Pravin Karthick Ravichandran
Santhosh Keerthi Balmuri
School of Technology
Malmo University
SE-205 06-Malmo
Sweden
Master Thesis Computer Science August 2011This thesis is submitted to the School of Technology at Malmö University in partial fulfillment of the requirements for the degree of Master of Science in Computer Science. The thesis is
equivalent to 20 weeks of full time studies.
Contact Information: Author(s):
Pravin Karthick RaviChandran E-mail: rpravink@gmail.com Santhosh Keerthi Balmuri
E-mail: santhoshkeerthi@gmail.com University Advisor: Annabella Loconsole E-mail: Annabella.Loconsole@mah.se School of Technology External Advisor(s) :
Swedish Armed Forces (SWAF), Enköping Dan Ahlström E-mail: dan.ahlstrom@mil.se Ross W Tsagalidis E-mail: wross@tele2.se University Examiner: Jan Persson E-mail: jan.a.persson@mah.se School of Technology Malmo University SE-205 06, Malmo Sweden Phone: +46 (0) 40 - 665 70 00 Internet: http://www.mah.se/english/Schools-and-faculties/School-of-Technology/
i
ABSTRACT
Cloud Computing (CC) is one of the fast growing computer network technologies and many companies offer their services through cloud network. Cloud Computing has many properties with respect to the existing traditional service provisions like scalability, availability, fault tolerance, capability and so on which are supported by many IT companies like Google, Amazon, Salesforce.com. These IT companies have more chances to adapt their services into a new environment, known as Cloud computing systems. There are many cloud computing services which are being provided by many IT companies.
The purpose of this thesis is to investigate which cloud environment (public, private and hybrid) and services (Infrastructure as a Service, Software as a Service, and Platform as a Service) are suitable for Swedish Armed Forces (SWAF) with respect to performance, security, cost, flexibility and functionality. SWAF is using private (internal) cloud for communications where both sensitive and non-sensitive information are located in the internal cloud. There are problems like maintenance of hardware, cost issues and secure communication while maintaining the private cloud. In order to overcome those problems we have suggested a hybrid and community cloud environment and SaaS, IaaS, PaaS services for SWAF.
For suggesting these cloud environments and cloud services we have performed a literature study and two empirical studies (survey and interviews) with different organizations.
A new cloud model is designed based on the suggested cloud environment, separate storage spaces for sensitive and non-sensitive information, suitable services and an effective infrastructure for sharing the internal information for SWAF.
Keywords: Cloud computing, private cloud, public cloud, hybrid cloud, Infrastructure as a Service (IaaS), Software as a Service (SaaS), Platform as a Service (PaaS), and VPN.
iii ACKNOWLEDGEMENT
First of all we thank to holy God who showered their blessing on us. We would also like to express our heartiest gratitude to our academic supervisor Senior Lecturer Annabella Loconsole at Malmö University of Computer Science Department, for the invaluable insights, motivation and guidance throughout the thesis work. We must be thankful for her suggestions, comments and the way of supervision that lead to present our thesis at Malmö University, 2011. We would also thank Dan Ahlström and Ross W Tsagalidis from Swedish Armed Forces (SWAF) for giving us an opportunity to work on this interesting as well as challenging topic under their keen guidance and support through the end of this thesis work.
I, Santhosh Keerthi Balmuri would be very thankful to my father B.Kamalakar Rao, mother B.Jyothi and my sisters B.Sandeepthi, J.Mounika for supporting me throughout the carrers. Finally I thank my lovely husband Ashok Nimmala, who had encouraged and supported me in my thesis work during Master's Programme.
I, Pravin Karthick Ravichandran would like to thank my mother Vijayalakshmy RaviChandran and my sister Ind Pradha RaviChandran for supporting me all through the years. I also thank all my friends for influencing me in a positive way towards my education.
v
CONTENTS
ABSTRACT...i ACKNOWLEDGEMENT...iii ABBREVATIONS...viii LIST OF TABLES……...ix LIST OF FIGURES………...x1 INTRODUCTION………1
1.1 Problem Description………...………...1 1.2 Related Work ...………1 1.3 Objective………...……....2 1.4 Motivation……….3 1.5 Research Questions………...3 1.6 Expected Results………...31.7 Contribution of our work………..3
1.8 Outline of Thesis………...4
2 CONTEXT OF THE MASTER THESIS PROJECT………...5
2.1 About SWAF……….5 2.1.1 Product ……….………....5 2.1.2 Process ……….………5 2.1.3 Practices ……….………..6 2.1.4 People ……….……….6 2.1.5 Organization ……….………...6 2.2 Selection of Topic………7
2.3 Problems in the Present Environment………...6
vi
3 THEORETICAL BACKGROUND………9
3.1 Introduction to Cloud Computing……….………9
3.1.1 Definitions of cloud computing …..……….…………9
3.1.2 Public cloud……….……….……..…11 3.1.3 Private cloud………...11 3.1.4 Hybrid cloud……….…..12 3.1.5 Community cloud………...12 3.2 VPN tunnels………..………..13 3.3 Cloud services……….…13 3.3.1 IaaS………..…...15 3.3.2 PaaS………...……..………...16 3.3.3 SaaS………...……….17
3.3.4 Properties of cloud services………18
3.3.5 Benefits of Cloud computing services………....20
3.4 Comparison of cloud environments………20
3.4.1 Definition of requirements……….21
3.4.2 Comparison of the cloud environments with the requirements…………..21
3.5 Benefits of cloud computing………...…23
3.6 Limitation of cloud computing……….………..23
3.7 Source Selections………24
3.8 Summary of Literature Study………..24
4 RESEARCH METHODOLOGY……….……….26
4.1 Research Design…….……….26 4.2 Survey process………...……….28 4.2.1 Survey objective………..…...28 4.2.2 Survey preparation……….………28 4.2.3 Survey participants……….28vii 4.2.4 Execution………28 4.3 Interview process………...……….29 4.3.1 Interview objective……….29 4.3.2 Interview preparation……….29 4.3.3 Interview participants……… 29 4.3.4 Execution………...……….29
4.4 Instruments used for survey and interview……….30
4.5 Threats to validity………..……….30
5 RESULTS OF THE EMPIRICAL STUDY……….32
5.1 Results of the survey………...………32
5.1.1 Summary of the survey………...………39
5.2 Results of Interview study……….…..40
5.2.1 Summary of the interview………..42
5.3 Discussion……….….…….43
5.3.1 Discussion of Qualitative and Quantitative data ...….…...44
5.3.2 Discussion of survey and interview………44
5.3.3 Suggesting the cloud environment……….45
6 PROPOSED MODEL FROM THE ACHIEVED RESULTS………49
6.1 Inputs used for designing the new cloud model
...
