Mälardalen University Press Licentiate Theses No. 175
INITIAL TRUST ESTABLISHMENT FOR HETEROGENEOUS
INDUSTRIAL COMMUNICATION NETWORKS
Apala Ray
2014
School of Innovation, Design and Engineering
Mälardalen University Press Licentiate Theses
No. 175
INITIAL TRUST ESTABLISHMENT FOR HETEROGENEOUS
INDUSTRIAL COMMUNICATION NETWORKS
Apala Ray
2014
Copyright © Apala Ray, 2014 ISBN 978-91-7485-149-6 ISSN 1651-9256
Printed by Arkitektkopia, Västerås, Sweden
Abstract
The severity of cyber threats towards existing and future industrial systems has resulted in an increase of security awareness in the industrial automation do-main. Compared to traditional information security, industrial communication systems have different performance and reliability requirements. The safety and availability requirements can also sometimes conflict with the system se-curity design of plants. For instance, it is not acceptable to create a secure system which may take up additional time to establish security and as a con-sequence disrupt the production in plants. Similarly, a system which requires authentication and authorization procedures before any emergency action may not be suitable in industrial plants. Therefore, there is a need for improvement of the security workflow in industrial plants, so that the security can be realized in practice. This also leads to the requirement of secure device deployment and secure data communication inside the industrial plants.
In this thesis, the focus is on the initial trust establishment in industrial de-vices. The initial trust establishment is the starting point for enabling a secure communication infrastructure. Reusability analysis with financial sectors has been considered as the reuse of security solutions from this adjacent application domain can be a simple and an effective way to achieve the desired system se-curity. Through this analysis, the reusability features have been identified and workflows have been proposed which can be used to bootstrap initial trust in the industrial process control devices and manage security workflow. A proof-of-concept implementation to prove the feasibility of the device deployment workflow has also been provided.
Abstract
The severity of cyber threats towards existing and future industrial systems has resulted in an increase of security awareness in the industrial automation do-main. Compared to traditional information security, industrial communication systems have different performance and reliability requirements. The safety and availability requirements can also sometimes conflict with the system se-curity design of plants. For instance, it is not acceptable to create a secure system which may take up additional time to establish security and as a con-sequence disrupt the production in plants. Similarly, a system which requires authentication and authorization procedures before any emergency action may not be suitable in industrial plants. Therefore, there is a need for improvement of the security workflow in industrial plants, so that the security can be realized in practice. This also leads to the requirement of secure device deployment and secure data communication inside the industrial plants.
In this thesis, the focus is on the initial trust establishment in industrial de-vices. The initial trust establishment is the starting point for enabling a secure communication infrastructure. Reusability analysis with financial sectors has been considered as the reuse of security solutions from this adjacent application domain can be a simple and an effective way to achieve the desired system se-curity. Through this analysis, the reusability features have been identified and workflows have been proposed which can be used to bootstrap initial trust in the industrial process control devices and manage security workflow. A proof-of-concept implementation to prove the feasibility of the device deployment workflow has also been provided.
Sammanfattning
Det ¨okande IT-hotet mot industriella system har medf¨ort en st¨orre medvetenhet om behovet av IT-s¨akerhet f¨or industriella system. J¨amf¨ort med traditionella IT- och kommunikationssystem s˚a har industriella IT- och kommunikationssys-tem andra krav p˚a prestanda och tillf¨orlitlighet. De industriella syskommunikationssys-temens krav p˚a persons¨akerhet och h¨og tillg¨anglighet kommer ibland ocks˚a i konflikt med dagens l¨osningar f¨or IT-s¨akerhet. Det ¨ar exempelvis inte acceptabelt att skapa ett system med h¨og IT-s¨akerhet om det inneb¨ar att IT-s¨akerhetens mekanis-mer st¨or produktionen i den industriella anl¨aggningen. P˚a liknande s¨att ¨ar sys-tem som kr¨aver externt godk¨annande f¨or n¨od˚atg¨arder inte acceptabla i indus-triella milj¨oer med h¨oga krav p˚a persons¨akerhet. Av denna anledning beh¨over existerande processer f¨or IT-s¨akerhet f¨orb¨attras f¨or att vara anv¨andbara i in-dustriella system med krav p˚a persons¨akerhet och tillg¨anglighet. Detta leder ocks˚a till nya krav p˚a IT-s¨akerhet vad g¨aller datakommunikation och vad g¨aller inf¨orandet av nya enheter i industriella system.
I denna avhandling fokuserar vi p˚a att etablera tillit f¨or industriella enheter. Denna initiala tillit ¨ar startpunkten f¨or att kunna bygga s¨akra infrastrukturer f¨or datakommunikation i industriella milj¨oer. Vi har analyserat m¨ojligheten att ˚ateranv¨anda IT-s¨akerhetsl¨osningar fr˚an det finansiella omr˚adet, eftersom ˚ateranv¨andning av existerande l¨osningar kan vara ett effektivt s¨att att n˚a godtag-bara s¨akerhetsniv˚aer. Genom denna analys har vi funnit dell¨osningar som kan ˚ateranv¨andas inom det industriella omr˚adet. Baserat p˚a dessa resultat har nya processer skapats f¨or att etablera initial tillit i industriell kommunikation med enheter f¨or industriell processkontroll, samt processer f¨or effektiv hantering av IT-s¨akerhet. Vi har ¨aven implementerat dessa processer i en experimentmilj¨o f¨or att visa p˚a anv¨andbarheten av v˚ara processer.
Sammanfattning
Det ¨okande IT-hotet mot industriella system har medf¨ort en st¨orre medvetenhet om behovet av IT-s¨akerhet f¨or industriella system. J¨amf¨ort med traditionella IT- och kommunikationssystem s˚a har industriella IT- och kommunikationssys-tem andra krav p˚a prestanda och tillf¨orlitlighet. De industriella syskommunikationssys-temens krav p˚a persons¨akerhet och h¨og tillg¨anglighet kommer ibland ocks˚a i konflikt med dagens l¨osningar f¨or IT-s¨akerhet. Det ¨ar exempelvis inte acceptabelt att skapa ett system med h¨og IT-s¨akerhet om det inneb¨ar att IT-s¨akerhetens mekanis-mer st¨or produktionen i den industriella anl¨aggningen. P˚a liknande s¨att ¨ar sys-tem som kr¨aver externt godk¨annande f¨or n¨od˚atg¨arder inte acceptabla i indus-triella milj¨oer med h¨oga krav p˚a persons¨akerhet. Av denna anledning beh¨over existerande processer f¨or IT-s¨akerhet f¨orb¨attras f¨or att vara anv¨andbara i in-dustriella system med krav p˚a persons¨akerhet och tillg¨anglighet. Detta leder ocks˚a till nya krav p˚a IT-s¨akerhet vad g¨aller datakommunikation och vad g¨aller inf¨orandet av nya enheter i industriella system.
I denna avhandling fokuserar vi p˚a att etablera tillit f¨or industriella enheter. Denna initiala tillit ¨ar startpunkten f¨or att kunna bygga s¨akra infrastrukturer f¨or datakommunikation i industriella milj¨oer. Vi har analyserat m¨ojligheten att ˚ateranv¨anda IT-s¨akerhetsl¨osningar fr˚an det finansiella omr˚adet, eftersom ˚ateranv¨andning av existerande l¨osningar kan vara ett effektivt s¨att att n˚a godtag-bara s¨akerhetsniv˚aer. Genom denna analys har vi funnit dell¨osningar som kan ˚ateranv¨andas inom det industriella omr˚adet. Baserat p˚a dessa resultat har nya processer skapats f¨or att etablera initial tillit i industriell kommunikation med enheter f¨or industriell processkontroll, samt processer f¨or effektiv hantering av IT-s¨akerhet. Vi har ¨aven implementerat dessa processer i en experimentmilj¨o f¨or att visa p˚a anv¨andbarheten av v˚ara processer.
