S TUDIES IN C OMPUTER SCIEN CE N O 1 2, DOCT OR AL DISSERT A TION F AHED ALKHABB AS MALMÖ UNIVERSIT
REALIZIN
G
EMER
GENT
C
ONFIGUR
A
TIONS
IN
THE
INTERNET
OF
THIN
GS
FAHED ALKHABBAS
REALIZING EMERGENT
CONFIGURATIONS IN THE
INTERNET OF THINGS
R E A L I Z I N G E M E R G E N T C O N F I G U R A T I O N S I N
T H E I N T E R N E T O F T H I N G S
Malmö University,
Studies in Computer Science No 12,
Doctoral Dissertation
© Fahed Alkhabbas, 2020 ISBN 978-91-7877-121-9 (print) ISBN 978-91-7877-122-6 (pdf) DOI 10.24834/isbn.9789178771226 Holmbergs, Malmö 2020FAHED ALKHABBAS
REALIZING EMERGENT
CONFIGUR ATIONS IN THE
INTERNET OF THINGS
Malmö University, 2020
Faculty of Technology and Society
Department of Computer Science and Media Technology
Studies in Computer Science
Faculty of Technology and Society Malmö University
1. Jevinger, Åse. Toward intelligent goods: characteristics, architec-tures and applications, 2014, Doctoral dissertation.
2. Dahlskog, Steve. Patterns and procedural content generation in digital games: automatic level generation for digital games using game design patterns, 2016, Doctoral dissertation.
3. Fabijan, Aleksander. Developing the right features: the role and impact of customer and product data in software product devel-opment, 2016, Licentiate thesis.
4. Paraschakis, Dimitris. Algorithmic and ethical aspects of recom-mender systems in e-commerce, 2018, Licentiate thesis.
5. Hajinasab, Banafsheh. A Dynamic Approach to Multi Agent Based Simulation in Urban Transportation Planning, 2018, Doctoral dis-sertation.
6. Fabijan, Aleksander. Data-Driven Software Development at Large Scale, 2018, Doctoral dissertation.
7. Bugeja, Joseph. Smart Connected Homes: Concepts, Risks, and Challenges, 2018, Licentiate thesis.
8. Alkhabbas, Fahed. Towards Emergent Configurations in the In-ternet of Things, 2018, Licentiate thesis.
9. Paraschakis, Dimitris. Sociotechnical Aspects of Automated Rec-ommendations: Algorithms, Ethics, and Evaluation, 2020, Doc-toral dissertation.
10. Tegen, Agnes. Approaches to Interactive Online Machine Learn-ing, 2020, Licentiate thesis.
11. Alvarez, Alberto. Exploring the Dynamic Properties of Interaction in Mixed-Initiative Procedural Content Generation, 2020, Licen-tiate thesis
12. Alkhabbas, Fahed. Realizing Emergent Configurations in the In-ternet of Things, 2020, Doctoral dissertation.
ABSTRACT
The Internet of Things (IoT) is a fast-spreading technology that enables new types of services in several domains, such as transportation, health, and building automation. To exploit the potential of the IoT effectively, several challenges have to be tackled, including the following ones that we study in this thesis. First, the proposed IoT visions provide a frag-mented picture, leading to a lack of consensus about IoT systems and their constituents. To piece together the fragmented picture of IoT sys-tems, we systematically identified their characteristics by analyzing exist-ing taxonomies. More specifically, we identified seventeen characteristics of IoT systems and grouped them into two categories, namely, elements and quality aspects of IoT systems. Moreover, we conducted a survey to identify the factors that drive the deployment decisions of IoT sys-tems in practice. A second set of challenges concerns the environment of IoT systems that is often dynamic and uncertain. For instance, due to the mobility of users and things, the set of things available in users’ environment might change suddenly. Similarly, the status of IoT systems’ deployment topologies (i.e., the deployment nodes and their interconnec-tions) might change abruptly. Further, environmental conditions moni-tored and controlled through IoT devices, such as ambient temperature and oxygen levels, might fluctuate suddenly. The majority of existing ap-proaches to engineer IoT systems rely on predefined processes to achieve users’ goals. Consequently, such systems have significant shortcomings in coping with dynamic and uncertain environments. To address these challenges, we used the concept of Emergent Configurations (ECs) to en-gineer goal-driven IoT systems. An EC is an IoT system that consists of a dynamic set of things that cooperate temporarily to achieve a user goal. To realize ECs, we proposed an abstract architectural approach, compris-ing an architecture and processes, as well as six novel approaches that refine the abstract approach. The developed approaches support users to achieve their goals seamlessly in arbitrary environments by enabling the dynamic formation, deployment, enactment, and self-adaptation of IoT systems. The approaches exploit different techniques and focus on different aspects of ECs. Moreover, to better support users in dynamic and uncertain environments, we investigated the automated
configura-tion of those environments based on user preferences.
