Elmer, the memory machine
Exploring symbiotic relationships with your microchip
implant
Victor Permild
Interaction Design
Master’s programnme (120 credits) 15 credits
Table of contents
Abstract 2
Acknowledgements 2
Introduction 3
Research area and scope 4
Research approach and method 4
Background/Context 5
Transhumanism 6
Grinders and Biohackers 7
Theory pt. I: Technology and Society 9
Identification And Authentication: The Context Of RFID 9 Something the user knows (Password-based systems) 10
Something the user has (Token-based systems) 10
Something the user is (Biometric-based systems) 10
Predecessors of RFID Implants 11
The Possibilities of RFID Implants 12
What Implants Have to Offer vs. Its Alternatives 14
Insertables vs. Portables 15
Insertables vs. Wearables 15
Insertables vs. Biometrics 16
In Criticism and Defense Of RFID Insertables 16
Theory pt. II: Design ideologies 18
Speculative design 18
Slow technology 19
Process: Design Experiments 21
Early explorations 21
Idea #1: Personalized objects 22
Idea #2: Pattern-based interaction (behavioural biometrics) 23
Back to the drawing board 24
Meet Elmer, the memory machine 25
Discussion 27
Conclusion 28
Abstract
In this paper, I explore the emerging field of voluntary implants as seen in the DIY biohacking scene. My work on such implants focuses specifically on implantable Radio frequency Identification capsules. With the approach of research through design, I have undergone an iterative process, combining research and prototyping methods to externalize insights and knowledge generated along the way, in an effort to bring shed light on the new ideas and design considerations that arise when we embed computer technology in our bodies. By challenging the status quo, and setting aside my
preconceptions through speculative design, my work has resulted in a working prototype, inspired by the ideology of slow technology. Elmer, the memory machine, is a device that enables the implantee to capture memories in point of time via their implants. Here user are can record and review moments of everyday life, merely through a timestamp — a design decision that contributes to the debate on topics like convenience, privacy, and the right to be human.
Acknowledgements
I would like to thank my friends and colleagues Nina, Jesper, Thomas and Christian for being the kind and supportive friends as they are, as well as for the invaluable knowledge they have contributed to my work with this project. I would also like to thank my supervisor, Clint, who must at times have been wondering what I have been up to, but has at all times been helpful and constructive. Lastly I a heartfelt thanks to the administrators and teachers involved with the Interaction Design Master’s programme at Malmö Högskola, who have been patient with me throughout the process. The making of this paper has at many times been distracted by misfortune in my private sphere. I am grateful for your understanding and the way leeway you have given me.
Introduction
All throughout history, and in all cultures around the world, humans have fantasized about transcending from the fleshy frame we are born into. From the tales of Hercules, the adventures told about comic book superheroes and seen consumer interests of video games. They all explore the urge that we have inside us to exceed human capability.
But interestingly, one could say that we already live a time where we as humans become increasingly better at overcoming our born-with limitations and our body’s vulnerability to wear and tear throughout life. This development is a product of a long line of scientific and technological advances, especially in the latter half of the 20th century onwards. Important factors of course include progress in our understanding human biology, medicine and treatments, but undoubtedly our advances are also owed to the pervasiveness of modern computers (McNamee & Edwards, 2006) . Computers have helped, and still helps, us do complex calculations in a matter of milliseconds, let us run through simulations worth several lifetimes of testing and have enabled us to measure, log, and store all types of information about the world we live in with precision down to the single bit. Thus it is no wonder that the idea of merging the cool, rigid qualities of computers with the human body has been fantasized about through works of science fiction, scientific debates and the public alike for the last several decades.
But the question of whether or not the the human body an appropriate place for a microchip is not as hypothetical a question as many people may think. As it turns out, one could argue that we already live in the time of cyborgs, only they do not look like Hollywood portrays them in the form of RoboCop or Terminators. Complex computational devices, like pacemakers, insulin pumps and cochlear implants are routinely implanted in humans every day (Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016; Bradley-Munn, & Michael, 2016). It is in the people, who has these smart technologies embedded under their skin, connected to and controlling various functions of the body. These are all devices that are designed to restore lost body functionality, and form a very intimate connections with the biology of the human body and the silicon of the technology. Such Implants shows promise of a future where the blind will be able to see and the deaf will be able to hear, the limb will be able to walk. The term of “cyborgs”, cybernetic organisms, is not a new one. It was coined by Clynes & Kline in 1960, in an essay exploring what it would take to modify the human body into prolonged space travel, and eventually, space living (Clynes, & Kline 1995). However, during the last two decades, the reality of cyborgs and the rise of cyborg culture has become ever more prominent. Cybernetic implants has a relatively long history within the field of medicine, where the first experiments dates back to the 1970’s (Bradley-Munn & Michael, 2016). Interestingly though, recent developments shows an increased practice of people voluntarily wanting to become cyborgs for non-medical reasons.
As a matter of fact I had a RFID chip implanted in my hand In March 2017, at a technology conference in Helsinki. I had only made superficial research on insertables beforehand, but had a quite solid understanding of RFID and NFC technology in itself. At the conference, I attended a speak on the subject of RFID implants presented by Hannes Sjöblad, a well-known figure within the biohacking community. Sjöblad had brought along Jowan Österlund, a biohacker with a background as a body modification artist, who has co-founded a company called Bio-Hax which serves the cause of promoting digital biohacking solutions. In my design work throughout this project, I have sought to explore what I had gotten myself into, and decided to test first hand, what possibilities lies in the future of RFID implants.
Research
area and scope
In this project I seek to explore the ramifications of people voluntarily having themselves implanted with microchips for non-medical reasons, and specifically I intend to turn the first sod in exploring what having individuals walking around with RFID chips in their hands, could mean for future society. One of my main goals from the beginning has been to question whether there is more to the
post-procedure life than the convenience factor. In doing this, I will cover and intertwine the theory and knowledge from the fields of transhumanism, cyborgs, biohackers, identification and
authentication technologies as well as and slow technology. As such my research question has come to take its form in asking:
What implications do the emergence of RFID implants bring, and how can we design for a richer, more symbiotic relationship between the implantee and the implants, beyond that of security authentications?