Acknowledgements
First of all I would like to express my heartfelt thanks to my supervisors Mats Bj¨orkman (MDH), Johan ˚Akerberg (ABB Corporate Research) and Mikael Gidlund (ABB Corporate Research) for constant support, motivation and en-couragement throughout the past two and half years which have made this work possible. It is my pleasure to have you as supervisors. I have learnt how to be-come a qualified and independent researcher through you.
I would also like to express my special thanks to Dr. Magnus Larsson, who generously accepted to be my mentor and guided me towards my Licentiate journey. All the discussions with you gave me valuable inspirations for my research.
I am very grateful to all of you who made time in your very busy schedules to read and comment on my drafts. I give my sincerest thanks to each one of you, who deserve special recognition for your unique insights and comments: Prof. Mats Bj¨orkman, Dr. Johan ˚Akerberg, Prof. Mikael Gidlund, Prof. Mag-nus Larsson, Dr. Deepaknath Tandur, Dr. Gargi Bag, Dr. Tomas Lennvall, Dr. Venkateswaran Narayanan, Dr. Judith Rossebø, Mallikarjun Kande, Pradnya Gaonkar, Fredrik Ekstrand. Your thorough reading and practical suggestions have improved this work.
The work would not have been possible without the support from ABB Corporate Research. I would like to express my sincere gratitude to Stefan Svensson, Dr. Venkateswaran Narayanan and Mallikarjun Kande for providing me with opportunities and resources for the research study. I would also like to express my gratitude to Peter L¨ofgren for allowing me to be in his group dur-ing my first year of research study in Sweden. This initial year of my study has really helped me to start my research work in a good shape. I would also like to give special thanks to the ITS-EASY Industrial Research School, affiliated with the School of Innovation, Design and Engineering (IDT) at M¨alardalen University for creating a friendly and cooperative research and educational
Acknowledgements
First of all I would like to express my heartfelt thanks to my supervisors Mats Bj¨orkman (MDH), Johan ˚Akerberg (ABB Corporate Research) and Mikael Gidlund (ABB Corporate Research) for constant support, motivation and en-couragement throughout the past two and half years which have made this work possible. It is my pleasure to have you as supervisors. I have learnt how to be-come a qualified and independent researcher through you.
I would also like to express my special thanks to Dr. Magnus Larsson, who generously accepted to be my mentor and guided me towards my Licentiate journey. All the discussions with you gave me valuable inspirations for my research.
I am very grateful to all of you who made time in your very busy schedules to read and comment on my drafts. I give my sincerest thanks to each one of you, who deserve special recognition for your unique insights and comments: Prof. Mats Bj¨orkman, Dr. Johan ˚Akerberg, Prof. Mikael Gidlund, Prof. Mag-nus Larsson, Dr. Deepaknath Tandur, Dr. Gargi Bag, Dr. Tomas Lennvall, Dr. Venkateswaran Narayanan, Dr. Judith Rossebø, Mallikarjun Kande, Pradnya Gaonkar, Fredrik Ekstrand. Your thorough reading and practical suggestions have improved this work.
The work would not have been possible without the support from ABB Corporate Research. I would like to express my sincere gratitude to Stefan Svensson, Dr. Venkateswaran Narayanan and Mallikarjun Kande for providing me with opportunities and resources for the research study. I would also like to express my gratitude to Peter L¨ofgren for allowing me to be in his group dur-ing my first year of research study in Sweden. This initial year of my study has really helped me to start my research work in a good shape. I would also like to give special thanks to the ITS-EASY Industrial Research School, affiliated with the School of Innovation, Design and Engineering (IDT) at M¨alardalen University for creating a friendly and cooperative research and educational
viii
vironment. My sincere gratitude to Prof. Ivica Crnkovic, Dr. Radu Dobrin, Prof. Gordana Dodig-Crnkovic, Prof. Thomas Nolte, Prof. Hans Hansson and all the professors and lecturers in IDT from whom I have learnt a lot during my studies.
I have been fortunate to work with a group of friendly and energetic people from ABB Corporate Research and Malardalen University. I especially want to thank Ravish Kumar, Arijit Bose, Sanjeev Koul, Pradnya Gaonkar, Deepaknath Tandur, Anitha Varghese, Rahul Gore, Hariram Satheesh, Simi Valsan, Gaetana Sapienza, Gargi Bag, Tomas Lennvall, Ewa Hansen, Jonas Neander, Krister Landern¨as, Niclas Ericsson, Johan Palm, Linus Thrybom, Mikael Davidsson, Stephan Baumgart, Marcus J¨agemar, Daniel Kade, Kivanc Doganay, Kristian Wiklund, Tomas Olsson, Mehrdad Saadatmand, Henrik Jonsson and all fellow researchers in ABB, ITS-EASY and IDT for your friendship and nice company. Personally, this work would not have been possible without the support of my parents, Prithwiraj Ray and Ashrudhara Ray. I especially want to thank them for their sacrifice to make me grow and pursue my dreams. Thank you so much for supporting me at every step of my life and believing in me.
Apala Ray V¨aster˚as, June, 2014
List of Publications
Papers Included in the Licentiate Thesis
1Paper A Initial Key Distribution for Industrial Wireless Sensor Networks. -Apala Ray, Johan ˚Akerberg, Mikael Gidlund and Mats Bj¨orkman. In proceedings of the 2013 IEEE International Conference on Industrial Technology (ICIT), pages 1309 - 1314, Cape Town, South Africa, Febru-ary, 2013.
Paper B Reusability assessment of financial card readers’ security
mecha-nisms in process control devices. Apala Ray, Johan ˚Akerberg, Mikael
Gidlund, Mats Bj¨orkman and Christophe Tremlet. In proceedings of 11thIEEE International Conference on Industrial Informatics (INDIN),
pages 494 - 499, Bochum, Germany, July, 2013.
Paper C A Solution for Industrial Device Commissioning along with the
Ini-tial Trust Establishment. Apala Ray, Johan ˚Akerberg, Mikael Gidlund
and Mats Bj¨orkman. In proceedings of the 39thAnnual Conference of
the IEEE Industrial Electronics Society (IECON), pages 5570-5575, Vi-enna, Austria, November, 2013.
Paper D An Industrial Device Deployment Framework using the Initial Trust
Establishment Workflow. Apala Ray, Johan ˚Akerberg, Mikael Gidlund
and Mats Bj¨orkman. Submitted to the IEEE Transactions on Industrial Informatics.
1The included articles have been reformatted to comply with the licentiate layout
viii
vironment. My sincere gratitude to Prof. Ivica Crnkovic, Dr. Radu Dobrin, Prof. Gordana Dodig-Crnkovic, Prof. Thomas Nolte, Prof. Hans Hansson and all the professors and lecturers in IDT from whom I have learnt a lot during my studies.