496.2 Model design………...………49
6.3 Analysis of design model………...……….52
6.4 Suggestion given by SWAF………....53
7 CONCLUSION AND FUTURE WORK………...…...55
7.1 Summary……….55
7.2 Answering the research questions………...56
viii
References………..58
Appendix 1……….65
ix ABBREVATIONS
IT - Information Technology
SWAF -SWedish Armed Forces (Försvarsmakten) FMKE - FörsvarsMaktens enhet för Konceptutveckling (Armed Forces Unit for concept development).
CC - Cloud Computing
IaaS - Infrastructure as a Service PaaS - Platform as a Service SaaS - Software as a Service VPN - Virtual Private Network
VINCI -Virtual Interacting Network CommunIty
ICT - Information and Communication Technology infrastructure SOAP - Simple Object Access Protocol
REST - Representational State Transfer XML - eXtensible Markup Language PHP - Hypertext Preprocessor HTTP - HyperText Transfer Protocol
x
LIST OF TABLES
Table 1: Classification of Requirements/Problem/Motivation………...7
Table 2: Comparison between Traditional software and software as a service………17
Table 3: Properties and different cloud computing service providers………..20
Table 4: Comparison of cloud environments………22
Table 5: Mapping of Research Process and Research Methodology………27
Table 6: Instruments used in our research……….…...30
Table 7: Employees working on CC in the organizations………....33
Table 8: Values for the factors according to the rank scale...36
Table 9: Interview Results………43
Table 10: Comparison of the results of Survey and Interview ……….……...…….45
xi
LIST OF FIGURES
Figure 1: Basic block Diagram for Cloud Computing Environments and Services..…...……10
Figure 2: Companies providing Cloud Computing Services………....14
Figure 3: Useful of different Clouds with the services……….18
Figure 4: Research Methodology ……….26
Figure 5: Excerpt of the online survey………...…...32
Figure 6: Rating the reasons for shifting to CC....………....34
Figure 7: Usage of Cloud Environments………...34
Figure 8: Priority of cloud environments………..35
Figure 9: Rating for the factors of public cloud………36
Figure 10: Rating for the factors of private cloud………...37
Figure 11: Rating for the factors of hybrid cloud……….37
Figure 12: Usage of Cloud Service Models………..38
Figure 13: Rating for IT Services/Applications to be outsourced by Cloud Providers………39
1
CHAPTER 1
INTRODUCTION
Cloud computing is the internet-based computing, where users can share resources, information and software. The recent development of Cloud Computing provides a motivation for organizations to outsource their Information and Communication Technology infrastructure (ICT). The data centers required for Cloud Computing are growing exponentially. This work describes how the large scale organizations like SWedish Armed Forces (SWAF) can use cloud computing effectively by suggesting them the services and cloud environments with respect to performance, security, cost, flexibility and functionality.
1.1 Problem Description
Cloud Computing plays a vital role in most of the internet based technologies, where we need secure transmission of data. Cloud Computing is changing the IT architectural solutions which are kept forward by means of data storage, local networks and software. In cloud computing technology, it is a challenge to manage security issues, high performance and to have different functionalities for cloud environments. It is also a challenge to provide a cloud service with high security, affordable cost, and high performance. Furthermore, an important decision is which type of cloud environment could be used (internal, external, hybrid, or community cloud environment) [14].
SWAF is currently using private cloud environment, where the same infrastructures, platforms and software are placed in all the centers (Ex: Stockholm, Malmö, Enköping, etc.) of SWAF. This leads to several processors, servers, security and network communication to be maintained by SWAF, thus resulting high cost. In order to overcome these issues, we are going to suggest a suitable cloud environment with respect to cost, security, performance, flexibility and functionality. In this work, we also propose a design of a cloud model for SWAF, which can also be used by other large scale organizations. With this new model, data and applications in SWAF can be managed and maintained securely with better performance and functionality.
SWAF is also handling several problems like troubleshooting software, extending the license of the product, hiring more employees to recover the technical problems, etc. caused by the internal cloud services. To maintain and manage these services, SWAF needs to have more funding and increased man power. In order to overcome these issues we have done a literature and empirical study on different cloud environments (public, private and hybrid cloud) and cloud services (Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (PaaS)) and described different cloud service providers with respect to their properties. In this way, SWAF can consider one or more services to be outsourced from cloud service providers. The services could be maintained and managed by the cloud providers securely.
1.2 Related work
Much of the focus in this report was the study of different cloud environments such as public cloud, private cloud and hybrid cloud. Ruan Gaofeng [16] tells how public cloud computing infrastructure could be used at low cost (is one of the factor used to suggest the cloud environment), low technical barriers and high diversity with multimedia technology. Lori M. Kaufman [17] explained the security and privacy issues of public cloud and mentioned that, because of thwart attacks in public clouds, many of the organizations ultimately need to move the traditional perimeter security approaches to the private virtual machines. Alexandra Loosup et al. [55] tells that Cloud computing services were designed to replace the small-to-medium size enterprise data centers; performance wise, workloads often require High-Performance Computing (HPC) or High-Throughput Computing (HTC)
2
capabilities. Another report on private cloud is described in [21], in which Jingyu Ding proposed a framework of data center consolidation by comparing the different VPN (Virtual Private Network) implementation technologies. For national security purposes, Anya Kim et al. [2] had proposed a national security hybrid cloud architecture that consists of private cloud, public cloud and community cloud. Sang-Ho Na [22] proposed a generalized security framework for hybrid cloud computing using hybrid cloud model. A hybrid cloud is composed of online storage (reliable and secure place to store data), online desktop (access anywhere we can connect to the Internet) and web based applications (like Google docs) for fast processing and to free up resources when needed. While designing a new cloud model, the main constraint is the placing of database in particular layer of the data model. In general, there are three levels of data modeling such as conceptual data model (identifies the highest-level relationships between the different entities), logical data model (includes all entities and relationships among them), and physical data model (represents how the model will be built in the database and shows all table structures, including column name, column data type, column constraints, primary key, foreign key, and relationships between tables) [78]. Lomet [57] has proposed an approach, where the storing of data in database is done with two layers called as “transactional component” (works in logical level) and “data component” (works in physical level). These two components support a record oriented interface that provides atomic operations. Separating Transactional component functionality from Data component functionality enables cloud platforms to support transactions with much greater flexibility. Another report presented by Hassan Takabi et al. [3] gives an overview of cloud computing and its features with their security implications. They discussed some of the security threats and proposed a security framework for cloud computing environments.