Keywords: Internet of Things, Emergent Configurations, Goal-driven
IoT Systems, Automated Configuration of IoT environments, Software Architectures, Self-adaptive Systems.
PUBLICATIONS
Included Papers
Paper I. Alkhabbas, F., Spalazzese, R., Davidsson, P.:
Character-izing Internet of Things Systems through Taxonomies: A Systematic Mapping Study. Internet of Things, 7, 100084. Elsevier, 2019. https://doi.org/10.1016/ j.iot.2019.100084
Paper II. Alkhabbas, F., Ayyad, M., Mihailescu, R. C., Davidsson,
P.: A Commitment-based Approach to Realize Emergent Configurations in the Internet of Things. In IEEE In-ternational Conference on Software Architecture Work-shops (ICSAW), pp. 88-91. IEEE, 2017. https://doi. org/10.1109/ICSAW.2017.55
Paper III. Alkhabbas, F., De Sanctis, M., Spalazzese, R.,
Buc-chiarone, A., Davidsson, P., Marconi, A.: Enact-ing Emergent Configurations in the IoT through Do-main Objects. In 16th International Conference on
Service Oriented Computing (ICSOC), pp. 279-294. Springer, Cham, 2018. https://doi.org/10.1007/ 978-3-030-03596-9_19
Paper IV. Alkhabbas, F., Spalazzese, R., Davidsson, P.: ECo-IoT:
an Architectural Approach for Realizing Emergent Con-figurations in the Internet of Things. In 12th European
Conference on Software Architecture (ECSA), pp. 86-102. Springer, Cham, 2018. https://doi.org/10. 1007/978-3-030-00761-4_6
Paper V. Alkhabbas, F., Spalazzese, R., Cerioli, M., Leotta, M.,
Reggio, G.: On the Deployment of IoT Systems: An Industrial Survey. In 2020 IEEE International Confer-ence on Software Architecture Companion (ICSA-C), pp. 17-24. IEEE, 2020. https://doi.org/10.1109/ ICSA-C50368.2020.00012
Paper VI. Alkhabbas, F., Murturi, I., Spalazzese, R., Davidsson, P.,
Dustdar, S.: A Goal-driven Approach for Deploying Self-adaptive IoT Systems. In 2020 IEEE International Con-ference on Software Architecture (ICSA), pp. 146-156. IEEE, 2020. https://doi.org/10.1109/ICSA47634. 2020.00022
Paper VII. Alkhabbas, F., Spalazzese, R., Davidsson, P.: An
Agent-based Approach to Realize Emergent Configurations in the Internet of Things. Electronics 9.9 (2020): 1347. MDPI, 2020. https://doi.org/10.3390/ electronics9091347
Paper VIII Alkhabbas, F., Alawadi, S., Spalazzese, R., Davidsson, P.:
Activity Recognition and User Preference Learning for Automated Configuration of IoT Environments. In 10th
International Conference on the Internet of Things, pp.1-8. ACM, 2020. https://doi.org/10.1145/3410992. 3411003
Personal Contribution
For all publications above, except Paper III, the first author was the main contributor to the planning and execution of the research and the writ-ing of the publications. Regardwrit-ing Paper III, the first three authors were the main contributors. Assoc. Prof. Romina Spalazzese and Prof. Paul Davidsson contributed to the inception, conceptualization, and the exe-cution of the research. Additionally, they reviewed and edited all publica-tions’ drafts. The other co-authors contributed to the conceptualization, writing, or editing of the publications.