I have been fortunate to work with a group of friendly and energetic people from ABB Corporate Research and Malardalen University. I especially want to thank Ravish Kumar, Arijit Bose, Sanjeev Koul, Pradnya Gaonkar, Deepaknath Tandur, Anitha Varghese, Rahul Gore, Hariram Satheesh, Simi Valsan, Gaetana Sapienza, Gargi Bag, Tomas Lennvall, Ewa Hansen, Jonas Neander, Krister Landern¨as, Niclas Ericsson, Johan Palm, Linus Thrybom, Mikael Davidsson, Stephan Baumgart, Marcus J¨agemar, Daniel Kade, Kivanc Doganay, Kristian Wiklund, Tomas Olsson, Mehrdad Saadatmand, Henrik Jonsson and all fellow researchers in ABB, ITS-EASY and IDT for your friendship and nice company. Personally, this work would not have been possible without the support of my parents, Prithwiraj Ray and Ashrudhara Ray. I especially want to thank them for their sacrifice to make me grow and pursue my dreams. Thank you so much for supporting me at every step of my life and believing in me.
Apala Ray V¨aster˚as, June, 2014
List of Publications
Papers Included in the Licentiate Thesis
1Paper A Initial Key Distribution for Industrial Wireless Sensor Networks. -Apala Ray, Johan ˚Akerberg, Mikael Gidlund and Mats Bj¨orkman. In proceedings of the 2013 IEEE International Conference on Industrial Technology (ICIT), pages 1309 - 1314, Cape Town, South Africa, Febru-ary, 2013.
Paper B Reusability assessment of financial card readers’ security
mecha-nisms in process control devices. Apala Ray, Johan ˚Akerberg, Mikael
Gidlund, Mats Bj¨orkman and Christophe Tremlet. In proceedings of 11thIEEE International Conference on Industrial Informatics (INDIN),
pages 494 - 499, Bochum, Germany, July, 2013.
Paper C A Solution for Industrial Device Commissioning along with the
Ini-tial Trust Establishment. Apala Ray, Johan ˚Akerberg, Mikael Gidlund
and Mats Bj¨orkman. In proceedings of the 39thAnnual Conference of
the IEEE Industrial Electronics Society (IECON), pages 5570-5575, Vi-enna, Austria, November, 2013.
Paper D An Industrial Device Deployment Framework using the Initial Trust
Establishment Workflow. Apala Ray, Johan ˚Akerberg, Mikael Gidlund
and Mats Bj¨orkman. Submitted to the IEEE Transactions on Industrial Informatics.
1The included articles have been reformatted to comply with the licentiate layout
x
Additional Papers, Not Included in the Licentiate
Thesis
• WirelessHART device integration challenges and solutions in industrial automation. Ravish Kumar, Apala Ray, Mallikarjun Kande. In
proceed-ings of the IEEE 18th Conference on Emerging Technologies and Fac-tory Automation (ETFA), pages 1-4, Cagliari, Italy, September, 2013.
• Wireless infrastructure for oil and gas inventory management. Shanthi
Vellingiri, Apala Ray, Mallikarjun Kande. In proceedings of the 39th
Annual Conference of the IEEE Industrial Electronics Society (IECON), pages 5461-5466, Vienna, Austria, November, 2013.
• Energy efficient environment control system using wireless condition mon-itoring. Mallikarjun Kande, Jithendrian Sundaravaradan, Apala Ray,
Venkateswaran Narayanan. In 8th International Conference and Expo on Emerging Technologies for a Smarter World (CEWIT), pages 1-4, New York, November 2011.
• Planning and analysis tool for large scale deployment of wireless sensor network. Apala Ray. International Journal of Next-Generation Networks
(IJNGN), Vol 1, No 1, December 2009.
Patents, Not Included in the Licentiate Thesis
• A method and a system for localization in industrial wireless sensor net-work. Apala Ray, Mallikarjun Kande, Venkateswaran Narayanan,
Rav-ish Kumar. WO2012014008 A1, 02-Feb-2012.
• A method of secure multiple joining for a device to join wireless sys-tem network and a wireless device thereof. Ravish Kumar, Apala Ray,
Mallikarjun Kande, Venkateswaran Narayanan, Hemanta K Kalita. -WO/2011/121388, 06-Oct-2011.
Contents
I
Thesis
1
1 Introduction 3 1.1 Research Problem . . . 6 1.1.1 Research Hypothesis . . . 7 1.1.2 Research Questions . . . 7 1.2 Research Method . . . 7 1.3 Thesis Scope . . . 9 1.4 Thesis Outline . . . 10 2 Security in Automation 11 2.1 Industrial Automation . . . 11 2.2 Wireless in Automation . . . 13 2.3 Communication Security . . . 14 2.3.1 Security Requirements . . . 15 2.3.2 Cryptography . . . 15 3 Related Work 21 3.1 Industrial automation security . . . 213.2 Key management . . . 23 4 Scientific Contributions 25 4.1 Paper A . . . 26 4.2 Paper B . . . 27 4.3 Paper C . . . 28 4.4 Paper D . . . 29 xi
x
Additional Papers, Not Included in the Licentiate
Thesis
• WirelessHART device integration challenges and solutions in industrial automation. Ravish Kumar, Apala Ray, Mallikarjun Kande. In
proceed-ings of the IEEE 18th Conference on Emerging Technologies and Fac-tory Automation (ETFA), pages 1-4, Cagliari, Italy, September, 2013.
• Wireless infrastructure for oil and gas inventory management. Shanthi
Vellingiri, Apala Ray, Mallikarjun Kande. In proceedings of the 39th
Annual Conference of the IEEE Industrial Electronics Society (IECON), pages 5461-5466, Vienna, Austria, November, 2013.
• Energy efficient environment control system using wireless condition mon-itoring. Mallikarjun Kande, Jithendrian Sundaravaradan, Apala Ray,
Venkateswaran Narayanan. In 8th International Conference and Expo on Emerging Technologies for a Smarter World (CEWIT), pages 1-4, New York, November 2011.
• Planning and analysis tool for large scale deployment of wireless sensor network. Apala Ray. International Journal of Next-Generation Networks
(IJNGN), Vol 1, No 1, December 2009.
Patents, Not Included in the Licentiate Thesis
• A method and a system for localization in industrial wireless sensor net-work. Apala Ray, Mallikarjun Kande, Venkateswaran Narayanan,
Rav-ish Kumar. WO2012014008 A1, 02-Feb-2012.
• A method of secure multiple joining for a device to join wireless sys-tem network and a wireless device thereof. Ravish Kumar, Apala Ray,
Mallikarjun Kande, Venkateswaran Narayanan, Hemanta K Kalita. -WO/2011/121388, 06-Oct-2011.