Ramgovind et al. [1] describes the different types of clouds, services (IaaS, SaaS, PaaS) and the security concerns that should be properly addressed and managed. By comparing the cloud models and delivery models with respect to cost, performance, functionality and security requirements, the vendors and organizations become more confident in promoting highly protected safe cloud framework. Zhibin Chen et al. [4] have discussed security issues and defined a solution to encrypt the data and make it secured. Rather than acquiring and managing own physical infrastructure, a community defines a virtual Information and Communication Technology (ICT) infrastructure, by instantiating and interconnecting virtual machines (VMs) defined from a small set of standards. While using internal cloud services of the organization, servers and memory systems are almost always purchased to meet projected capacity needs, not current needs. At last, an ample percentage of acquired resources are always wasted until the company grows into them [56]. Instead, outsourcing infrastructure enables IT departments to focus on strategic ideas that add value and create competitive advantage, rather than getting delayed in the daily information of managing servers. As a result this provides greater flexibility while outsourcing the services.
In the above related literature, authors had explained about specific cloud environment with specific factor and about the developed framework in particular cloud environment. In this thesis, cloud environments and cloud services will be explained with all the factors such as cost, security, performance, functionality and flexibility. Based on this description we will be deciding the suitable cloud environment for SWAF.
1.3 Objective
The main goal of our project is to suggest a suitable cloud environment and services for the large scale organization, here we have chosen SWedish Armed Forces (SWAF) by considering the requirements (performance, security, cost, flexibility and functionality) given by SWAF and to do a detailed study on cloud environments and cloud services.
3
Sub goal 1: Suggest a suitable cloud environment (Public cloud, Private cloud and Hybrid cloud). Sub goal 2: Suggest the suitable cloud services (IaaS, PaaS, and SaaS).
Sub goal 3: Propose a new cloud model to substitute the existing model, after identifying the above cloud environments and services.
1.4 Motivation
For SWAF, it is needed to have a suitable cloud environment and a model to implement this cloud environment. By doing this research we would propose a secure computing environment by considering all the requirements for large amount of computing and storage data for SWAF.
1.5 Research Question
RQ 1: Which environment (public cloud, private cloud and hybrid cloud) would be suitable for SWAF with respect to performance, security, cost, flexibility and functionality? RQ 2: How the services Infrastructure-as-a-Service (IaaS), Software-as-a-Service (SaaS),
Platform-as-a-Service (PaaS) could be used and how these services could be firmly integrated with the suggested cloud environment by SWAF?
[Note: Above RQ1 and RQ2 are suggested by SWAF, apart from that we will also make a study on other cloud environments]
1.6 Expected Results
The expected results of our research will be a suitable cloud environment and cloud services that will be suggested to SWAF. This solution will be derived by performing the literature study and empirical study (from survey and interview). After analyzing the statistic results of empirical study, literature study and getting the requirements from SWAF, a proposal of a cloud model for SWAF will be designed to satisfy the requirements of affordable cost, greater performance, higher flexibility and functionality.
1.7 Contribution
During this thesis we made our contribution,
By presenting a literature study (section 3.8) on various cloud environments and services, large organizations like SWAF can be aware of those concepts. This study helped us to integrate the findings for designing the new cloud model. During our literature study we had enough number of articles, which motivated to do our literature work. From that we have gathered a lot of information about cloud environment, services, applications, service providers, cloud architecture and cloud management. Among several articles we have found one article discussing about the cloud environment related to defense. To be specific, the article on “Security and Architectural Issues for National Security Cloud Computing” [2] tells how the cloud computing can be used for large organizations by having a secure hybrid cloud architecture that consists of private cloud, public cloud and community cloud. But here in our research we have studied on cloud environments, cloud services, service providers and
4
about the security requirements; also we have compared all the different environments and services related to the given requirements with suitable examples.
By doing the survey and interview we will identify the suitable cloud environment and cloud services, this also answers the first research question. Several surveys and interviews are taken on cloud computing in order to manage cloud environment, cloud services and other services. But there is no survey/ interview, which contains the information about the usage of cloud environments, reason for shifting to cloud environment from this existing environment, priority of choosing Cloud Environments, selection of SPI (Software, Platform, and Infrastructure) model and about the outsourcing of IT services/applications. But, all the above mentioned information is discussed in our empirical study. This gives a suitable solution to choose the cloud environment and services with respect to performance, security, cost, functionality and flexibility for SWAF. This empirical study can also be applied for other organizations those who use/not use cloud computing.
By presenting the possible solution to the problem given by SWAF. After making it clear they can make use of those suggested cloud environment and services at their place. This solution can also be used for the other large scale organizations, those who were planning to shift their current environment into cloud.
By presenting a new cloud model, provides possible solution to a problem related to the research question. We can also use this proposed cloud model to other large scale organizations that have same or less requirements as SWAF.
1.8 Outline of Thesis
Chapter 2 describes the context of master thesis project, problems in the present environment and about the requirements/inputs given by the SWAF.
Chapter 3 describes the theoretical background of CC, and the different kinds of cloud environments and services. We also describe the benefits and limitations of CC and different cloud environments are compared to each other.
Chapter 4 explains the research methodology is used in this thesis and the reason why those specific research methods are selected. The process of survey and interview are also explained.
Chapter 5 explains the results of survey and interviews which we had conducted with several organizations, which is followed by the analysis of the results and a suggestion of a suitable cloud environment.
Chapter 6 describes the specifications and analysis of the model designed in the suggested cloud environment. And also discusses about the suggestions given by SWAF for improving the designed model.
5
CHAPTER 2
CONTEXT OF THE MASTER THESIS PROJECT
The first part of this chapter contains general information about the company and their contexts. The second part describes the research work done at the organization and about how the thesis topic has been selected. The third part describes the problems in the present environment. The fourth part describes the requirements given by SWAF.
2.1 About SWAF
Cloud computing is a vast area, where it is used at profit/non-profit organizations, government, health care, defense, hospitals, businesses and for commercial(iCloud) use to store music, videos, photos, applications, documents. Among those places defense is a fascinating area, where SWAF officials are looking to move away from its decentralized network of computer servers and data centers into “cloud computing”. By start doing the research for SWAF, will also help to make use for other large scale organizations.