Research approach and method
To explore my research question I have made used of research through (RtD), a practical approach that draws on using sketching and prototyping processes to externalize ideas, and conduct research from the knowledge gained in such activities. My approach been to uncover problems and ask questions in regards to voluntary implants. My goal has been to come up with a design, thought for a possible future, in which I strive to illuminate the implications of the emergence of microchip implants in a multifaceted manner. That is not to say that my aim has been to create a ready-to-market product. Instead I have come up with a prototype that materialized ideas and findings that have been brought to my attention during my design work, and may act as a conversation piece for discussion and debate on this novel, peculiar topic. Because of the very same novelty I have found it rewarding approach this project through RtD as it “allows researchers to rely on designerly activities as a way of
approaching messy situations with unclear or even conflicting agendas” (Zimmerman, Stolterman, & Forlizzi, 2010, p. 310). Like, RtD is describes as a non-formal method of research without a specific way of documenting the insights obtained( Zimmerman et al. 2010). Also in the spirit of RtD, my process have been iterative, and has enabled me to gradually embed my insights in my design, which as stated, has eventually come to act as a vessel of information and topics for debate.
Background/Context
In 2004, Neil Harbisson, born with extreme color blindness, had an antenna implanted in his skull, which senses colors and translates these into sound pitches, enabling him to “hear” the colors around him. Having lived with this implant for some time, Harbisson not only started to dream in colors. He got so used to his implant, that he started to perceive colors in music and speech, to which he has stated that he feel he has extended his sensory apparatus, beyond human biological standards. Harbisson was initially not allowed to have his passport renewed because of the presence of electronic devices in his passport photo. After weeks of correspondence, the passport was finally accepted with the antenna included in the passport photo, which has later been marked a milestone in the emergence of cyborg rights. In 2010, Neil Harbisson co-founded the Cyborg Foundation, in response to the growing amount of emails and letters received from people around the world wanting to become cyborgs. The foundation promotes research, rights and development of projects related to extending and creating new senses and perceptions by applying cybernetic technology to the human body.
Avant-garde artist, cyborg activist and associate of Harbisson, Moon Ribas, had a chip implanted in her elbow in 2013. Through her smartphone, the implant is connected to a global system om seismographic sensors, that makes her sense whenever there is an earthquake somewhere on earth, via vibrations felt in her arm. In that sense, she reportedly feel directly connected to the geology of the whole planet. With the use of her seismic sense, Ribas has created generative dance pieces, where the choreography depends on earthquake activity (surpassing 1.0 on the Richter scale) during the performance. Thus, In her solo performance “Waiting for Earthquakes” she stands still until an earthquake is felt, and the intensity of the dancer's movements depend on the magnitude of each earthquake. If there are no earthquakes during the time of performance she will not dance. Like Harbisson, Ribas has reported that she feels she has developed a new sense to her sensory apparatus, and has also stated that she “[...] modified [her] body, to modify [her] mind” (Quartz.com, 2016).
Robert Spence damaged his eye at the age of 9, when he was playing with his grandfather’s shotgun in the field. Gradually, the condition of his eye worsened to a point where he had to have it removed and decided to use a ocular prosthesis instead. In 2008, he decided to replace his prosthesis with a
custom eyeball-shaped video camera, with a transmitter that sends real-time color video to a remote device (Warwick, 2016). Whether Spence is to be considered a cyborg or not is debatable, as the camera is not connected to the optic nerve. Thus, spence has not restored his vision, but can use to camera to record what is in his line of sight. The video of the current model is low in resolution, and can only record for a limited amount of time before it gets too hot. Likewise, the transmitter is rather weak. That being said, A better performing higher-resolution model is under development (Warwick, 2016). Coincidentally, both Spence and Harbisson, and their respective body modifications, colloquially goes under the name of “Eyeborg”.
These examples depict fascinating futuristic stories of certain individuals special backgrounds, but in order to understand how such project came to, we need to look into some of the various forces that pushes forth this subculture.
Transhumanism
A wide range of views fall under the label of transhumanism, and there does not seem to exist an absolutely agreed on definition of transhumanism. At present time it seems to be a movement based mostly in North America, although there are some adherents from the UK. Transhumanism can be considered an ideology, that seeks to evangelise its human-enhancing aims (McNamee & Edwards, 2006; Bostrom, 2005). Given that transhumanism covers a broad range of ideas, it is important to distinguish moderate conceptions with the strong ones.
Strong promoters of transhumanism see themselves engaged in a project, a school of thought, the purpose of which is to overcome the limits of human capability, although it is not clear whether this is the foundational claim or merely the central one (McNamee & Edwards, 2006; Bostrom, 2005). The limitations described — or, because the idea of labelling them as limitations is itself to take up a negative stance towards them, one could also choose to describe them simply as regular features of human nature — relate to the manipulation and enhancement of the human sensory system, tailor-made changes in appearance, improving intelligence and ways of learning, prolonging of expected lifespan and reduction of vulnerability to harm. Some even go as far as refusing to accept traditional human limitations such as death and disease, and other “imperfections” on the biological level (McNamee & Edwards, 2006). Within these circles, it is believed that this can be done by exploitation of various kinds of technology, including genetic engineering, cybernetics, computation as well as bio- and nanotechnology — all of which are common topics of discussion and debate in the community. Just as well, albeit less immediate, futurist topics including space migration, mind uploading and cryonic suspension are common fantasies of what in their view would constitute a better tomorrow.
In the more moderate circles of transhumanism, the overall agenda for the project is less extreme, although it still concerns the use of technology to enhance human characteristics — also when it comes to appearance, death and disease etc. However, in this less radical project, the aspiration is not necessarily to discard human nature or human genetic constitution, but merely use technology to augment where possible and where desired by the individual. Some transhumanists may simply regard their ideology as a way of upgrading their own life by their own code of what they regard as an upgrade. It may very well be, that the most vociferous part of the transhumanist community, are simply deep-dyed libertarians at the end of the day, and see it as a matter of free choice (McNamee & Edwards, 2006; Bostrom, 2005). In that case, transhumanism merely supplies an overt technological dimension to libertarianism: If a given advance in technologically driven enhancement becomes possible, proficient adult consumers should not be restrained from receiving it, should they desire it. For this group, the worth of transhumanism is in its connection with their own conception of what is good for them, with the extension of their personal life choices. Other transhumanists may not see the transhumanism project not so much bound to the extension human capability and characteristics, as one that has the potential to better the human conditions of living in general. For this group, the relationship between transhumanism and the general, greater good is what makes transhumanism worthy backing (McNamee & Edwards, 2006).
Grinders and Biohackers
While the examples above are undoubtedly interesting, the technology they make use of and their setups are not widespread yet. On the contrary, a particularly notable recent development is found in the so-called “grinder movement”. Grinders are a type of biohacking community that applies the hacker ethic (eg. sharing, openness and decentralization) to manipulate the potential of their own bodies with Do-It-Yourself (DIY) cybernetic devices (Ahteensuu & Blockus, 2016). They are generally found to identify with open-source transhumanism, and techno-progressivism. According to biohack.me, a website that presents themselves as a virtual home for grinder around the world, the grinder mission statement is as follows: “Grinders are passionate individuals who believe the tools
and knowledge of science belong to everyone. Grinders practice functional (sometimes extreme) body modification in an effort to improve the human condition. We hack ourselves with electronic hardware to extend and improve human capacities. Grinders believe in action, our bodies the experiment.”