Contents
I
Thesis
1
1 Introduction 3 1.1 Research Problem . . . 6 1.1.1 Research Hypothesis . . . 7 1.1.2 Research Questions . . . 7 1.2 Research Method . . . 7 1.3 Thesis Scope . . . 9 1.4 Thesis Outline . . . 10 2 Security in Automation 11 2.1 Industrial Automation . . . 11 2.2 Wireless in Automation . . . 13 2.3 Communication Security . . . 14 2.3.1 Security Requirements . . . 15 2.3.2 Cryptography . . . 15 3 Related Work 21 3.1 Industrial automation security . . . 213.2 Key management . . . 23 4 Scientific Contributions 25 4.1 Paper A . . . 26 4.2 Paper B . . . 27 4.3 Paper C . . . 28 4.4 Paper D . . . 29 xi
xii Contents
5 Conclusions and Future Work 31
5.1 Conclusions . . . 31
5.2 Future Work . . . 32
Bibliography 35
II
Included Papers
43
6 Paper A: Initial Key Distribution for Industrial Wireless Sensor Networks 45 6.1 Introduction . . . 476.2 Related Work . . . 49
6.3 Industrial Standard and Current Practice on Key Management Workflow . . . 50
6.3.1 Key Management in WirelessHART standard . . . 51
6.3.2 Current Practice in Key Management . . . 52
6.4 Assessment of current practice key distribution in Industrial Wireless Sensor Networks . . . 54
6.5 Key Distribution Pre-requisite and Assessment . . . 56
6.6 Conclusion and Future Work . . . 58
Bibliography . . . 61
7 Paper B: Reusability assessment of financial card readers’ security mecha-nisms in process control devices 65 7.1 Introduction . . . 67
7.2 Related Work . . . 68
7.3 Overview of industrial plants and the financial sector . . . 69
7.4 Assessment of reusability of security features from financial card readers . . . 72
7.4.1 Comparison of workflow between financial card read-ers and industrial process control devices . . . 72
7.4.2 Assessment of threats and countermeasures between fi-nancial card readers and industrial process control de-vices . . . 75
7.5 Conclusion and Future Work . . . 78
Bibliography . . . 81
Contents xiii 8 Paper C: A Solution for Industrial Device Commissioning along with the Ini-tial Trust Establishment 83 8.1 Introduction . . . 85
8.2 Related Work . . . 86
8.3 Device commissioning with the initial trust establishment - Over-view . . . 87
8.3.1 Workflow objective . . . 87
8.3.2 System components and the assumptions . . . 88
8.3.3 Proposed Workflow - Device commissioning with the initial trust establishment . . . 90
8.4 Assessment of the initial trust establishment workflow . . . 93
8.5 Conclusion and Future Work . . . 95
Bibliography . . . 97
9 Paper D: An Industrial Device Deployment Framework using the Initial Trust Establishment Workflow 99 9.1 Introduction . . . 101
9.2 Industrial Device Deployment - An Overview . . . 105
9.2.1 Solution objective . . . 105
9.2.2 System components and the assumptions . . . 105
9.2.3 Framework Overview: . . . 107
9.3 Industrial Device Deployment - Framework . . . 108
9.3.1 Initial Trust based authentication: . . . 110
9.3.2 Authenticity verification phase: . . . 113
9.3.3 Key Establishment: . . . 115
9.4 Proof-of-concept Implementation . . . 118
9.5 Assessment and discussion of the device deployment frame-work for industrial plants . . . 121
9.5.1 Discussion on Framework Objective . . . 121
9.5.2 Formal verification and validation of protocol using AVISPA . . . 123
9.6 Conclusions and future work . . . 124
xii Contents
5 Conclusions and Future Work 31
5.1 Conclusions . . . 31
5.2 Future Work . . . 32
Bibliography 35
II
Included Papers
43
6 Paper A: Initial Key Distribution for Industrial Wireless Sensor Networks 45 6.1 Introduction . . . 476.2 Related Work . . . 49
6.3 Industrial Standard and Current Practice on Key Management Workflow . . . 50
6.3.1 Key Management in WirelessHART standard . . . 51
6.3.2 Current Practice in Key Management . . . 52
6.4 Assessment of current practice key distribution in Industrial Wireless Sensor Networks . . . 54
6.5 Key Distribution Pre-requisite and Assessment . . . 56
6.6 Conclusion and Future Work . . . 58
Bibliography . . . 61
7 Paper B: Reusability assessment of financial card readers’ security mecha-nisms in process control devices 65 7.1 Introduction . . . 67
7.2 Related Work . . . 68
7.3 Overview of industrial plants and the financial sector . . . 69
7.4 Assessment of reusability of security features from financial card readers . . . 72
7.4.1 Comparison of workflow between financial card read-ers and industrial process control devices . . . 72
7.4.2 Assessment of threats and countermeasures between fi-nancial card readers and industrial process control de-vices . . . 75
7.5 Conclusion and Future Work . . . 78
Bibliography . . . 81
Contents xiii 8 Paper C: A Solution for Industrial Device Commissioning along with the Ini-tial Trust Establishment 83 8.1 Introduction . . . 85
8.2 Related Work . . . 86
8.3 Device commissioning with the initial trust establishment - Over-view . . . 87
8.3.1 Workflow objective . . . 87
8.3.2 System components and the assumptions . . . 88
8.3.3 Proposed Workflow - Device commissioning with the initial trust establishment . . . 90
8.4 Assessment of the initial trust establishment workflow . . . 93
8.5 Conclusion and Future Work . . . 95
Bibliography . . . 97
9 Paper D: An Industrial Device Deployment Framework using the Initial Trust Establishment Workflow 99 9.1 Introduction . . . 101
9.2 Industrial Device Deployment - An Overview . . . 105
9.2.1 Solution objective . . . 105
9.2.2 System components and the assumptions . . . 105
9.2.3 Framework Overview: . . . 107
9.3 Industrial Device Deployment - Framework . . . 108
9.3.1 Initial Trust based authentication: . . . 110
9.3.2 Authenticity verification phase: . . . 113
9.3.3 Key Establishment: . . . 115
9.4 Proof-of-concept Implementation . . . 118
9.5 Assessment and discussion of the device deployment frame-work for industrial plants . . . 121
9.5.1 Discussion on Framework Objective . . . 121
9.5.2 Formal verification and validation of protocol using AVISPA . . . 123
9.6 Conclusions and future work . . . 124
I
Thesis
I
Thesis
Chapter 1
Introduction
Industrial control systems, which include Supervisory Control And Data Ac-quisition (SCADA) systems, Distributed Control Systems (DCS), and Pro-grammable Logic Controllers (PLC), are typically used in process industries like pulp and paper, water and wastewater, food and beverages, mining etc. The goal of industrial automation is to automate the operations involved in the technical process with minimal or reduced human intervention. Since the last decade, the severity of cyber threats towards existing and future industrial sys-tems has increased the security awareness in the industrial automation domain. Industrial communication involves various ranges of hardware and software products and protocols which are used to establish communication between in-dustrial automation devices and standard computer platforms. These systems were built to meet performance, reliability, safety and flexibility requirements without much concern regarding secure communication capabilities. To be-gin with, industrial automation plants were built as stand-alone systems, where specialized hardware and software were used based on proprietary control pro-tocols. At the same time, many of these components were not connected with the outside world, so security had less attention. Over the last few years, com-panies have been moving towards fast and cost effective decisions based on real-time information about the plant and the processes, in order to increase the interconnection and predictability between different automation systems. This has raised the level of security threats. In addition to this, wireless solutions have become more prevalent in industrial plants. Process industries have seen a smoother transition towards wireless communication systems with the ad-vancement of wireless field networks. The integration of wireless devices with
Chapter 1
Introduction
Industrial control systems, which include Supervisory Control And Data Ac-quisition (SCADA) systems, Distributed Control Systems (DCS), and Pro-grammable Logic Controllers (PLC), are typically used in process industries like pulp and paper, water and wastewater, food and beverages, mining etc. The goal of industrial automation is to automate the operations involved in the technical process with minimal or reduced human intervention. Since the last decade, the severity of cyber threats towards existing and future industrial sys-tems has increased the security awareness in the industrial automation domain. Industrial communication involves various ranges of hardware and software products and protocols which are used to establish communication between in-dustrial automation devices and standard computer platforms. These systems were built to meet performance, reliability, safety and flexibility requirements without much concern regarding secure communication capabilities. To be-gin with, industrial automation plants were built as stand-alone systems, where specialized hardware and software were used based on proprietary control pro-tocols. At the same time, many of these components were not connected with the outside world, so security had less attention. Over the last few years, com-panies have been moving towards fast and cost effective decisions based on real-time information about the plant and the processes, in order to increase the interconnection and predictability between different automation systems. This has raised the level of security threats. In addition to this, wireless solutions have become more prevalent in industrial plants. Process industries have seen a smoother transition towards wireless communication systems with the ad-vancement of wireless field networks. The integration of wireless devices with
4 Chapter 1. Introduction
industrial automation systems has also raised the device security challenges. Compared to traditional information security, industrial communication systems have different performance and reliability requirements. One of the most important requirements for industrial plants is safety of personnel, equip-ment, and the environment. Any loopholes in security infrastructure may seve-rely impact the system and might affect the safety of the plant and its person-nel. Another important requirement for an industrial plant is the continuous availability of systems and components. Traditional security processes primar-ily focus on confidentiality, integrity and availability. In industrial plants, the availability comes first. Many processes in industrial plants are continuous in nature and the expectation is that the plant system should be operational over a long period of time, for example 10 to 15 years of continuous operation. Un-planned downtime is not acceptable as plant downtime leads to a huge loss for companies. For this reason, plant outages are generally planned and sched-uled days/weeks in advance. Therefore, the goal of safety and availability can sometimes conflict with the security design of plants. For instance, it is not acceptable to create a secure system which may require additional time to es-tablish security and as a consequence disrupt production in plants. Similarly, a system which requires prior authentication and authorization for emergency actions is not suitable for industrial plants.