The SWedish Armed Forces (SWAF) is a Swedish government agency, responsible for the operation of the armed force of the realm; they are one of the biggest authorities in Sweden and are headed by a supreme commander [40]. SWAF is allocated an annual budget of about SEK 40 billion to perform its responsibilities. Around half of this goes to unit operations and the rest to research, development and the purchasing of new materials systems [41]. FMKE (FörsvarsMaktens enhet för konceptutveckling) is located at the Armed Forces development center in Enköping but receive their assignments directly from the Headquarters. The company details of SWAF are explained in the following sub sections, by complying the guidelines from [81].
2.1.1 Product
Product is the software system developed with help of the object study. In SWAF, there is no in house development process. They just buy and outsource the software and services from different service providers.
2.1.2 Process
SWAF is a large scale organization, where several processes are undertaken and dispatched by themselves. The authors of this report have been informed about the existing cloud environment, while they have not been informed about the cloud model used at the company because of security reasons. Currently company makes use of private cloud for the telephony calls, emails, and several different software systems to communicate with their peer users. They are maintaining and managing all the services inside their organization.
SWAF are maintaining and managing some of the services (like logistics, Payroll, Human resource, Supply chain management, Accounting and finance, installations of needed licensed software) internally. Because of maintaining/managing the larger infrastructure inside their organization, they have some problems in terms of cost; man power (with more technical support) and flexibility. However the services are provided from service providers, SWAF will have their own security features. Now, all the information has been placed within the firewalls. The Logistics is maintained with separate branch of technicians. At present, all the services had been centralized (maintenance and installations) by SWAF in the internal cloud.
6 2.1.3 Practices
Practices context describes the systematic approaches that are used in the organizations and also the tools and techniques which are used for the development. SWAF, do not develop software or using the CASE tools, practices, and techniques in their organization.
2.1.4 People
There are about 20000 employees working in the Swedish Armed Forces, and their units consist of 500-1000 people of which about 75 plus of employees working with IT administration. SWAF have many camps, canton and branches at Afghanistan, Kosovo and other countries (names are not specified because of some security reasons), the work of IT administration with these countries are of telecommunication and exchanging data. They manipulate all these data through the internal cloud. 2.1.5 Organization
The organization model describes how the company is organized. Here SWAF works on several units like Mechanized unit, Cavalry unit, Artillery unit, Air defense unit, Command and Control Unit, Engineer unit, Logistics unit, CBRN units, where all these units are connected to IT administration for different kind of works. All these units are operated both in Sweden and abroad.
2.2 Selection of Topic
In three occasions we interviewed the external supervisor of SWAF at Malmo University. In the first
interview we were discussing the primary tasks of SWAF and the interviewee was telling that how
they organize, train, and deploy military forces, domestically and internationally. The interviewee described the different research projects in which SWAF is involved, SWAF were undergoing several research under different topics like, Communication Security, Virtualization, Mobility, Web Security, IAM-AC (Identification Authentication Management, Access Control), MMI/MCI (Man-Machine/ Computer Interaction), Password Management, Automation, Logging, Market analysis, Security Management, INFO War, Data media UPS (Uninterruptable power supply), Cloud Computing, Risk Management, Cyber Security, Social media, Interoperability, Awareness, Information assessment, Information Quality, IT administration, Security Architecture/Design, Communication between security domains, Business Intelligence and more.
And another project is undergoing that is, PRIO by IBM. By this project they can maintain the Working time, payments, travelling etc. For these services SWAF will be getting the applications, infrastructure, and help-desk from IBM. Thus all these above topics have several research works with different research question. These research works are carried out by the Researchers of SWAF and from the students of various universities in Sweden.
After looking over the given topics we decided to choose Cloud Computing, where we have good study background and also taking into consideration that this topic could be related to our Master‟s Program. In general Cloud Computing is a broad/vast topic; it provides computation, software, data access, storage and services. On cloud computing many research works are undergoing for SWAF, among those works we were assigned for evaluating different cloud environments and services with respect to the requirements. The requirements are explained in the following,
2.3 Problems in the present environment
Then in the second interview we collected information about the problems at SWAF. SWAF is a large scale organization, where several processes are undertaken and dispatched by themselves. We got the information about the existing cloud environment and the services to be outsourced, but not the cloud model because of some security reasons. Currently SWAF are using private cloud for communication, where both sensitive and non-sensitive Information are located in the internal cloud.
7
Also they are maintaining and managing all the services inside their organization. They are having 25 to 30 data-centers located in Sweden. Most of the local data centers are moving to central places. SWAF is also handling with other problems like troubleshooting software, extending the license of the product, hiring more employees to recover the technical problems, etc. caused by the internal cloud services. In the existing cloud environment, SWAF had a specific functionality but they require in-sourcing (Finance, ERP and Human Resource) and outsourcing (email, conferencing, social media and travel) functionality in one cloud environment.
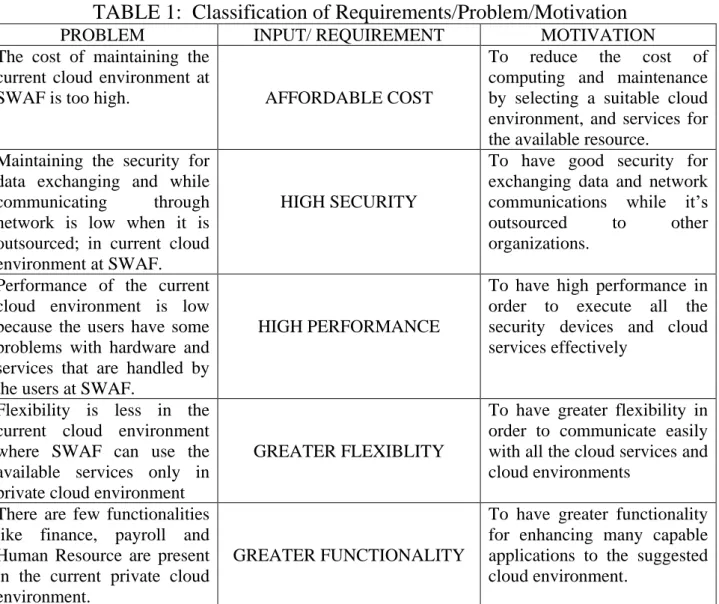
This following table describes the problems of current cloud environment (private cloud), input/requirements and motivation for selecting the requirement.
TABLE 1: Classification of Requirements/Problem/Motivation
PROBLEM INPUT/ REQUIREMENT MOTIVATION
The cost of maintaining the current cloud environment at
SWAF is too high. AFFORDABLE COST
To reduce the cost of computing and maintenance by selecting a suitable cloud environment, and services for the available resource.
Maintaining the security for data exchanging and while
communicating through
network is low when it is outsourced; in current cloud environment at SWAF.