(Biohack.me, 2017).
The Grinder movement has strong ties to the body modification movement and they engage in actual implementation of cybernetic devices in organic bodies, as means of approaching a transhumanist future, by hacking, designing and installing body-enhancing implants for human use. Similarly to the rise of the maker movement, biohacking emerged from a growing trend of non-institutional science and technology development, helped along by a democratization of hitherto expert-only, expensive
technologies seen since the 2000s (Ahteensuu & Blockus, 2016). Industrial production methods such as 3D-printing, laser-cutting and the use of Computer Numeric Control (CNC) tools has become ever more affordable, thus increasingly available to the public, and conjunctively Open-source hardware frameworks like Arduino have facilitated DIY computer projects. Technologies that used to only sit in high-tech laboratory equipment is suddenly available having at home, in your garage, student dorm or at public libraries or makerspaces. In other words, these people are not scientists or researchers, and that is an important distinction to make. The grinder movement is distanced from university research institutions or corporate interests. It is a third force, a band of citizen scientists and DIY makers striving to explore and understand the new uses of the technology (Ahteensuu & Blockus, 2016).
As such, hackers and hobbyists are now augmenting their bodies in new ways by voluntarily inserting non-medical devices. Especially popular are the small semi-permanent insertables like neodymium magnets, RFID (Radio Frequency IDentification) or NFC (Near Field Communication, a type of shorter range RFID technology) chips (Heffernan, Vetere, Britton, Semaan & Schiphorst, 2016; Bradley-Munn & Michael,, 2016). The implants being semi-permanent means that the device can potentially stay in as long as the user desires, but if wanted, it can also be surgically removed without notable consequences other than leaving a scar. Magnet implants, usually placed near the nerve endings of the fingertips, vibrates when they are in range of electromagnetic fields, and allow the implantee to sense these fields. Furthermore, the magnet makes it possible for the user to pick up small magnetic objects, as well as sensing if a electricity is running through wire or not. RFID and NFC chips, usually implanted in the hands too, can be used as keys in digital authorization processes through an unique ID number on the chip. In 2005, Amal Graafstra had an RFID chip inserted an into his hand with the aid of a surgeon friend (Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016; Bradley-Munn, & Michael, 2016). At the time, he was working as an IT consultant for a group of medical clinics, and decided to get “chipped” because he felt his keyring was ever only increasing in size, and because he was often carrying heavy computer equipment through a door with an automated lock at work. With his chip, he was able to identify himself digitally without the use of a key or card, and his chip could be reused for other security systems, gradually diminishing the size of his keyring. Graafstra’s work gained traction online, and is widely acknowledged for pushing forward the bio-hacker and grinder movement. In 2013, Graafstra founded the startup and website dangerousthings.com, and started to sell Do-It-Yourself implants made for humans, along with sterilized peripherals used to insert them. Insertables can be self-fitted or inserted by medical professionals or most commonly, qualified body- modification artists (Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016; Bradley-Munn & Michael. 2016). While it is hard to say just how many people have undergone procedure, RFID (and its cousin NFC) chips are the most prevalent both in numbers and in public debate. In 2016, Dangerousthings.com had sold over 10.000 implantable units (Supply Chain Digest, 2016), and a facebook group by the name of “RFID Implantees”, which is moderated by Graafstra has over 2400 members (Facebook, 2017).
Understandably, one might argue that implantable RFID chips are not that new of a technology. After all, chips have been used to identify pets (and later, livestock) since the 1990s (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016). So much so, that Microchipping is common, a legal requirement in many states and countries that assists in the identification and management of stray animals. This practice has been widely adopted with no sound evidence of harm. But what makes exactly the emergence of human chip implants particularly interesting at this point, is the rapid development of the internet of things, where market analyses forecasts of 20-30 billion connected devices by the time of 2020 (Forbes.com, 2016; Gartner.com, 2017). With an implant, the human body is admitted to the sphere of interconnected devices, and is granted a way to “talk” together with non-human agents in a common language or protocol. Today, hackers are now using RFID implants to access their homes, computers, phones, unlock and starting their vehicles. They arrange “implant parties” where they invite people to join the movement by having an implant done, and get to know the community (Heffernan, Vetere, & Chang, 2016; Bradley-Munn, & Michael, 2016). Voluntary non-medical implants are by no means a mainstream practice as of yet, but the topic has made it to mainstream media and the public discussion. Thus, the subject is to be considered interesting and worthy of debate in order to understand what the near future of non-fiction cyborgs may hold.
Theory pt. I: Technology and Society
Identification And Authentication: The Context Of RFID
Information and communication technologies, and especially the internet, has brought upon an ever increasing digitalization of information and a time of always-on services, that can be accessed at any time, regardless of geographical location.In making sure that such services are maintained with appropriate levels of security and privacy, there has been a growing need for identification and authentication (I&A) processes to prevent attempts of unauthorized access of these digital systems. Identification refers to the means by which an individual provides a claimed identity to a system, and through an authentication process, the user’s identity is verified (Rotter, Daskala, & Compano, 2008) . In other words, authentication ensures that a person is who they claim to be. The most common methods of authentication can be clustered into three main categories. In practice, these three methods are either used by themselves (one-factor authentication) or in combination (multi-factor authentication) to provide stronger, more reliable proof of authentication.
Something the user knows (Password-based systems)
This method refers to the use of secrets passwords and Personal Identification Numbers (PINs), and is widespread because of its simplicity of use and relatively low maintenance costs. However, weaknesses of this method include the risk of others obtaining and misusing this knowledge, with or without the user’s consent (Rotter, Daskala, & Compano, 2008) . This may happen either as user’s share passwords or manage them in an exposed manner, or as culprits resort to phishing, cracking or eavesdropping — be it physically or digitally.
Something the user has
(Token-based systems)In many ways similar to its password-based counterpart, token-based systems are quick and convenient, and generally easy to use. Tokens such as smartcards or -keys, usually personal and meant as non-transferable, can be thought of as physical representations of an individual’s passphrase or PIN ( Rotter, Daskala, & Compano, 2008) . However, the need for a physical medium brings about higher acquisition and maintenance costs, than that of password-based systems.Similarly to password-based systems, tokens may be lost and end up in the wrong hands. That being said, users might not always be aware that someone else knows their password until it’s already too late. Though, If a token is lost, the user is arguably more likely to notice because a physical object, and its access-giving functionality, is suddenly missing. Furthermore, tokens are often checked together with the keyholder’s physical appearance, preventing misuse further. This bring us to the last type of authentication.