Industrial plants involve many employees with different authorization roles for 24x7 operation of the plant. An industrial plant in general may have spe-cific employees who are assigned to particular roles for plant management [1]. For example, the following roles are relevant to the security management in industrial plants, (a) manufacturers of the devices, (b) system integrators, (c) operators, and (d) service personnel. Manufacturers produce the devices. Sys-tem integrators customize those devices and integrate them into the plant. They also perform commissioning. Operators monitor the system during their nor-mal operation and respond to alarms. Service personnel are responsible for maintaining and repairing the devices. In addition to this, these roles might be manned from different organizations. For instance, the manufacturer may be the asset owner or from an external company. The system integrators for the plant may be the manufacturer, the asset owner, or an external company. These roles are involved in operation of the plants including the device functionality and their management. Successful functionalities of plants are possible when the devices are properly commissioned, operated and maintained. Therefore, the security management of devices inside the plant is indirectly coupled with the different employees and their roles. The device access can be managed through a role-based access control policy but there might be several
employ-5
ees who share the same role. Therefore, the role-based access control cannot guarantee accountability for an individual employee. For a successful security deployment in plants, it is necessary to create accountability and establish a relationship between the employee and the device. At present, the industrial automation life cycle does not have a workflow which can link and manage both the device security and the employee access. Therefore, there is a need to harmonize the link between device security and employee access.
Industrial plant automation encompasses a mix of wired and wireless com-munication technologies. Wireless comcom-munication is expanding into industrial communication areas where deploying wired communication has been a chal-lenge with respect to cost, mobility, or mechanical wear. However, the config-uration workflow for wired and wireless technologies differs from each other. The automation protocols, which are designed for wired devices, require prior configuration of parameters, so that the devices can respond to their master’s queries. On the other hand, the wireless protocols enable network and device configuration once the device is authenticated to access the network. This leads to a requirement of unified commissioning and engineering workflow for both the wired and wireless devices with adequate security. Therefore, there is a demand for efficient security workflow for secured communication in hetero-geneous industrial automation networks.
Industrial system security requires secure management of workflow and policies. The security management involves the perimeter security with phys-ical access control, physphys-ical intrusion detection etc. It also requires the device security where the hardware, software and firmware need to be protected. The security of communication is another aspect where the message or data need to be protected. In addition to all these, security assessment is another part of security management workflow to monitor and test the security status in industrial system. Cryptography is used to address important aspects of com-munication security, such as, message authentication and integrity as well as confidentiality. Within cryptography, key management is the most dynamic field of research and there are challenges in the area of industrial plant key management.
4 Chapter 1. Introduction
industrial automation systems has also raised the device security challenges. Compared to traditional information security, industrial communication systems have different performance and reliability requirements. One of the most important requirements for industrial plants is safety of personnel, equip-ment, and the environment. Any loopholes in security infrastructure may seve-rely impact the system and might affect the safety of the plant and its person-nel. Another important requirement for an industrial plant is the continuous availability of systems and components. Traditional security processes primar-ily focus on confidentiality, integrity and availability. In industrial plants, the availability comes first. Many processes in industrial plants are continuous in nature and the expectation is that the plant system should be operational over a long period of time, for example 10 to 15 years of continuous operation. Un-planned downtime is not acceptable as plant downtime leads to a huge loss for companies. For this reason, plant outages are generally planned and sched-uled days/weeks in advance. Therefore, the goal of safety and availability can sometimes conflict with the security design of plants. For instance, it is not acceptable to create a secure system which may require additional time to es-tablish security and as a consequence disrupt production in plants. Similarly, a system which requires prior authentication and authorization for emergency actions is not suitable for industrial plants.
Industrial plants involve many employees with different authorization roles for 24x7 operation of the plant. An industrial plant in general may have spe-cific employees who are assigned to particular roles for plant management [1]. For example, the following roles are relevant to the security management in industrial plants, (a) manufacturers of the devices, (b) system integrators, (c) operators, and (d) service personnel. Manufacturers produce the devices. Sys-tem integrators customize those devices and integrate them into the plant. They also perform commissioning. Operators monitor the system during their nor-mal operation and respond to alarms. Service personnel are responsible for maintaining and repairing the devices. In addition to this, these roles might be manned from different organizations. For instance, the manufacturer may be the asset owner or from an external company. The system integrators for the plant may be the manufacturer, the asset owner, or an external company. These roles are involved in operation of the plants including the device functionality and their management. Successful functionalities of plants are possible when the devices are properly commissioned, operated and maintained. Therefore, the security management of devices inside the plant is indirectly coupled with the different employees and their roles. The device access can be managed through a role-based access control policy but there might be several
employ-5
ees who share the same role. Therefore, the role-based access control cannot guarantee accountability for an individual employee. For a successful security deployment in plants, it is necessary to create accountability and establish a relationship between the employee and the device. At present, the industrial automation life cycle does not have a workflow which can link and manage both the device security and the employee access. Therefore, there is a need to harmonize the link between device security and employee access.
Industrial plant automation encompasses a mix of wired and wireless com-munication technologies. Wireless comcom-munication is expanding into industrial communication areas where deploying wired communication has been a chal-lenge with respect to cost, mobility, or mechanical wear. However, the config-uration workflow for wired and wireless technologies differs from each other. The automation protocols, which are designed for wired devices, require prior configuration of parameters, so that the devices can respond to their master’s queries. On the other hand, the wireless protocols enable network and device configuration once the device is authenticated to access the network. This leads to a requirement of unified commissioning and engineering workflow for both the wired and wireless devices with adequate security. Therefore, there is a demand for efficient security workflow for secured communication in hetero-geneous industrial automation networks.
Industrial system security requires secure management of workflow and policies. The security management involves the perimeter security with phys-ical access control, physphys-ical intrusion detection etc. It also requires the device security where the hardware, software and firmware need to be protected. The security of communication is another aspect where the message or data need to be protected. In addition to all these, security assessment is another part of security management workflow to monitor and test the security status in industrial system. Cryptography is used to address important aspects of com-munication security, such as, message authentication and integrity as well as confidentiality. Within cryptography, key management is the most dynamic field of research and there are challenges in the area of industrial plant key management.