HIGH SECURITY
To have good security for exchanging data and network communications while it‟s
outsourced to other
organizations. Performance of the current
cloud environment is low because the users have some problems with hardware and services that are handled by the users at SWAF.
HIGH PERFORMANCE
To have high performance in order to execute all the security devices and cloud services effectively
Flexibility is less in the current cloud environment where SWAF can use the available services only in private cloud environment
GREATER FLEXIBLITY
To have greater flexibility in order to communicate easily with all the cloud services and cloud environments
There are few functionalities like finance, payroll and Human Resource are present in the current private cloud environment.
GREATER FUNCTIONALITY
To have greater functionality for enhancing many capable applications to the suggested cloud environment.
2.4 Requirements of SWAF
Then during the third interview we collected the requirements for suggesting the cloud environment and services. Currently SWAF is using Private cloud; there are some problems (table1) like hardware maintenance, cost issues, and flexibility in the environment. In order to overcome those problems SWAF has given requirements (like High Performance, High Security, Affordable Cost, Greater Flexibility and More functionality) for suggesting a suitable cloud environment for their organization.
8 REQ1: To decrease the cost of maintenance of the cloud environment compared to the actual maintenance cost
REQ2: The security of the cloud environment shall not degrade if the company changes to the new cloud model and outsource services.
REQ3: The cloud model shall have higher performance when outsourcing the services, compared to the performance of the current cloud model. This can be done by outsourcing high speed processors for the computer systems.
REQ4: The cloud model shall offer more functionalities compared to the model used today, for instance by archiving information, backing up functions and by allowing local data to replicate a public cloud.
REQ5: The cloud model shall offer higher flexibility compared to the flexibility offered with the actual cloud model. This can be done by outsourcing the infrastructure, instead of managing and monitoring the services inside the organization.
However the services are provided from service providers (section 2.3), SWAF will have their own security features. Now, all the information is placed within the firewalls. The Logistics is maintained with separate branch of technicians. At present, in the private cloud everything had been centralized (maintained and installed) by SWAF. External Advisor specified that, SWAF wants public net, restricted net (private), security net in one server which is maintained by SWAF users. They have also asked to implement the VPN tunnels (see chapter 2.2) in our new proposed system. The following characteristics are listed for selecting the CC-environment such as, Conceptional characteristic – service oriented, Economic characteristic – pay-per-use model, where the user can pay for processing, storage and network on their usage, Virtualization and Security characteristics
9
CHAPTER 3
THEORETICAL BACKGROUND
This chapter describes the definitions of cloud computing (under section 3.1.1), it explains the different types of cloud environments (such as public, private, hybrid and community clouds, see section 3.1.2, 3.1.3, 3.1.4, 3.1.5), cloud services (IaaS, PaaS and SaaS) under section 3.3 and VPN tunnels (for connecting to a private local area network at remote location) which is used for security purpose. VPN tunnels are used to connect the systems located in remote or local area through a secured communication. VPN tunnels are described in this chapter (see section 3.2) because it will be used in our proposal of cloud architecture, in chapter 5. In section 3.3.4 properties of cloud services are explained briefly and different cloud providers (like Amazon Web Services, GoGrid and more) are compared with the properties of cloud services. Thereafter, different cloud environments are compared (see section 3.4); benefits and limitations of CC are listed (see sections 3.5 and 3.6).
3.1 Introduction to Cloud Computing
Cloud Computing delivers services dynamically over the internet. Storage, Operating system, Hardware, Software and other resources helps in keeping the company‟s IT budget to bare minimum cost [15]. CC also refers to both the applications delivered as services over internet and the hardware and software systems in the data centers. It provides services like IaaS (Infrastructure as a Service), SaaS (Software as a Service), and PaaS (Platform as a Service). CC clients have to trust 3rd party cloud providers on many sides, especially on the availability of cloud service as well as data security. The main focus of the thesis is on public, private and hybrid clouds. However there is other kind of cloud environment like community cloud. These models are explained in the following sections. To summarize, in the cloud deployment model, networking, platform, storage, and software infrastructure are provided as services that scale up or down depending on the demand. By deciding which type of Cloud to deploy, SWAF needs to assess different parameters (like cost, flexibility, security, performance and functionality) from an architectural point of view.
3.1.1 Definitions of cloud computing
The data center‟s hardware and software is what we call “cloud”. Cloud computing is a new model of computer infrastructure and application services. CC has gained rapid improvement on a global scale. A cloud offers customers the ability to start businesses without having to pay huge upfront capital expenses to the services provided by different cloud providers [17]. Major Service providers in this field are Amazon's EC2 [8], IBM's Smart Business cloud offerings [10], Microsoft's Azure [11], and Google's AppEngine [9]. There are many definitions of CC given by cloud experts and organizations, such as the following,
“Gartner”- Cloud computing is a style of computing where massively scalable IT-related
capabilities are provided as a service across the Internet to multiple external customers [51].
“IBM” - A cloud computing platform dynamically provides, configures, reconfigures, and
deprivations servers as needed. Cloud applications use large data centers and powerful servers that host web applications and web services [52].
“Wikipedia” - A style of computing in which dynamically scalable and often virtualized resources
are provided as a service over the Internet [53].
“451 Group”- The cloud is IT as a service, delivered by IT resources that are independent of location
10
“National Institute of Standards and Technology” - A model for enabling convenient, on-demand
network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction [2].
In this section, we describe the benefits of cloud computing, that is, the application of cloud computing for SWAF by analyzing the work done by the U.S military cloud environment. Their cloud computing definition is much broader, which only refers to “the use of cloud computing technology and techniques for the support of localized and short-lived information access and processing requirements” [12]. They concentrates on cloud computing in a military environment, supporting series of tasks and/or engagements in real-time within a tight Observe, Orient, Decide, and Act (OODA) loop [18]. Cloud computing will also be valuable to use in the military operational and strategic level defense processes, but the environment‟s special limitations and constraints pose a more difficult problem requiring special consideration.
The following figure 1 shows the basic blocks for computing the cloud environment and services. They have three delivery models (Cloud Infrastructure as a Service (IaaS), Cloud Platform as a Service (PaaS), and Cloud Software as a Service (SaaS), and four deployment models Private cloud, Public Cloud, and Hybrid Cloud and Community cloud computing.
Figure 1: Basic block for Cloud Computing environment and services
Cloud computing builds on the advancements in virtualization technology, grid computing, SOA (Service Oriented Architecture) and web services technologies. Apart from proposing a design model we need to evaluate how cloud computing can increase the effectiveness of the military missions. This evaluation may be done by collecting relevant data from different environments and comparing with each other, then proposing a suitable infrastructure and deployment model for SWAF.