Something the user is
(Biometric-based systems)Biometric technologies makes use of measureable physical traits to authenticate its users ( Rotter, Daskala & Compano, 2008) . Here we can distinguish between two types of biometrics: physical and behavioral. The former approach is the most common, and refers to authentication through fingerprint or iris scans, facial recognition. The most well-known example is probably the TouchID placed in Apple products since the iPhone 5s came out in 2013. A rarer, and less explored part of biometrics are those that deal with behaviour. Behavioral biometrics concerns they way a user performs a task (Moskovitch, R. et al. 2009). Analog examples might include comparing hand-writing or personal signatures. An example of digital behavioral biometrics could be a device measuring not only if the user types the password correct, but also if types it in the correct rhythm. Likewise, a advanced behavioral biometric algorithms could potentially be able to discern if a person using a computer was its rightful owner determined on work patterns like the way they type, erase, click and make use keyboard shortcuts (Moskovitch, R. et al. 2009). In theory, well-implemented biometrics can be considered a reliable method of authentication, but in practicality this is not always the case. Physical
biometric systems are often bulky and more fragile than its RFID counterparts, all the while being more expensive to purchase, setup and maintain (Rotter, Daskala, & Compano, 2008) . When it comes to behavioural biometrics there is a trade-off between simple and complex systems. The simpler the system is, the easier the behavior of a person is to mimic. As systems are made more complex, they also become more secure, but this usually requires vast amount of user data to make a person’s digital idiosyncrasies discernable (Moskovitch, R. et al. 2009).
Compared to its counterparts, biometric systems also faces some issues in terms of social acceptance. As a result, these types of systems have higher barriers of broadening its deployment. Though, with the emergence of implants, a new possibility in the use of biometrics appears. Having a digitally identifiable device embedded in your body, makes up for many of the disadvantages of the two other types of biometrics. Some even argue implants could be the best of the each approach combined. That is, the reading equipment and success rate of readings becomes the same of tokens. All the while, they require little to no maintenance, and the user can not lose their device ( Rotter, Daskala, & Compano, 2008).
Predecessors of RFID Implants
Radio Frequency Identification (RFID) technology was originally developed to for automatic identification of physical objects, with so called “tags” attached on them. The RFID tags are small, passive (ie. batteries are not needed for them to operate) devices, which emits identification signals through radio waves in response to inquiries made by an RFID reader, when it is within its reading range (Frith, J. 2015). The information sent from the tag is then further processed in a computer on the reader’s end. RFID technologies are already seen employed as replacements for barcode, but unlike its predecessor, RFID tags do not require clear line-of-sight for its readings. This means multiple scannings can occur at the same time, which opens of possibilities for the technology to be used for tracking of inventory status, self-checkout in stores, and automation of countless of other industrial procedures. Besides identification, it is possible for the tags to contain additional information about the products they are attached to, eg. storing conditions, expiry date, optimizing production and logistics chains of enterprises. In general, Industry and governments are both strong backers of RFID technology.
RFID technology makes a suitable choice for I&A processes, because of its relatively low cost and maintenance, and its use today is widespread especially in the form of smart cards or -keys (or as token in the keyring). Today, a wide array of RFID/NFC wearables like rings and bracelets are also available online. Likewise, RFID chips are already deployed in passports of all member countries of the EU and the U.S., amongst others, and more countries are to follow. For most countries, these chips hold the biometric data that is already available in written form in the passport, but in the U.S., fingerprints and iris scans may also be stored for use later.
The Possibilities of RFID Implants
In 1998, Kevin Warwick, who at the time was Professor of Cybernetics at The University of Reading, became the first person to have an RFID chip implanted. He used the chip to control lights and open doors in his office buildings, and programmed the system to greet him when entering the front door (Warwick, 2016). It was found that implants of this kind, could potentially be used in wide array of I&A scenarios, potentially verifying or substituting use of credit cards, car keys or passports (as is already the case in some types of animals). In 2004, the U.S. Food and Drug Administration approved the world’s first human RFID implant, the VeriChip (later known as PositiveID). The VeriChip was readable at a distance of up to 10-15cm. and stores nothing but an ID, long enough to uniquely identify everybody in the world. Other data related to the implantee was not stored in the chip itself, but in a centralized database. The VeriChip was notably larger than today’s implants, allowing room for a bigger antenna and thus, a larger reading range. The chip was put in test in the medicine industry, where it would help doctors retrieve medical records on patients. During its lifetime, over 2,000 VeriChips were sold and 900 medical facilities equipped to read them (Heffernan, K. J., Vetere, F., & Chang, S. (2016, May). The launch proved itself promising, especially in cases where patients were not to come in contact with, eg. unconscious or suffering from Alzheimer's disease. Also in 2004, the Mexican Attorney General's office had 160 employees in the organized crime division chipped, giving them access to restricted areas ( Rotter, Daskala, & Compano, 2008; Heffernan, Vetere, & Chang, 2016). Same year, VeriChip announced a partnership with gun maker FN Manufacturing to produce an RFID-embedded police gun with an RFID, that could not be fired, should it fall into the wrong hands. In theory, smart guns promise a safer future of having a gun in the home, but a criticism still present today, is the worry that the gun malfunctions in emergency situations, rendering the gun useless. Furthermore, Some hundred staff and patrons of the now-defunct Barcelona Baja Beach Club VIP program had implants done for access, payment and special offers (Heffernan, Vetere, & Chang, 2016). However, after a series of bad publicity, including conspiracy theories and dubious promises to its stakeholders, VeriChip was discontinued its implants until further notice in 2010 (CBS News, 2010). Since VeriChip ceased their implant operations, Amal Graafstra has been developing smart gun prototypes to work with his implant products. These guns are not commercially available as of yet, however.
Today, many variations of RFID implants exists, not many papers specify which ones they are talking about. In general, it is a real challenge mapping out the precise technical descriptions of each chip as they vary from model to model. What can be said however, is that the latest versions of the RFID (NFC) chips serves even more than just being a digital identifier device. It is more of a tiny implantable computer capable of doing very simple computations and storing information on the chip.