6 Chapter 1. Introduction
1.1 Research Problem
Industrial system security aims to protect the process control devices from
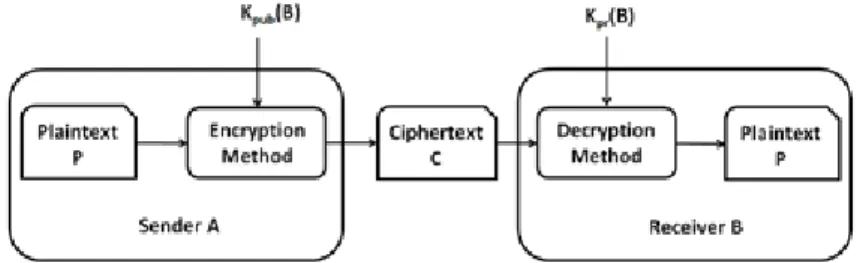
se-curity attacks. The first level of defense typically involves physical access control and user authentication. The second level of defense is in the security of various communication protocols which is used between various devices in a plant network. In any architecture of communication network security, there are two major types of cryptographic algorithms which are used for encryption: asymmetric key based and symmetric key based. In each case, the first goal is to establish an initial key between two devices in a trusted manner. The trust requires, if device A is communicating with device B, then device A should be sure that it is communicating with device B, not any other device C and vice versa. The problem statement is defined as follows:
1. In communication network security, there is either an explicit assump-tion or an explicit mechanism to establish the initial trust among the communication parties. The explicit assumption is that the devices in the network are trusted. This trust may be established by the explicit mech-anism of out-of-band initial trust bootstrapping such as manual entry of security key parameters in the device. However, such methods create an additional burden for engineers. It is also a non-trivial task for a com-missioning and maintenance engineer to find the physical devices that are spread over large areas and configure with the right parameters for different devices. The research problem is, therefore, to determine how one device can be allowed to join in the industrial network in a trusted way with minimal manual intervention and with minimal changes in the existing standards.
2. In today’s scenario, every signal from a wired device needs to be manu-ally checked prior to the commissioning in order to verify that the correct data is being received and transmitted to the intended physical entity. Commissioning engineers typically sign off these results in traditional commissioning reports. In practice, this is a critical and error-prone pro-cess since it is very likely that not all signals are checked due to the large number of signals involved. In addition to it, this work is time con-suming and can involve several persons over several days. The research problem to be investigated here is, how the commissioning parameters for the device can be securely downloaded to the correct device, along with the initial trust establishment, without manual verification and val-idation during the entire plant life-cycle.
1.2 Research Method 7
1.1.1 Research Hypothesis
The security issues in industrial plants are well discussed in both the industrial and research communities. In the current scenario, the available security tech-nologies and solutions are independent islands in an overall plant network due to the presence of old and new emerging technologies. The hypothesis in this research work is that, it is possible to have an integrated and complete solution which can cater to the overall plant instead of separate independent technolo-gies and solutions. This will help to eliminate the security gap between old and new technical solutions. The aim of this research work is to address the requirement of availability and reduced manual intervention in heterogeneous communication in industrial plants.
1.1.2 Research Questions
From the research hypothesis, we further refine the problem statements to for-mulate two questions that we will investigate in this thesis.
• Q1: How to efficiently bootstrap the initial trust to a large number of
devices in a heterogeneous network, considering the different roles of employees, and the entire plant life-cycle?
• Q2: How to efficiently manage the life cycle of the security workflow
in an industrial plant given the different roles of employees in the entire plant life-cycle?
1.2 Research Method
The research can be broadly classified in four categories based on the purpose, process, outcome and logic of the research [2].
• Exploratory, descriptive, analytical or predictive research - based on
pur-pose of the research
• Quantitative or qualitative research - based on process of the research • Applied or basic research - based on outcome of the research
6 Chapter 1. Introduction
1.1 Research Problem
Industrial system security aims to protect the process control devices from
se-curity attacks. The first level of defense typically involves physical access control and user authentication. The second level of defense is in the security of various communication protocols which is used between various devices in a plant network. In any architecture of communication network security, there are two major types of cryptographic algorithms which are used for encryption: asymmetric key based and symmetric key based. In each case, the first goal is to establish an initial key between two devices in a trusted manner. The trust requires, if device A is communicating with device B, then device A should be sure that it is communicating with device B, not any other device C and vice versa. The problem statement is defined as follows:
1. In communication network security, there is either an explicit assump-tion or an explicit mechanism to establish the initial trust among the communication parties. The explicit assumption is that the devices in the network are trusted. This trust may be established by the explicit mech-anism of out-of-band initial trust bootstrapping such as manual entry of security key parameters in the device. However, such methods create an additional burden for engineers. It is also a non-trivial task for a com-missioning and maintenance engineer to find the physical devices that are spread over large areas and configure with the right parameters for different devices. The research problem is, therefore, to determine how one device can be allowed to join in the industrial network in a trusted way with minimal manual intervention and with minimal changes in the existing standards.
2. In today’s scenario, every signal from a wired device needs to be manu-ally checked prior to the commissioning in order to verify that the correct data is being received and transmitted to the intended physical entity. Commissioning engineers typically sign off these results in traditional commissioning reports. In practice, this is a critical and error-prone pro-cess since it is very likely that not all signals are checked due to the large number of signals involved. In addition to it, this work is time con-suming and can involve several persons over several days. The research problem to be investigated here is, how the commissioning parameters for the device can be securely downloaded to the correct device, along with the initial trust establishment, without manual verification and val-idation during the entire plant life-cycle.
1.2 Research Method 7
1.1.1 Research Hypothesis
The security issues in industrial plants are well discussed in both the industrial and research communities. In the current scenario, the available security tech-nologies and solutions are independent islands in an overall plant network due to the presence of old and new emerging technologies. The hypothesis in this research work is that, it is possible to have an integrated and complete solution which can cater to the overall plant instead of separate independent technolo-gies and solutions. This will help to eliminate the security gap between old and new technical solutions. The aim of this research work is to address the requirement of availability and reduced manual intervention in heterogeneous communication in industrial plants.
1.1.2 Research Questions
From the research hypothesis, we further refine the problem statements to for-mulate two questions that we will investigate in this thesis.
• Q1: How to efficiently bootstrap the initial trust to a large number of
devices in a heterogeneous network, considering the different roles of employees, and the entire plant life-cycle?
• Q2: How to efficiently manage the life cycle of the security workflow
in an industrial plant given the different roles of employees in the entire plant life-cycle?
1.2 Research Method
The research can be broadly classified in four categories based on the purpose, process, outcome and logic of the research [2].
• Exploratory, descriptive, analytical or predictive research - based on
pur-pose of the research
• Quantitative or qualitative research - based on process of the research • Applied or basic research - based on outcome of the research
8 Chapter 1. Introduction
Figure 1.1: Research Method
In this thesis, the research work is defined based on the purpose and the logic of the research. At the starting point of this research, the security chal-lenges in industrial communication network were known. The first step in this thesis is to justify the selected topics of investigations from both industry and academia through analytical research. The state-of-the-art analysis and the lit-erature survey results in defining the problem statement and research questions. In the second step, the inductive research method is used. In this step, the specific observation is that the reuse of initial trust establishment of security solutions from adjacent industrial domains can be a simple and effective way to achieve a desired level of system security. Therefore, the financial sector segment has been chosen, since in this segment security has been carefully managed for a long time. As security is very important for this sector, the security mechanisms present in financial card readers which are involved in financial transactions have been evaluated.