Related Papers Not Included in this Thesis
This thesis also builds upon other papers that I co-authored but are not included in the thesis.
A. Alkhabbas, F., Spalazzese, R., Davidsson, P.: Emergent
Con-figurations in the Internet of Things as System of Systems. In IEEE/ACM Joint 5th International Workshop on Software
Engineering for Systems-of-Systems and 11th Workshop on
Distributed Software Development, Software Ecosystems and Systems-of-Systems (JSOS), pp. 70-71. IEEE Computer Society, 2017.https://doi.org/10.1109/JSOS.2017.6
B. Alkhabbas, F., Spalazzese, R., Davidsson, P.: Architecting
Emer-gent Configurations in the Internet of Things. In IEEE In-ternational Conference on Software Architecture (ICSA), pp. 221–224. IEEE, 2017.https://doi.org/10.1109/ICSA.2017. 37
C. Alawadi, S., Mera, D., Fernández-Delgado, M., Alkhabbas, F., Olsson, C. M., Davidsson, P.: A comparison of machine learn-ing algorithms for forecastlearn-ing indoor temperature in smart build-ings. Energy Systems, 1-17, 2020.https://doi.org/10.1007/ s12667-020-00376-x
ACKNOWLEDGEMENTS
My journey towards a PhD was a long and exciting one, during which many people have supported me. First of all, I would like to express my sincere gratitude and appreciation to Assoc. Prof. Romina Spalazzese, my amazing supervisor, for her invaluable input, availability, patience, kindness, continuous support and feedback and for believing in me. Romina is not only my supervisor but also a colleague and friend. Discus-sions with her always helped me find the right ways to achieve my goals. It has been an honor to be her first PhD student. Similarly, I would like to express special thanks to my co-supervisor, Prof. Paul Davidsson, who also did an amazing job in supervising me and helping me become a bet-ter researcher and a critical thinker. I am deeply grateful for the wealth of knowledge you shared with me and for the inspiration and great support you provided. Thank you Romina and Paul for your tremendous sup-port and for the interesting and fruitful supervision meetings; I could not have imagined having better supervisors for my PhD study. I would also like to thank Prof. Ivica Crnkovic for reviewing the thesis and providing valuable feedback, which helped me enhance the thesis and improve its readability.
I am so thankful to the “Internet of Things and People (IOTAP)” Re-search Profile financed by the Knowledge Foundation and Malmö Uni-versity in collaboration with several industrial partners. I extend my thanks to all the participants in the research project “Emergent Config-urations of Connected Systems (ECOS).”
Many thanks to my PhD examiner, Assoc. Prof. Andreas Jacobsson, and to the review group members, Prof. Bengt Nilsson and Dr. Radu-Casian Mihailescu, for their efforts in reviewing my individual study plans. I would also like to convey my thanks to my managers, Assoc. Prof. Johan Holmgren and Assoc. Prof. Bo Peterson, who facilitated my work at the Computer Science and Media Technology Department and provided all the support I needed. Additional thanks to Assoc. Prof. Jan Persson, Dr. Åse Jevinger, Dr. Christina Bjerkèn, Dr. Sadi.Alawadi, Dr. Annabella Loconsole, Prof. Thomas Pederson, Farid Naisan, Zahra Ghaffari, Dr. Arezoo Sarkheyli-Hägele, Prof. Nancy Russo, Assoc. Prof. Jose Font, Prof. Helena Holmström Olsson, Assoc. Prof. Carl Magnus
Olsson, Prof. Martin Berg, Dr. Victor Kebande, Dr. Fabian Lorig, Johan Holmberg, Susanne Lundborg, Solveig-Karin Erdal, and Sara Säthersten for the different types of support you provided. Moreover, I would like to thank all my colleagues who sat in the PhD students’ room for the interesting discussions and friendly environment.
Finally, this thesis is dedicated to my parents, wife, and children. I am grateful for their understanding, sacrifices, and support. I am also thankful to my friends Dr. Majed Ayyad, Dr. Abed Alhakim Freihat, Bayan Alkhabbas, Mohammed Alkhabbas, Mohammed Isleem, Abdual-lah Hamdan, and Hamza Hamayel for their encouragement.