11
3.1.2 Public cloud
Public cloud (which is also called external cloud) allows users to access the cloud via interfaces. Public clouds are less secure than the other cloud models and one has to ensure that all applications and data accessed on the public cloud are not subjected to malicious attacks [1]. Performance is one of the main concern in public cloud computing. Key issues when subscribing to a public cloud is that we have little control over the public cloud architecture, performance (which can be variable -capable to change) [58] and sharing resources compared to other cloud environments. By using public cloud we can avoid the costs of building and maintaining a private storage infrastructure, opting instead to pay a service provider for the services which are accessed by the users. This feature enables a greater functionality by providing the benefits of availability (access data from anywhere) and reliability (not to worry about the backup of data).
Ruan Gaofeng [16] tells how public cloud computing infrastructure could be used at low cost, low technical barriers and high diversity with Multimedia technology and concludes that by achieving “the resources and procedures storing and running on cloud share the same human-computer interaction interface” and this approach is clearly more flexible to achieve, it is easier and cheaper. Public-cloud providers typically provide the environment; applying traditional perimeter-security approaches will increase their potential for exploitation. Due to thwart attacks in public clouds [17], we need to move the security from the edge of the public cloud to the Virtual Machines. The public cloud offers user access via the Internet, and cloud subscribers perform administrative activities (knowledge management, e-record service, payroll, accounting and finance, human resource, and project management) in this environment. This paradigm in itself introduces security risks because this remote access provides exposure to potential cyber attackers. Although these vulnerabilities increase the threat space, other concerns pose an equal, if not greater, security threat. For instance, in public Cloud organizations no need to pay a large upfront cost (e.g., for hardware purchase) before launching services, or over-provision to accommodate future or peak demand. Instead, the cloud‟s pay-as-you-go charging model enables the customer to pay for what he/she actually uses and promises to scale with demand [19].
3.1.3 Private Cloud
A private cloud (which is also called internal cloud) is set up within an organization‟s internal project datacenter. Private computing is easier to align with security, compliance, and a regulatory requirement, compared to other cloud environments, and provides more enterprise control over deployment and use. In private cloud computing the performance levels of the application services such as Windows Azure, Office 365, Xbox Live and Bing services can be optimized. This benefit of Private cloud can be useful to every IT environment and has the new features like processing troubleshooting, immediate deployment and general visibility of the services [59].
Private cloud computing is used by many organizations. Private small-cloud computing is based on three concepts: small clusters, virtualization, and general graphics processor. Private cloud can be replaced instead of cluster computing, grid computing and distributed computing to avoid the high cost of data delivery [20]. Jingyu Ding [21] proposed a framework of data center consolidation by comparing the different VPN implementation technologies. This cloud infrastructure is owned or leased by a single organization and is operated solely for that organization. Here the Private cloud is composed by two types of resources: the resource manager and the network resource manager. These resources extend private cloud to enterprise cloud computing (is a controlled, internal place that offers the rapid and flexible provisioning of compute power, storage, software, and security services by meeting the organization requirements) by adding virtual private computing and virtual private network resource [79]. Where the virtual private computing is mostly kept in public cloud companies and virtual private computing resources are connected securely to the enterprise infrastructure via virtual private network provided by telecom carriers.
12
High Scalability and Flexibility for Private Cloud Computing are provided by Eucalyptus 2.0 (infrastructure software that enables organizations to deploy scalable private and hybrid cloud computing environments within a secure IT infrastructure) [60]. Amazon extends the functionality of private cloud by widening the networking options and allows customers to specify which of their VPC (Virtual Private Cloud) resources they wish to access directly through the Internet [61].
3.1.4 Hybrid Cloud
In the hybrid cloud (which is also called personal cloud), scalable resources and virtual application provide virtual IT solutions through a mix of both public and private clouds. Hybrid Clouds provide more secure control for data and applications and allow various parties to access information over the Internet. It also has an open environment that allows to interfaces with other management system. Hybrid cloud makes the customers agree to a viable and cost-saving methodology to make a great use of public cloud services along with their private cloud services. The cost factors are measured by considering the bandwidth, storage, power, cooling, physical plant, and operations of the organization [62].
The composition of two or more clouds in which one has to be public and another has to be private cloud (private, public or community) is called Hybrid cloud. Most of the users believe that personal clouds are private clouds. But a Personal Cloud is the hybrid deployment model that combines a private cloud and a public cloud [22]. Sang-Ho Na proposed a generalized security framework for personal cloud computing using personal cloud model. Personal cloud is of online storage (which is a reliable and secure place to store data), online desktop (which allows access anywhere we can connect to the Internet) and web based applications (Google docs). These connections free up resources and processing power.
In this environment the performance will be neutral while accessing the applications and services. Also the hybrid cloud exploits flexibility in the organization, as it can be a composition and combination of at least one private cloud and at least one public cloud. This environment provides more prominent functionality by archiving information, backup functions and allowing local data to be replicated to a public cloud.
Many organizations and Defense departments are using hybrid cloud which consisting of private and public clouds. For national security purposes, Anya Kim et al. [2] had proposed a national security hybrid cloud architecture that consists of private clouds for sensitive, non-shared information; public clouds for information gathering, dissemination of public information; community clouds for information sharing and collaboration needs. And Anya Kim discussed private and public clouds, but focus here is on national security community clouds, the security requirements and features of community cloud.
3.1.5 Community Cloud
A Community Cloud is not open to the general public; it is available only to the followed members of a community, it can be set up where the organization has similar requirement at all their branches and for sharing their infrastructures. Community Cloud Computing has the advantage of no control of vendors in Cloud Computing. Compared to other cloud, Community Cloud is as much a social structure as a technology paradigm, because of the community ownership of the infrastructure [43]. An example is Wikipedia adopts Community CC; it would be dispersed throughout the Community Cloud alongside other services, which in this environment can be as simple as a webpage or complex. Examples of complicated tasks, such as editing a Wikipedia page, will require an update to the distributed storage of the Community Cloud, achieved by transmitting the new data through its network of nodes, most likely resulting in an eventual consistency mode. We can secure the
13
community cloud by using Virtual Interacting Network Community (Vinci) [46]. Vinci is a software architecture that aims to increase the shared applications to be secured on a cloud. Vinci architecture exploits multi-core processors and virtualization to share in a secure way an ICT infrastructure among users with distinct trust levels and reliability requirements. Vinci partitions users into several communities, according to the user privileges and to the trust level of the applications the user executes. For each community, Vinci defines a distinct security policy for accessing the resources. Instead of acquiring and managing own physical infrastructure, a community defines a virtual Information and communication Technology (ICT) infrastructure. Vinci includes template to run user applications protect shared resources and control traffic among communities to filter out malware or distributed attacks, each of these templates are related to a specific application or system functionality.