In the third step, a workflow that uses the existing trust mechanism on employees to enable the initial bootstrap of trust in the devices is introduced. This concept is derived from the chip-and-pin enabled financial card readers’ transactions. Analytical research is used in this third step.
1.3 Thesis Scope 9
In the fourth step, both analytical and deductive research methods are used. A framework has been proposed where the device can be verified by the em-ployee management system and security management component inside plant. This can be done only once the commissioning engineer or maintenance engi-neer has transferred their employee trust parameters to the device. Through a proof-of-concept implementation and formal verification the feasibility of de-vice deployment workflow has been demonstrated.
Finally, the findings in this initial trust establishment research have been summarized and future research work is defined.
1.3 Thesis Scope
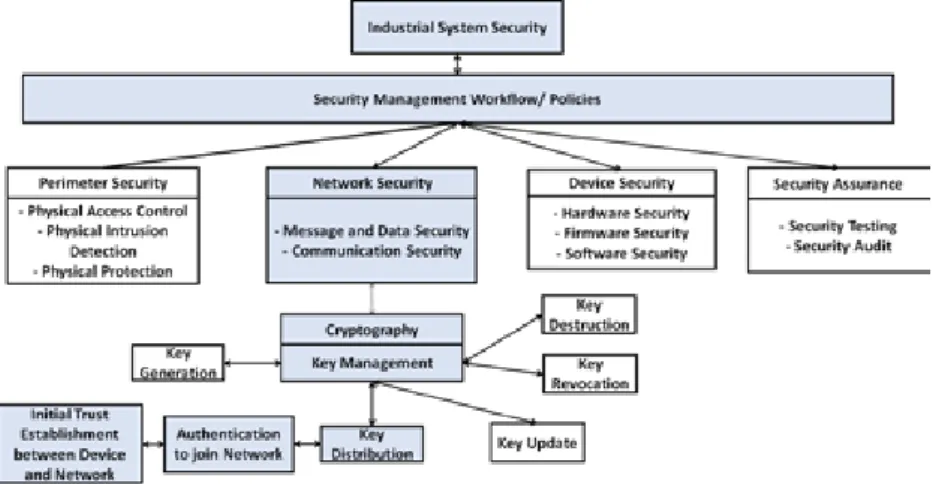
The scope of this thesis is to provide a mechanism for initial trust establishment between industrial devices and heterogeneous industrial network. As shown in Figure 1.2, the illustration of the areas in industrial system security presents the scope of the thesis. The aim of this illustration is not to define the industrial system security, rather to help readers to find out where the contribution of this research fits in.
Figure 1.2: Scope of the Thesis
The industrial system security requires the security management workflow or policies related to Perimeter Security, Device Security and Network Secu-rity. One important aspect of network security is the key management for
cryp-8 Chapter 1. Introduction
Figure 1.1: Research Method
In this thesis, the research work is defined based on the purpose and the logic of the research. At the starting point of this research, the security chal-lenges in industrial communication network were known. The first step in this thesis is to justify the selected topics of investigations from both industry and academia through analytical research. The state-of-the-art analysis and the lit-erature survey results in defining the problem statement and research questions. In the second step, the inductive research method is used. In this step, the specific observation is that the reuse of initial trust establishment of security solutions from adjacent industrial domains can be a simple and effective way to achieve a desired level of system security. Therefore, the financial sector segment has been chosen, since in this segment security has been carefully managed for a long time. As security is very important for this sector, the security mechanisms present in financial card readers which are involved in financial transactions have been evaluated.
In the third step, a workflow that uses the existing trust mechanism on employees to enable the initial bootstrap of trust in the devices is introduced. This concept is derived from the chip-and-pin enabled financial card readers’ transactions. Analytical research is used in this third step.
1.3 Thesis Scope 9
In the fourth step, both analytical and deductive research methods are used. A framework has been proposed where the device can be verified by the em-ployee management system and security management component inside plant. This can be done only once the commissioning engineer or maintenance engi-neer has transferred their employee trust parameters to the device. Through a proof-of-concept implementation and formal verification the feasibility of de-vice deployment workflow has been demonstrated.
Finally, the findings in this initial trust establishment research have been summarized and future research work is defined.
1.3 Thesis Scope
The scope of this thesis is to provide a mechanism for initial trust establishment between industrial devices and heterogeneous industrial network. As shown in Figure 1.2, the illustration of the areas in industrial system security presents the scope of the thesis. The aim of this illustration is not to define the industrial system security, rather to help readers to find out where the contribution of this research fits in.
Figure 1.2: Scope of the Thesis
The industrial system security requires the security management workflow or policies related to Perimeter Security, Device Security and Network Secu-rity. One important aspect of network security is the key management for
cryp-10 Chapter 1. Introduction
tographic operations. In this thesis, the focus is on the initial trust establishment between industrial devices and the industrial network.
1.4 Thesis Outline
The thesis is organized into two parts:
Part I includes the first five chapters. Chapter 1 provides the introduction and formulates the research problem. Chapter 2 presents the background knowl-edge of industrial automation and security. Chapter 3 discusses related work. In Chapter 4, discusses the contributions in this thesis. Chapter 5 presents the conclusion and suggestions for future work.
Part II presents the scientific contributions of the thesis in the form of four papers which are organized in Chapters 6-9.
Chapter 2
Security in Automation
In this chapter we introduce the information which is fundamental for better understanding of the problem and solution that are proposed in this thesis. At first, an overview of industrial automation plants is given. Next, automation with wireless communication is discussed to demonstrate the use of wireless technologies in industrial automation. Finally, basic communication security is discussed.
2.1 Industrial Automation
Industrial automation is a broad area which can be divided into different cat-egories such as process automation, factory automation, building automation, home automation and substation automation [3]. The characteristics of these different automation domains differ significantly based on requirements of sa-fety, security and availability. The communication medium in industrial au-tomation is traditionally wired. These wired industrial communication systems have been applied successfully for decades. With the advancement of technol-ogy, wireless communication became another option for industrial communi-cation. The well-known benefits of wireless communication in industrial plants are cost efficiency, flexible deployment, convenient installation and availabil-ity [4].
Generally, the architectural model of industrial automation is depicted in the pyramid structure [5], known as the Automation Pyramid as shown in Fig-ure 2.1. This hierarchical topology system model is based on the properties
10 Chapter 1. Introduction
tographic operations. In this thesis, the focus is on the initial trust establishment between industrial devices and the industrial network.
1.4 Thesis Outline
The thesis is organized into two parts:
Part I includes the first five chapters. Chapter 1 provides the introduction and formulates the research problem. Chapter 2 presents the background knowl-edge of industrial automation and security. Chapter 3 discusses related work. In Chapter 4, discusses the contributions in this thesis. Chapter 5 presents the conclusion and suggestions for future work.
Part II presents the scientific contributions of the thesis in the form of four papers which are organized in Chapters 6-9.
Chapter 2
Security in Automation
In this chapter we introduce the information which is fundamental for better understanding of the problem and solution that are proposed in this thesis. At first, an overview of industrial automation plants is given. Next, automation with wireless communication is discussed to demonstrate the use of wireless technologies in industrial automation. Finally, basic communication security is discussed.