TABLE OF CONTENTS
I.
COMPREHENSIVE SUMMARY
1
1. Introduction. . . .
3
1.1. Scenarios. . . .
5
1.2. Research Questions. . . 10
1.3. Related Work. . . 13
1.4. Thesis Outline. . . 22
2. Research Methodology. . . 23
2.1. Systematic Mapping Study
. . . 23
2.2. Design Science Research
. . . 23
2.3. Surveys
. . . 25
3. Contributions
. . . 27
3.1. RQ1. What are the characteristics of IoT systems?
. . . 27
3.2. RQ2. What is a suitable software architecture to enable the dynamic formation, deployment, enactment, and adapta-tion of goal-driven IoT systems?
. . . 28
3.3. RQ3. How can goal-driven IoT systems be dynamically formed, deployed, enacted, and adapted?
. . . 30
3.4. RQ4. How can environments be configured automatically according to their users’ preferences?
. . . 33
3.5. Validation of the Architectural Approaches
. . . 34
3.6. Discussion
. . . 35
3.7. Mapping Between RQs, Contributions, and Papers: a Sum-mary
. . . 38
4. Conclusions and Future Work
. . . 39
4.1. Conclusions
. . . 39
4.2. Future Work
. . . 40
II. PAPERS
57
PAPER I: Characterizing Internet of Things Systems through Taxonomies:
A Systematic Mapping Study
. . . 59
1. Introduction
. . . 60
2. Research Method
. . . 61
3. Results
. . . 66
4. Discussion
. . . 80
5. Related Work
. . . 81
6. Conclusions and Future Work
. . . 81
PAPER II: A Commitment-based approach to realize Emergent Con-figurations in the Internet of Things
. . . 93
1. Introduction
. . . 94
2. The Smart Meeting Room Scenario
. . . 95
3. Conceptual Model for Commitment-based Emergent Con-figurations
. . . 95
4. Realizing Emergent Configurations via Commitments
. . . 97
5. Conclusion and Future Work
. . . 101
PAPER III: Enacting Emergent Configurations in the IoT through Do-main Objects
. . . 105
1. Introduction
. . . 106
2. Background on the Domain Object Model
. . . 107
3. The IoT-FED Approach
. . . 109
4. The AL-office Scenario and AL Prototype Running on IoT-FED
113
5. Validation. . . 116
6. Lessons Learned
. . . 119
7. Related Work
. . . 119
8. Conclusion and Future Work
. . . 121
PAPER IV: ECo-IoT: an Architectural Approach for Realizing Emer-gent Configurations in the Internet of Things
. . . 127
1. Introduction
. . . 128
2. Related Work
. . . 129
3. Emergent Configurations Background
. . . 131
4. The ECo-IoT Approach
. . . 132
5. Prototype Implementation
. . . 137
6. Experimenting ECo-IoT
. . . 140
7. Conclusion and Future Work
. . . 144
PAPER V: On the Deployment of IoT Systems: An Industrial Survey
. 149
1. Introduction. . . 150
2. Related Work
. . . 151
4. Overview of Survey Participants
. . . 156
5. Main Findings and Results
. . . 158
6. Discussion
. . . 163
7. Conclusions and Future Work
. . . 165
PAPER VI: A Goal-driven Approach for Deploying Self-adaptive IoT Systems
. . . 171
1. Introduction. . . 172
2. Related Work. . . 173
3. The Approach. . . 175
4. Prototype Implementation. . . 184
5. Validation. . . 185
6. Discussion. . . 192
7. Conclusion and Future Work
. . . 194
PAPER VII: An Agent-based Approach to Realize Emergent Config-urations in the Internet of Things
. . . 201
1. Introduction
. . . 202
2. Emergent Configurations Scenarios
. . . 203
3. The Approach
. . . 206
4. Guidelines for Developers on Using the Approach
. . . . 215
5. Validation
. . . 216
6. Discussion
. . . 221
7. Related Work
. . . 222
8. Conclusions and Future Work
. . . 225
PAPER VIII: Activity Recognition and User Preference Learning for Automated Configuration of IoT Environments
. . . 233
1. Introduction
. . . 234
2. The Smart Hotel Suite Scenario
. . . 235
3. Approach
. . . 236
4. Validation
. . . 245
5. Discussion
. . . 248
6. Related Work
. . . 249
Part I.