The common RFID implants are the size of a grain of rice, and function as passive tags, which again means that they do not need batteries to operate. Instead, they make use of the electromagnetic field emitted by an external RFID Reader (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016). Due its small size and lack of power source, the chip requires very little maintenance once implanted, but is also limited in terms of memory and communication range. The common RFID implant is re-writeable, but usually have a memory of a little less than 1 kB, which is indeed not a lot compared to most modern electronics. Yet this amount of memory is still enough to store a unique ID, and up to several user-chosen numbers, strings of text or URL’s. The devices are encryptable, and are only readable within a at very close ranges, from around 1-3 cm, depending on the reader (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016). The reader is not able to tell how far away the tag is — it is either within range or not, on or off. With all its hardware limitations, it becomes difficult to design for interoperation with other wireless technologies like Bluetooth and GPS. However, just like its short range, this limitation could also be seen a good thing from a security and privacy perspective. For instance, contrary to what many people may believe, it is not possible to locate an implantee in real time, although use of the chip can of course leave digital traces of the user's whereabouts at a given moment of interaction.The chip is most commonly implanted in the hand, usually in the webbing between the thumb and index finger, but it can also be done in the fingertips. Other examples of implantation sites include arms or between the shoulder blades (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016).
Potentially, implants can be used for all I&A processes built on RFID technology. This is why the most common examples of today’s use are grinders using their implants to access their electronic devices, vehicles, homes, storages and offices (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016). Other uses include monetary transactions, or as links to digital wallets (eg. bitcoin wallets), general contact information, links to online CVs, portfolios or websites, or web app commands also through the use of URLs. The main issue is to have the administrator of a given system read the implant and make the computer append its information with the personal information of the implantee. At this point, the implantee must repeat this process for each system they wish to use the implant for, as there is no centralized database of implant identifications and who they belong to. If the implantee themselves are the administrators of the system, this process requires little to no effort other than technical know-how. In the spirit of hacker culture, many grinders decide to design their own systems, often helped along by the rest of the community in maker spaces or online.
In recent years Sweden has especially seen a rise in the interest of implantables. In 2015, Epicenter, a high tech office block in Stockholm made headlines when it was reported that it was granting its employees the option to have an RFID chip implanted. Here, several implant parties have been hosted, and today more than 150 employees out of a total some 2000 workers have been implanted.
In the building, the implant can be used to open doors, use printers and buy food in the canteen (Bradley-Munn & Michael, 2016; Independent, 2017a). Belgian company NewFusion have also adopted this practice, and also use their implants to access personal dashboard and add songs to their collective Spotify Playlist. In 2017, the swedish state-operated rail company SJ started offering passengers the option to use their RFID implants as travel cards, and reactions have been largely positive. SJ has said they expect about 200 people to take up the microchip method. About 2,000 Swedes in total are estimated to have had the surgical implant to date, the majority of them employed in the tech industry The Independent. (2017a, 2017b).
What Implants Have to Offer vs. Its Alternatives
While implanting chips in a person only to prove their identity may seem a bit farfetched, it is actually not that unexplainable, as the course of Moore’s law still leads digital devices have become smaller and more powerful. Mobile devices have progressed from portables, to wearables, to insertables, digital devices that go through or under the skin, or inside a person. The term insertables refers to devices that can contained within the boundaries of the human body, including devices that can be inserted and removed in openings in the orifices of the body. As such, RFID implants falls into the category of insertables (Rotter, Daskala & Compano, 2008; Heffernan, Vetere, Britton, Semaan, & Schiphorst, 2016). Throughout history we have seen similar developments in our artifacts. In the example of optometry, people would use to carry portables such as vials of water or clear gems for magnification. Later, with the invention of spectacles, the technology became wearable, and today we are able to craft contact lenses tailored to compensate for the individual’s visual impairment. Likewise, in the case of otology, we have transitioned from portable ear trumpets to wearable hearing aids, to cochlear implants. As such, some people might simply consider this the next frontier of I&A technologies, and consequently they buy into the promises of the technology being better (Heffernan, Vetere, F. & Chang, 2016). However, just because implants constitute the supposed next step for technology, there are many use cases of technology in which portables and wearables are still widespread, as these three methods of carrying technology all have their advantages and shortcomings compared to each other.
In the following section I will compare the pros and cons of each of these three approaches together with the option of “sans-insertable” biometrics. I will only be focusing on ways to carry passive antenna tags such as RFID and NFC chips. Be aware, that this assessment would look a whole lot different if the devices were battery-driven, which I will get back to at the end of the comparison.
Insertables vs. Portables
Portables refer to devices that can be carried by a user, but not worn like a wearable. Examples include smart cards and -keys, as well as other kinds of tokens. One of the most common problems with portables are the tendency, for the owner to unintentionally leaving them behind. This is an issue, not only because it puts the user in a position where they can not gain entry to areas, they have to right to access, but also because of the risk of the portable getting untraceably lost or stolen. Whether lost or stolen, such scenario, comprises the security of a system or building (Heffernan, Vetere, F. & Chang, 2016; Rotter, Daskala & Compano, 2008). Another potential issue is when users borrow RFID tokens to each other. In such cases, tokens can be misused by people the user thought they could trust, or wrong data entries can be fed to systems where users and their whereabouts and doings are of importance (eg. in secure facilities like power plants and military armories). All of the problems above are virtually non-existent with insertables. They are not forgotten, and can not be borrowed or stolen, at least not without the implantee being present eg. by coercion or threats — which is no less of an issue in the case of portables or wearables either, ie. threats are problem none of the approaches are guarded against. Portable RFID Devices are potentially invisible, meaning they can usually be carried in clothing, however unlike their implantable counterparts, they will always take up some kind of space (Heffernan, Vetere, F. & Chang, 2016; Rotter, Daskala & Compano, 2008). RFID token can have a clunky feel to them, and the thin and light they get, the more vulnerable they are to wear and tear and eventually breakage. Insertable RFID chips are much more sturdy and protected human body tissue, and impacts strong enough to damage the chip, will harm or crush the hand anyways.
Insertables vs. Wearables
Wearables are electronic devices that can be worn on the body, such as smartwatches, -wristbands and -rings. While a lot of the things said about portables also apply to wearables, there are some important distinctions to make. Wearables, are not as easily left behind or forgotten, simply because they are readily worn most of the time. This also make them harder to steal, and more cumbersome to borrow to someone else. However, because they are worn on the body, wearables are more likely to be scrutinized as fashion accessories and thus a part of a individuals’s look and self-image (Gemperle, Kasabach, Stivoric, Bauer & Martin, 1998). Among other things, they must allow for movability and not appear clunky or heavy. Likewise, wearables like smart rings and -bracelets must be flexible in their sizing or simply come in various sizes. If a carrier feels uncomfortable wearing the device, or does not like the look of it, they are likely to take it off when not in use or carry it unattached to the body, in which case we are presented with the problems of portable devices mentioned above. If done right, however, wearables do have the blend in and synergize with the user’s sense of fashion,
but even given just the few issues mentioned here, it is clear that many options for customization are often required for such a thing to happen.