Community cloud computing do not consider the monetary cost when accessing resources, it is made in a pay-as-you-go manner [45]. When a service is needed to fulfill a request, even without proper instantiation on a suitable node, a copy should be retrieved from the repository and instantiated as needed. This allows for flexible responsiveness and resilience to irregular traffic spikes (a transient variation) [43]. Community cloud-based applications and resources can reduce costs, improve performance, ease troubleshooting, and enhance privacy and control [63]. Community clouds have a significant performance over the public cloud by providing their associates with both high-performance bandwidth and latency.
Community cloud is a resources community formed by services, hardware resources and other network resources for organizations such as enterprises and institutions. Community cloud users can easily use the services of resources from different members, without knowing the specific location where the service is running [45]. Community Clouds will probably require more bandwidth than vendor Clouds (such as Google, Amazon and Microsoft), but can take advantage of the ever-increasing bandwidth and deployment of broadband.
3.2 VPN Tunnels
The study of VPN Tunnels is made in this section because it is used to gather the security requirements for designing new cloud model with different cloud environments and services, in chapter 5.
A Virtual Private Network (VPN) is a private network on a public network infrastructure (Internet). We can use VPN connectivity for connecting to a private local area network at remote location. It is frequently used in the organization with remote offices to share network resources and private data. A VPN can be a good security solution for a large company; especially its IT department can preinstall VPN clients on the employees‟ laptops. The VPN secures the network connections from the laptops all the way to the VPN server on the company network.
The basic building block of VPN is the tunnel. “VPN tunnels are often used to connect employees to
their organizations intranet. One end of the tunnel is a VPN software client on the employee‟s laptop while the other end is the VPN server software running on the organizations computer” [49]. Secure
socket layer (SSL) VPN is a secure remote access solution based on SSL [47] protocol, and performs rapidly. SSL tunnel is the overlay networking facility for creating a SSL VPN on top of existing Internet or IP based network. The key factor of using VPN is for minimizing the cost [48].
3.3 Cloud services
Cloud computing is an on demand service. The client just need to have a computer and internet access, everything from services to the maintenance of the services are managed by the provider. Cloud computing has new services which provides benefits, such as cost reduction, high availability,
14
scalability, fault-tolerance capability and so on. The cloud computing services involves three roles, such as
Cloud provider - Some organizations (like Amazon) [30] rent or lease the resources like storage, servers, etc. for their needs, such organizations are known as cloud providers.
Service provider or cloud consumer - The organizations who rent these resources become cloud consumer and some of the organizations will build applications based on the rented resources which further offer different services to end users, then they are known as service providers.
Service consumer - The end user using the services are known as service consumer.
There are many services that are provided by cloud computing providers, such as Infrastructure as a Service (IaaS), Network as a Service (NaaS), Platform as a Service (PaaS), Data as a Service (DaaS) and Software as a Service (SaaS). These services are further divided into three levels, such as hardware level - IaaS, NaaS; application level – DaaS, SaaS and system level - PaaS. There are many companies like Google, Amazon EC2, salesforce.com and many more that provide the services of cloud computing.
Figure 2: Example of Companies providing Cloud Computing Services [38]
In this thesis, we had selected three services such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS) and Software as a Service (SaaS) which are mostly used by different organizations and could also be used by SWAF. While computing the cloud, SaaS is broadly used when compared to PaaS, DaaS and NaaS. Network as a Service is a more recent term, originally used in the IT and cloud computing context but now being increasingly applied in the mobile world. As SWAF is a defense organization, it could be difficult to maintain the entire infrastructure and to build the software applications on different platforms as needed to SWAF. By outsourcing the IaaS, SaaS and PaaS to different IT organizations like Microsoft, IBM and more, SWAF can reduce the technical work and cost. DaaS is not mostly considered because the service providers offering SaaS are also offering a layer known as DaaS. Like example, providers such as Salesforce.com, which offer CRM Software-as-a Services (SaaS), over the internet, have been building out their own cloud platform to offer new services including a new DaaS layer called Database.com and other emerging platforms
15
are designed to allow apps to run natively on any device. Apart from that SWAF are having their own data center in Sweden, also they are having their own localized database at all their branches with database managing and monitoring group. Whether it is a sensitive or non-sensitive data they want to maintain their data by themselves. In figure 2, we can see some companies which use the above mentioned cloud computing services for the organizations.
3.3.1 Infrastructure as a Service (IaaS)
Infrastructure as a service is an IT solution which tackles the hardware concerns (like reducing infrastructure cost, maintenance of different resources and security) of an organization. IaaS is the delivery of computer hardware as a service. It is a one of the cloud layer in CC which minimizes the need for investments in computing hardware components like servers, storage capacity, memory capacity, network, load balancing, firewalls and so on. It is characterized by the concept of resource virtualization which allows customers to deploy and run their own guest operating system on top of the virtualization software offered by the provider [23]. Virtualization meaning is that the user or consumer can select a configuration of CPU, memory and storage which could be optimal for their application. There are many companies that provide infrastructure as a service such as Amazon EC2, Mosso, Sun, VMware, etc.
Advantage and Disadvantage
The advantage of infrastructure-as-a-service is that companies can access the expensive data center resources by a rental arrangement and do not need to worry in managing, replacement of disk drives and networking issues. The disadvantage of IaaS is there is less granular on-demand expandability of the resource (organizations cannot instantly increase the resources like storage, memory and more). Some of the providers of Infrastructure-as-a-service are briefly explained, such as Amazon and GoGrid [75].
Amazon Web Services
Amazon Web Services (AWS) provides the infrastructure web services platform in the cloud to different organizations. Some of the infrastructure services offered by amazon are: Amazon CloudFront – it is a web service that provides a high performance and delivers the content globally; Amazon EC2 (Elastic Compute cloud) – provides the computing capacity; Amazon SimpleDB (Database); Amazon S3 (Simple Storage Service); Amazon VPD (Virtual Private Cloud) – these are secure and seamless bridge between a company‟s existing IT infrastructure and AWS cloud. Examples of services offered to different organizations by AWS are the following: a pharmaceutical company can rent computing power to execute large-scale simulations, Media Company can serve unlimited videos and music, an enterprise can deploy bandwidth-consuming services, an e-commerce web site can be developed without any difficulty and more examples are found in [29]. By using AWS, companies or IT developers have some benefits like; cost effectiveness, scalable, flexible, and secure. But for AWS they is no service level agreements (SLA‟s), it is only of instance service. Among the benefits, security is the important issue for all cloud service providers. In AWS, each service as different layers of security in which all the data of the customers could be more secured in all service offerings mentioned above. Amazon EC2 has multilevel security strategies, like security for host operating system, security for virtual instance or guest operating system, security for a firewall and network communication [25].