2.1 Industrial Automation
Industrial automation is a broad area which can be divided into different cat-egories such as process automation, factory automation, building automation, home automation and substation automation [3]. The characteristics of these different automation domains differ significantly based on requirements of sa-fety, security and availability. The communication medium in industrial au-tomation is traditionally wired. These wired industrial communication systems have been applied successfully for decades. With the advancement of technol-ogy, wireless communication became another option for industrial communi-cation. The well-known benefits of wireless communication in industrial plants are cost efficiency, flexible deployment, convenient installation and availabil-ity [4].
Generally, the architectural model of industrial automation is depicted in the pyramid structure [5], known as the Automation Pyramid as shown in Fig-ure 2.1. This hierarchical topology system model is based on the properties
12 Chapter 2. Security in Automation
of different levels. Typically, the bottom of this hierarchy is the field network which consists of sensors and actuators. The next level is the control network, which typically consists of controllers, connectivity servers. The top level is the
plant/server network which consists of operator workplaces, engineering and
monitoring stations, and servers. The plant/server network can be connected to the Internet for remote monitoring through firewalls and virtual private net-works (VPN).
Figure 2.1: Industrial Automation Pyramid
The shape of the pyramid depicts the volume of information at different levels. From the lower level to the upper level, the information amount is reduced as in every level the data is processed and sent to the next upper level. For example, the bottom level of the pyramid, i.e., at the field network, the data of interest will be sensor data which is transferred to the control network. At the control network level, the data which are related to the operator, for example, the control loop performance, will be transferred to the next level. At the top level of the pyramid, the main interest will be the data that provides information related to the quantity and quality of the product.
Typically an industrial plant has a mix of different industrial communica-tion protocols and these industrial protocols are usually common across several industries. These industrial communication protocols require specific hardware and software for robust and reliable operations inside the plants. There are many protocols that exist and are used in the industrial communication
mar-2.2 Wireless in Automation 13
ket. The three most dominant protocols are Foundation Fieldbus, Profibus and Profinet. Foundation Fieldbus is broadly used in the United States. Profibus and Profinet are preferred in Europe. The total installed base is in the order of one hundred million devices and is increasing [3]. Some of the industrial communication protocols such as the Distributed Network Protocol 3.0 and Modbus were originally developed to run over a serial connection. Later, these were adapted to run on top of the TCP/IP stack as application layer proto-cols [6]. Therefore, many of these industrial and proprietary protoproto-cols lack proper security measures in terms of authentication or integrity checking and do not support any cryptography mechanisms.
2.2 Wireless in Automation
Wireless technologies have been used in industrial plants for quite some time. In the higher level of the communication architecture of industrial automation, Wireless LANs, long-haul wireless links are commonly found. On the field network level, low rate and short distance wireless technologies are suitable communication technologies as the applications support low rates. However, in the field level application also Wireless LANs are being used. For factory automation ABB developed the Wireless Interface to Sensors and Actuators (WISA) [7] radio technology. It was released in 2001 and later WISA-COM is standardized by WSAN (Wireless Sensor-Actuator Network).
The IEEE 802.15 working group focuses on developing standards for Per-sonal Area Networks (WPAN) or short distance wireless network. Bluetooth [8] is an 802.15.1 based wireless personal network area technology. Gener-ally Bluetooth uses peer to peer communication whereas field networks some-times demand a large scale network with many sensor devices. The IEEE 802.15.4 specifies the PHY and MAC layers in the OSI model (Open Systems Interconnection model). The higher layers are specified by other standards that use 802.15.4 as base, for example, ZigBee [9], WirelessHART [10, 11], ISA100.11a [12], WIA-PA [13]. In [14], Lennvall et al. presented a per-formance comparison between WirelessHART and ZigBee standards. Their conclusion was that the ZigBee standard is not suitable in industrial environ-ments due to poor performance, and because security is optional, while in the WirelessHART standard it is mandatory. In process automation the stan-dards for industrial wireless sensor networks are WirelessHART, ISA100.11a, WIA-PA. These standards are based on IEEE 802.15.4-2006. However, Wire-lessHART, ISA-100a, and WIA-PA may merge into one industrial standard in
12 Chapter 2. Security in Automation
of different levels. Typically, the bottom of this hierarchy is the field network which consists of sensors and actuators. The next level is the control network, which typically consists of controllers, connectivity servers. The top level is the
plant/server network which consists of operator workplaces, engineering and
monitoring stations, and servers. The plant/server network can be connected to the Internet for remote monitoring through firewalls and virtual private net-works (VPN).
Figure 2.1: Industrial Automation Pyramid
The shape of the pyramid depicts the volume of information at different levels. From the lower level to the upper level, the information amount is reduced as in every level the data is processed and sent to the next upper level. For example, the bottom level of the pyramid, i.e., at the field network, the data of interest will be sensor data which is transferred to the control network. At the control network level, the data which are related to the operator, for example, the control loop performance, will be transferred to the next level. At the top level of the pyramid, the main interest will be the data that provides information related to the quantity and quality of the product.
Typically an industrial plant has a mix of different industrial communica-tion protocols and these industrial protocols are usually common across several industries. These industrial communication protocols require specific hardware and software for robust and reliable operations inside the plants. There are many protocols that exist and are used in the industrial communication
mar-2.2 Wireless in Automation 13
ket. The three most dominant protocols are Foundation Fieldbus, Profibus and Profinet. Foundation Fieldbus is broadly used in the United States. Profibus and Profinet are preferred in Europe. The total installed base is in the order of one hundred million devices and is increasing [3]. Some of the industrial communication protocols such as the Distributed Network Protocol 3.0 and Modbus were originally developed to run over a serial connection. Later, these were adapted to run on top of the TCP/IP stack as application layer proto-cols [6]. Therefore, many of these industrial and proprietary protoproto-cols lack proper security measures in terms of authentication or integrity checking and do not support any cryptography mechanisms.
2.2 Wireless in Automation
Wireless technologies have been used in industrial plants for quite some time. In the higher level of the communication architecture of industrial automation, Wireless LANs, long-haul wireless links are commonly found. On the field network level, low rate and short distance wireless technologies are suitable communication technologies as the applications support low rates. However, in the field level application also Wireless LANs are being used. For factory automation ABB developed the Wireless Interface to Sensors and Actuators (WISA) [7] radio technology. It was released in 2001 and later WISA-COM is standardized by WSAN (Wireless Sensor-Actuator Network).
The IEEE 802.15 working group focuses on developing standards for Per-sonal Area Networks (WPAN) or short distance wireless network. Bluetooth [8] is an 802.15.1 based wireless personal network area technology. Gener-ally Bluetooth uses peer to peer communication whereas field networks some-times demand a large scale network with many sensor devices. The IEEE 802.15.4 specifies the PHY and MAC layers in the OSI model (Open Systems Interconnection model). The higher layers are specified by other standards that use 802.15.4 as base, for example, ZigBee [9], WirelessHART [10, 11], ISA100.11a [12], WIA-PA [13]. In [14], Lennvall et al. presented a per-formance comparison between WirelessHART and ZigBee standards. Their conclusion was that the ZigBee standard is not suitable in industrial environ-ments due to poor performance, and because security is optional, while in the WirelessHART standard it is mandatory. In process automation the stan-dards for industrial wireless sensor networks are WirelessHART, ISA100.11a, WIA-PA. These standards are based on IEEE 802.15.4-2006. However, Wire-lessHART, ISA-100a, and WIA-PA may merge into one industrial standard in