Insertables vs. Biometrics
Another valid alternative to insertables is traditional biometric technology, such as fingerprint or iris scans and the like. After all, we already carry our genetic traits with us everywhere we go, and biometric readers are indeed quite common. But first off, it is important to note, that equipment to process such tasks are considerably more expensive than RFID Readers. Likewise, they are more bulky, and more sensitive to dirt or damage than its alternative. Furthermore, even modern biometric readers are more prone to misreadings, and the fact that the biological traits of a human person can change slightly over time only make matters more problematic (Heffernan, Vetere, F. & Chang, 2016; Rotter, Daskala & Compano, 2008). Biometric I&A also suffer from a lower acceptance rate, as users have been observed to be more hesitant to whom they hand out their fingerprints out to. In the same vein, the activity of handing out fingerprints have a bit of a social stigma that used to only relate to suspects of criminal activity. Eventually, all biometric data boils down to a series of numbers for the computer to interpret (Rotter, Daskala & Compano, 2008). A valid critique of biometric-dependant systems here is that they potentially puts the users at the risk of having their information hacked, without being able to reset their information. That is, if the numbers end up in the wrong hands, it is extremely difficult to resecure the system and still let victims use their biometric data as access validations. While insertables (as well as portables and wearables for that matter) can also be hacked, it is still possible to replace a compromised unit with a new one.
In Criticism and Defense Of RFID Insertables
Most people are hesitant towards the idea of implantation, likely because it seem more permanent of a solution compared to other approaches. Of course, having a wireless chip in the body implant also raises some privacy and security concerns. It should be known, that like all other digital devices, implants can also be hacked, but one must keep in mind that this also applies to its alternatives. However, one of the strengths of implants can also turn out be a shortcoming. It is harder to distance an implanted device from a user in the case of a security breach, compared to portables and wearables. Though, as mentioned, unlike the case of compromised biometric-based systems, it is not impossible replace an implant (Heffernan, Vetere, F. & Chang, 2016; Rotter, Daskala & Compano, 2008). Furthermore, modern implants are encryptable — most smart cards are not — and can be protected with a password. Implants are also harder to for culprits to manipulate or dupe, due to its short range. As mentioned, there is also a myth that RFID can track users whereabouts globally in a GPS-like manner. As we know the chip can only be activated within a few centimeters, this is technologically impossible, unless the reader is connected to a system in which a GPS is also
present. A common and valid response to the “uberveillance” questions of RFID implants is that if one already owns a smartphone, they are already facing much bigger privacy concerns in their daily life. People tend to store highly personal information on their phones, are logged in real time through location-based services and download free bloatware apps that taps into questionable many of the phone’s settings.
Perhaps the most vociferous opponents of RFID implants are a subculture of highly religious Christian activists, who have massively condemned the microchip as “The Mark of the Beast”, prophesied to be a future requirement for buying and selling, and a key element of the Book of Revelation
Heffernan, Vetere, & Chang, 2015). It should be known, that this is not the first time in history, a new technology has been called that, however. As a side note, these kind of people, alongside other communities of conspiratorial theorists makes makes very cumbersome to search for knowledge on the topic of implants, without being flooded with misinformation. Most of these myths are debunked above, but there are still some concerns that cannot be dismissed just as of yet. While it can both be seen as a good and a bad thing, the implant approach does mean a shorter reading range which potentially inconvenient maneuverability of the implant site in order for the chip to read. Furthermore, a consistent worry seems to be putting the user’s health at risk by having an implant done (Heffernan, Vetere, F. & Chang, 2016; Rotter, Daskala & Compano, 2008).. First off, there is a risk of infection at the site of implantation (and if untreated, blood poisoning), but this is also why sites like dangerousthings.com recommends having professional surgeons or body modification artists do it for you. Also, a recurrent concern is the worry that the chip may cause cancer.
However, from what we know with use in pets (and later humans) there has yet to be reported any cases where implants have been provenly linked to the development of cancer.
Still, human implantation is indeed a quite recent technological venture, and it would be too hasty to dismiss the risk just as of yet. Lastly, just like all other technologies RFID implants have the risk of getting outdated, which does raise an noteworthy call for sustainability in implants for the future.
Theory pt. II: Design ideologies
Speculative design
In my aim to explore the implications surrounding The topic of DIY Biohacking and microchip implants, I have found it beneficial to position myself within the realm of Speculative Design as coined Dunne and Raby (2013). One of the main reasons to this, is of course that we seem to be interested in enlightening ourselves what the world will begin to look like when cyborgs are walking among us. Here, Speculative Design brings a type perspectival aid to prepare ourselves of how things may or may not play out. However, this is not to say that this mental activity is necessarily an exercise of being right or wrong in predictions, but rather to prepare for eventual shifts in the status quo (Dunne & Raby, 2013). Rather, Speculative design uses design methods and proposals to manifest ideas that spark debate, discussion and reflection upon alternative ways society could take form. In contrast to affirmative, problem-solving, design ideas, we care not as much about how a design would perform on the market or whether it would sell. In Speculative Design, current state of affairs are challenged, and
in doing one is permitted to ask hypothetical “what if” questions, to inspire and encourage our
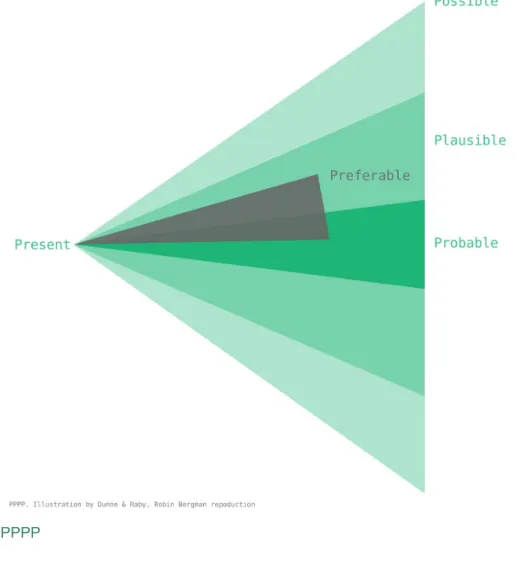
collective imagination. Thus, Speculative design and RtD goes well in hand. Figure 1 shows a tool for understanding the scope of the potential types of future scenarios Dunne & Raby cover, where each cone represented different levels of likelihood. b All parts of this illustration plays its part in
understanding the greater picture, but as we move closer to cone’s center, we find ourselves in situations than are increasingly likely to happen. However, this is not to say that this mental activity is necessarily a game of being right or wrong in predictions, but rather to prepare for eventual shifts in the status relative to their prospects.