GoGrid
GoGrid [31] is the Infrastructure-as-a-service provider which manages the IT infrastructure, data centers – it shares power, cooling, security, fire suppression infrastructure with different version and 2 Megawatt generators. It provides the hosting services with secure and reliable cloud platform for the customers, who can deploy and manage the existing or new applications on servers. It provides infrastructure components like, cloud storage, cloud servers, dedicated servers and load balance
16
between servers for organizations or enterprises on on-demand access. Organizations or customers can manage and operate the infrastructure services of GoGrid through web-based interface or Application Programming Interfaces (APIs). GoGrid [31] is not responsible for any physical access or copies of software, data or content stored on GoGrid system by third parties, so the level of security and privacy is very low. When compared to Amazon EC2, GoGrid provides service on Service Level Agreements (SLA‟s) to the customers and it is less secured than Amazon EC2.
3.3.2 Platform as a Service (PaaS)
Platform as a service is the delivery of a computing platform and solution stack as a service without software downloads or installation for developers, IT managers or end users [24]. It provides self-contained platforms with all the resources that are needed for application development and operational hosting. There are some major features of platform as a service that should be delivered by the service providers in PaaS, such as design, development, deployment, integration, storage and operations. Some of the platform provider‟s will provide with full stack including an operating system, programming language, security, storage, version control, collaborative tools and tools to build web interaction. The companies that provide platform-as-a-service are for example Microsoft, Google App Engine, Force.com and Engine Yard.
Advantage and Disadvantage
The advantage [75] of platform-as-a-service is that companies or users can access a complete enterprise development environment at a low cost and build applications. The disadvantage [37] is that many of the platform-as-a-service providers purchase proprietary programming language (the programming language owned by the particular service provider) and interfaces, so once the application is there it may be difficult to move it to an on-premise server (server within the organization) or another PaaS provider. Some of the providers of platform-as-services are briefly explained, such as Google App Engine and Window Azure.
Google App Engine
Google App Engine [10] provides platform as a service, that lets the users or customers to run web application on Google‟s infrastructure, in which applications are easy to build and maintain. There is no need to maintain servers, only upload the applications to app Engine and starts to serve the users. Google App Engine supports applications written in several programming languages like, Java technologies using Java Virtual Machine (JVM), Java servlets and any other language using JVM-based interpreter such as JavaScript or Ruby and also Python interpreter. All the applications that are built on App Engine [10] are run in a secure and reliable environment. Google App Engine uses sandbox for security for separating the running programs from third party or untrusted users. Sandbox is a computer security mechanism for separating running programs and is used to execute untrusted programs from unverified third-parties and untrusted users.
Windows Azure
Windows Azure is a Microsoft cloud computing platform. It is a cloud service operating system and flexible platform that provides the developers to build, manage and store the application and run it on Microsoft data centers [11]. It supports popular standards, protocols and languages including Simple Object Access Protocol (SOAP) – it is a simple XML based protocol which lets the applications to exchange the structure information over (HTTP) [71]; Representational State Transfer (REST) – it is a software architecture for distributed hypermedia systems such as World Wide Web (WWW) [72], eXtensible Markup Language (XML) – is used to transport and store data, Java – programming language; Hypertext Preprocessor (PHP) – it is a general purpose scripting language that is especially suited for web development [73]; and Ruby – it is a dynamic, interpreted and open source programming language [74]. In Windows Azure, servers will be behind firewalls to keep the service
17
and data in a secured state. Some of the benefits of Azure are agility, efficiency, simplicity and trustworthy [11].
3.3.3 Software as a Service (SaaS)
The first implementation in cloud services was software-as-a-service. It is a multi-tenant platform and it is also knows as software on demand. It is an application hosted on a remote server which is accessed through Internet and is a low-cost way for businesses to have specialized software that multiple users can operate. It is also a model of software, where a provider licenses an application to customers as pay-per-use model [25]. SaaS runs on the hardware from the licensor or somewhere in the cloud and provides the maintenance, installation and management of the software. We can also say it is a software application functionality offered/consumed over the internet with minimal or no software installation that is required to access. Some of the providers of SaaS are Force.com, AT&T, and Media Temple and so on; most of these organizations provide hosting services.
Table 2 explains the difference between traditional packaged software and software as a service.
Table 2: Comparison between Traditional software and software as a service
[77] Traditional software (Perpetual licensing) Software as a Service (SaaS)Traditional software licensing, which involves the organizations purchasing a perpetual use of license from the software publisher and then making additional investments for hardware, installation, and maintenance.
SaaS is a service, which organizations buy a subscription to the software from service provider and the software provider runs and maintains the software on the provider‟s hardware.
Software upgrades will be done depending upon the organization usage and expenses.
Upgrades where done automatically by the service provider.
In traditional software, the data will be secured within the organizations.
In SaaS, data security is an issue because organizations or users data are stored on the service provider‟s hardware and systems. Repeatable functionality via web services,
open API‟s and standard connectors. Use open API‟s and web services to facilitate integration.
Advantage and Disadvantage
An advantage of SaaS is that it has the ability to leverage an application without having to buy and install the software. The disadvantage is that, the security burden falls on the hosting company (service provider). So, the organizations should trust the service providers to properly secure the servers on which the virtualized applications runs and the firewall controlling network security [75]. Salesforce.com
Salesforce is an organization that delivers software as a service. Salesforce [35] has a multi-tenant architecture (it provides both PaaS and SaaS) that each user‟s private source code is stored in a separate container (it has several containers maintained by sales force for different users) and is isolated from the others containers. The servers are hosted, managed and maintained by the sales force. It also includes capabilities such as middleware, security, database management, performance management and monitoring. It provides integration of a set of standardized web services APIs that enable the applications to have a common approach to access the information from one application to another. Salesforce is also a partner for Platform-as-a-Service known as Force.com.
![Figure 2: Example of Companies providing Cloud Computing Services [38]](https://thumb-eu.123doks.com/thumbv2/5dokorg/3999935.80046/27.892.81.755.501.827/figure-example-companies-providing-cloud-computing-services.webp)