COMPREHENSIVE
SUMMARY
1. Introduction
The term “Internet of Things” was coined by Kevin Ashton in 1999 [1], and it builds upon work in several areas, such as ubiquitous comput-ing and distributed systems. The basic idea behind the IoT is to enable physical objects (or “things”, such as sensors, actuators, appliances, and vehicles) to connect and collaborate to achieve goals [2–4]. By exploit-ing such objects, the IoT has opened for new types of services that have a social and societal impact on almost every aspect of our daily life. New things are connected to the Internet every day, and new types of applica-tions are developed and used in several fields such as building automa-tion, health-care, and logistics [3, 5]. Several IoT products are available in the consumer market, including Amazon Echo1and Google Nest
Ther-mostat.2 Amazon Echo provides services such as enabling users to
con-trol connected things like doors, TVs, lights, and thermostats through the Alexa Voice Service.3 Google Nest Thermostat learns user behaviors
to automatically adjust the usage of available power resources to save energy. The number of things connected to the Internet is increasing rapidly due to the advantages gained from connecting objects and the affordability of this technology, among other things.
To exploit the potential of the IoT effectively, several challenges have to be tackled, including the following ones that we study in this thesis. First, the existing visions about the IoT provide a fragmented pic-ture, leading to a lack of common understanding about IoT systems and their constituents [3]. To piece together the fragmented picture of IoT systems, we systematically identified their characteristics by analyzing and synthesizing existing taxonomies. More specifically, we identified seventeen characteristics of IoT systems and grouped them into two cat-egories, namely, elements and quality aspects of IoT systems. Moreover, we conducted a survey to identify the factors that drive the deployment decisions of IoT systems in practice. A second set of challenges concerns the environments of IoT systems, which are often dynamic and uncertain. More specifically, the dynamicity of IoT environments makes it hard to
1https://iot.do/devices/amazon-echo
2https://store.nest.com/product/thermostat/T3007ES 3https://developer.amazon.com/alexa
foresee at design time the things available within an environment. For instance, due to the mobility of users and things, the set of things avail-able in an environment can change dynamically. Additionally, things are often resource-constrained with respect to energy. Thus, they can ap-pear, be discovered, and be used at runtime. Likewise, they can become unavailable suddenly. Furthermore, the hardware infrastructures in dif-ferent environments are heterogeneous with respect to their processing and storage capabilities and interconnections, and the status of IoT sys-tems’ deployment topologies (i.e., the deployment nodes that host the systems’ software functionalities and the communication links among the nodes) might change abruptly. Moreover, users’ activities and goals can change suddenly. An activity represents a high-level user behavior (e.g., sleeping or working), whereas a goal represents a desired effect in the user’s environment (e.g., to make a room dark). Finally, environmen-tal conditions monitored and controlled through IoT devices, such as ambient temperature and oxygen levels, might fluctuate suddenly. To en-able users to benefit from such dynamic and uncertain environments, we argue that several requirements should be considered when engineering IoT systems, including the following ones:
(i) Users should be able to achieve their goals seamlessly when mov-ing among environments that have different types of thmov-ings. For instance, a user uses an application that runs on her/his smart-phone to adjust the light level in her/his bedroom and office and in a hotel room that she/he visits for the first time (see more in Section 1.1.1).
(ii) IoT systems should be able to cope with dynamic changes in their environments. For instance, a user is offered automatically to con-tinue her/his presentation via an available smart screen after the projector used to view the presentation stops working suddenly. Another example is automatically adapting the deployment topol-ogy of an IoT system responsible for adjusting the temperature in a smart building when changes in the infrastructure that hosts the system hinder the achievement of the system’s goal (see more in Section 1.1.2).