If we start off in the broadest field of possible futures, we find ourselves in space of almost free imagination, where our only limits seem to be that which is (yet) physically impossible to create (eg. perpetual motion and precognition). Possible futures covers events and developments that could indeed happen, but most likely will not. The next cone describes plausible futures. Imagining ideas in this field, we can mentally prepare ourselves for conceivable transformations in society, that could actually happen. Next we we find probable futures, which is the most common for conventional design to take place in, and where most designers find themselves working, as it refers to future
developments and trends we almost anticipate happening, unless we experience some great disruption in society.
Then, if we take half a step back, in between probable and plausible futures, Dunne and Raby notes a fourth design space they find particularly fruitful for developing and exploring scenarios alternative to the probable, which gives us a chance to make them palpable and debatable before they arise. This requires its participants to temporarily suspend their skepticism, forget how things are right now, let their imaginations wander. By creating such fictional future narratives, designers need not adhere to current norms and tendencies, but are free to use design as a tool explore social and ethical issues that may arise eg. with the emergence of new technologies such as microchip implants. In their own words: “We believe that by speculating more, at all levels of society, and exploring alternative scenarios, reality will become more malleable and, although the future cannot be predicted, we can help set in place today factors that will increase the probability of more desirable futures happening. And equally, factors that may lead to undesirable futures can be spotted early on and addressed or at least limited.” (Dunne and Raby, p. 6, 2013).
Slow technology
The Slow Technology (ST) approach, as described by Hallnäs & Redström (2001), seeks to underline how technology can support reflective use, rather than only fast-paced, efficiency-based use. Within the design philosophy of ST, a key issue is that we should embrace slowness in learning,
objects should in and of itself be time consuming, but rather but time productive: that it enables us time for new reflective activities.
ST stands in contrast to what Hallnäs & Redström describes as fast technology. In the time personal computers have increasingly become a more and more pervasive part of our everyday life, the measures of what constitutes good design has often been characterised in terms of ease of use, easy to learn, effectiveness, as well as immediate ‘‘visible’’ results, and the like. As such, fast technology can be described as: “efficiency in functionality with respect to a well-defined task” (Hallnäs & Redström, p. 203, 2001). The aim here is to take away time in completing a task, as well as decreasing the ascent of the learning curve of the product through which this task in done. Through promoting slower and/or less extreme interaction with the technologies around us, ST intends to restrain some of the potentially damaging effects of excessive technologies in our everyday life. It is part of a broader cultural agenda, which generally promotes living life at a slower pace. The authors see a need actively to promote moments of mental rest and time for reflection in an ever hastily changing environment, and explores way to alter how humans consume technologies,
including mobile devices, social media and other modern innovations that tend to consume a lot of our time, and a worst can become addictive.
Of the ways this ideology may be utilized, I have found one especially interesting. Hallnäs & Redström talks of the kind of technologies that focuses on the presence of time, where slowness of appearance and presence is simply an inherent part of the design for reasons beyond aesthetics and functionality alone, and where time is a principal, clear-cut conception: “If slowness comes as a result of the
concentration on aesthetics, it might well be that the given thing at the same time is an effective tool, i.e. slowness comes from reflection on aesthetical aspects and changing perspective but we use the same thing to accomplish a given task efficiently.” Hallnäs & Redström (p. 204, 2001).
An example is that of a wrist watch, which invites us to reflect on how the technology is slow in appearance, but also effectively accomplishes the task of giving us the time at a given moment. We change mode of interaction as we switch back and forth between slow and fast use of such technologies, and it is perfectly acceptable that a piece of ST can somehow correlate with some definitions of functionality. Within the programme of ST, Hallnäs & Redström distinguish between three perspectives: Reflective technologies, Time technologies and Amplified environments, of which I have worked with the two first. Each aspect constitutes a specific design theme within the broader approach of ST. Reflective technologies describes designs that in its fundamental expression invites for reflective use. It is a type of technology that could be considered awkward if it what used without reflection, i.e. in the case the user treats it as a conventional efficiency-based tool. Time technologies concerns the design of technologies that augments the presence of time, rather than diminishing it. This should not be misinterpreted as technologies that are tedious or time consuming, but rather an inspiration for us to design in a way that seems to extend and unfold time, in an effort to slow things down. Through true use, such technologies uncover a slow expression of time in present.
Process: Design Experiments
Early explorations
As demonstrated above, my first course of action was to do a lot of desktop research on the subjects of insertables, biohacking and grinding. Meanwhile, I acquired a substantial overview of the various uses of RFID implants, past as well as present, the majority of which, already disseminated in this paper. Furthermore I conducted an improvised Interview with both Hannes Sjöblad and Jowan Österlund when I had the implant done, in order to get some answers to some of the questions which first comes to mind regarding the topic. Most of the questions I had are answered earlier in this paper, and reinforced by research. One important takeaway I got from this this interview however, was the recommendation to not write any data on the chip, that was so important that you could not wear the same information printed on a t-shirt you could wear in public. This is to be understood as an extra safety measure, so that even if other people would unbeknownst to you manage to access your chip data, it would not be life-destroying.
Figure 2: Arduino/RFID reader setup
I then started exploring the possibilities of interfacing with the device in my hand. I was able to upload a command-like URL to my implant, that when read on a smartphone, would open up MobilePay, an application for danish credit payments, and request a payment of 50DKK (equivalent of €6.72). My idea was that this could be used as party trick that I could show off to my peers. At the same time,
having the amount set at 50DKK ended up being handy at other times eg. when paying for my co-students lunch, which would often be around that price. Soon I started experiencing problems with this configuration. First off, the majority of in my social sphere have iPhones, myself included. While iPhones do contain the technology to communicate with RFID devices, they have not made it explicitly possible for developers to tinker with just as of yet. But my goal was not to interface with services already existing anway. I strived to contribute with new knowledge and design explorations.
Seeing as my own phone can not read my implant, I restored to building my own reader in the Arduino IDE, which allowed me to explore some rudimentary interaction possibilities (Figure 2).
Idea #1: Personalized objects
Figure 3: Sketch for the idea of personalized objects
One of the first ideas i sought to explore was a way to let everyday objects know who was using them through identifying the microchip implant, and adapt their settings appropriately to needs and wants specified by the user. For instance cooking devices would be able to make coffee or toast bread just to the users taste. In the home, light settings or music playlists could be set to the user’s preferences, maybe taking the time of day into account also. In such a world, microchip implants could also be
used at office spaces where work desktops where often switched between workers, eg. at an office hotel, where moving from desk to desk would be easier because she chip would store your ideal work setting in terms of software installs, lighting etc.
Yet I found several complications with this idea as soon as I started scratching the surface a little bit. First off, to make this work all devices would somehow have to be compatible with RFID tags, either by having a reader in them or be “smart device” connected the internet — a trend that I had no intention of reinforcing, unless there is good reason. Meanwhile, I slowly lost interest in this idea as I started to find it was pretty similar to opening doors and vehicles, only here I would be working with home appliances. Lastly, I found the idea to be a little too uninspiring, and not that far from what is already being made, which caused me to eventually shelf this concept.
Idea #2: Pattern-based interaction (behavioural biometrics)
Figure 4: Sketch for the idea of pattern-based interaction with an RFID reader
I also tried experimenting with technologically repurposing the way an RFID reader works. As described earlier, RFID readers are not able to sense distance to a nearby tag, but only whether at tag is within range or not. Yet, this trait can still bring about interesting interaction possibilities. For instance, in the thought of behavioural biometrics, I thought I could be interesting if I could somehow measure a sequence of readings as an input pattern, and handle this as an inquiry for the computer give an output corresponding a given pattern. Here, I ran into two problems. Firstly, while getting the reader to read an RFID token was not that much of an issue, getting it to read my tag was another
story. The power and range of the reader I have used for my Arduino is not as great as in the out-of-the-box products currently on the market. This did not keep my from testing out my idea however, but for the most time I resorted to using a RFID token, rather than my implants, because of the greater read range of the former. Then, I ran into a problem that I was not able to fix. As it turns out, in all the RFID libraries I tested out, there was a fundamental piece of code that kept the reader from continuously reading a tag without returning a “0” every other reading, instead of the tags ID number. While I still think this idea is interesting, I did not find it to be worthwhile trying to overcome this obstacle.
Back to the drawing board
While I made some important findings, and was able to outrule certain design opening from explore the ideas above, I felt like I needed a new shot of inspiration in order to push my project onwards. As such, I decided to conduct a semi-structured interview with two good friends, who also had a chip implanted at the same conference I had mine done. The point of the interview was primarily to gain new inspiration and insights of use, and not necessarily to talk user-friendliness and desired products, although the conversation did touch upon that from time to time. In the nature of semi-structured interviews, I prepared some questions that I would like my fellow implantees’ opinion on, but as the interview went on, I was very open to let the topic of discussion flow freely in directions I had not thought of myself. During the interview, there was especially one use case was unveiled, that happened to stick with me: to use the implant to write notes to oneself, in this particular case, where one would park their bike in town before a night out. As such the implant would, until overwritten, become a tiny little time capsule of information, a message to future self about the whereabouts of one’s bicycle, should they forget during the night. In this case, the message consisted of a rebus made from emojis, which gave the implantee a clue to the location of the bike, although we also talked of writing simple text or a geotag on the chip.
Following the interview, I went back to the drawing board and couldn’t let go of this idea. For quite some time at this point, I had a feeling there was some special, yet uncovered about RFID Implants. Almost since the beginning of my work, I had sought to think beyond the I&A functionality of the chip, now I finally felt I had an idea connecting my research and finding, as well as tying into the school of transhumanism and the practice of biohacking. An idea that seemed to afford synergy between the human body and the microchip in a way that felt richer than accessing building or vehicles.
What I found so interesting was the narrative that in my body, I now have a small digital brain. Its memory might not be very big, and in itself it may not be very smart. But it is digital, and besides its ability to communicate with RFID readers it can store digital memory — both describing traits I (or any other human being) was born with.
Meet Elmer, the memory machine
At its core Elmer is a type of memory device, that stores memories generated over time by a user who is implanted with an RFID microchip in their hand. The use of Elmer reminisces back to a time where people would tie a string around their index finger, or draw a cross on their hand to assist them remember something they would not want to forget, for instance an important letter to be sent before the day was over. In contrast to the way we make notes to ourselves today on our phones or
computers, these types of tools for recall does not store any information, they are merely prompts.
Figure 5: Elmer, the memory machine. Note the points of interest, marked by numbers on the two bottom pictures. 1) Ultrasonic distance sensor, 2) Screen, 3) Instrument panel, 4) RFID reader, 5) Laser pointer, 6) Confirmation point light
In a similar fashion Elmer allows one to record memories and reassess memories, stored as
timestamps and displayed on a screen split in two (seen at point 2, in Figure 5). On the left-hand side of screen the user finds a data visualisation of the moments they recorded, along with the timestamp for each respective memory, written in text on the right-hand screen. It is up to the user what they want to record, and thus how they will use the device. It could be that the user wanted to record moments where they felt good, sleeping patterns, deadlines and the like. Because each memory is only delineated as simple timestamp, it is to be expected that the user will sometimes forget what they wanted to remember. However, in a world where we create more data than can ever be analysed (perhaps except with the aid of artificial intelligence), yet most of us can not even remember the phone numbers of our closest friends by heart, perhaps it is time we ask the question if we should start taking some of the memory load upon our own shoulders and train our minds to remember. As such, Elmer is designed to stimulate the user to remember, but also recognizes the right to forget.
By bringing your chip to reader in the top of the “tower” seen to left (point 4, Figure 5), Elmer fetches the memories (timestamps) stored on your implant and displays them chronologically on its screen. From here, the user is enabled to browse through their memories in various ways by turning the knob in the middle, seen to the right (point 3, Figure 5). First off, by pushing the knob, you can alternate between browsing by individual timestamps in order recall a certain memory, or by the day in order to see how you have recorded your memories as the days goes by. Furthermore, you can choose to have memories shown by the day, or to have everything shown together in one accumulative data visualization by toggling the on/off button below the knob (point 3, Figure 5). All of the options stated above allows the user to look into, and reflect upon, your habits and recording patterns along the lines of slow technology (Hallnäs & Redström, 2001). By pushing the button above the knob, the user ends his session.
As such, Elmer is intended as a time-based design piece inspired by slow technology. Through its use, a patchwork of memories form a web-like structure on the screen. It is no coincidence either, that that I have come to call this project “Elmer” either. “Elmer the Patchwork Elephant” is an 1980’s children’s book about an elephant that has a colorful patchwork-covered body instead of being grey like the rest of the elephant herd. The themes and issues dealt with in the story, is related to those of diversity and while being different, trusting in yourself, which I found particularly fitting on the topic of cyborgs. Lastly, there is of course the saying that elephants never forget, which again fits into this theme.
Besides the memory-oriented features of Elmer, I have taken the insights I have gotten from my interviews into consideration. Throughout the time I have worked on this project, I have not found a single reader whose design where meant to fit the ergonomics of a hand. All the market readers are made for tokens or smartcards, and this was also brought that was brought up during my interviews.