(iii) Users should be offered services that are relevant to the specific context and can be provided by available things. For instance, while working on a table using her/his laptop, a user is offered to increase the light level in her/his room for a better working ex-perience (see more in Section 1.1.3). Like goals, services cause desired effects in the environment when users approve their exe-cution. Thus, we use these terms interchangeably in this thesis. (iv) Users’ environments should be configured automatically based on
their preferences. For instance, the light level and color in a user’s room are adjusted automatically whenever she/he issues the
pre-pare to sleep voice command (see more in Section 1.1.3).
Related challenges have been addressed in several research disciplines such as Ubiquitous Computing [6, 7], System of Systems [8, 9], Multi-Agent Systems [10, 11], Service Oriented Computing [12, 13], and Edge-Cloud Computing [14, 15].
The majority of existing approaches for engineering IoT systems rely on predefined processes to achieve users’ goals or automate their en-vironments. Consequently, such systems have significant shortcomings in coping with dynamic and uncertain environments. To address these challenges, we exploited the concept of Emergent Configurations (ECs) to engineer goal-driven IoT systems. A goal-driven system supports a user to achieve a specific goal (e.g., adjusting the light level) within well-defined spatial boundaries (e.g., room, building, or neighborhood).
An EC is a goal-driven IoT system composed of a dynamic set of things that connect and cooperate temporarily. A thing is any (smart) connected object, with its individual functionalities and services or applications [16, 17].
To engineer IoT systems that meet the aforementioned requirements, we developed novel approaches that enable the dynamic formation, deploy-ment, enactdeploy-ment, and self-adaptation of goal-driven IoT systems. The approaches exploit different techniques and focus on different aspects of goal-driven IoT systems. We consider those systems emergent because their constituents are determined dynamically based on the things discov-ered at runtime. To better explain the concept of ECs, in Section 1.1, we introduce three concrete scenarios that we use throughout the thesis. It is important to note that security and privacy are relevant non-functional requirements but are out of the scope of this thesis.
1.1. Scenarios
The concept of ECs represents a basis for novel approaches to engineer-ing goal-driven IoT systems that can cope with dynamic and uncertain environments and automate users’ environments. Realizing the ECs vi-sion requires enabling several processes, including expressing and inter-preting user goals, recommending services to users, learning users’ pref-erences, and automating users’ environments accordingly and automati-cally. The following processes should also be enabled: discovering avail-able things dynamically; automatically forming, deploying, and enact-ing ECs; and adaptenact-ing the ECs in response to changes in their environ-ments.
three concrete scenarios that exemplify the aforementioned requirements, and we use these scenarios throughout the thesis. More specifically, the first scenario, presented in Paper III, exemplifies requirement (i) by il-lustrating how ECs are realized to enable a user to use an application to adjust light levels in different locations that have different types of things. The second scenario, presented in Paper IV and Paper VII, exemplifies requirement (ii) by describing how two ECs formed to support a person to give a presentation and to maintain the temperature in a smart room can cope with dynamic changes in their environments. The third sce-nario, presented in Paper VIII, exemplifies requirements (iii) and (iv) by illustrating how users are offered services relevant to their context and how ECs are realized to configure users’ environments automatically ac-cording to users’ preferences.
1.1.1. The Adjust Light Scenario
Adjust Light (AL)-office. Lorraine enters an office that is equipped with
several connected things, including light sensors, curtains, and lamps. The things with their functionalities are configured to be controllable by people in the office. Preparing for a meeting, Lorraine requests to increase the light level using an application running on her smartphone. The available things are automatically discovered, and as illustrated in Figure 1, an EC formed of her smartphone, a light sensor, curtain, and lamp is enacted to achieve her goal. The light sensor measures the light level in the room, the lamp is turned on, and the curtain is partially opened. We realized this scenario in our IoT lab, including both its hard-ware and softhard-ware.
Figure 1. The Adjust Light Scenario
AL-hotel. Lorraine enters a hotel room that is equipped with three light
sensors, a connected curtain, and two connected lamps. The things with their functionalities are configured to be controllable by guests living in the room. Using the same application running on her smartphone, Lorraine expresses her goal to decrease the light level in the room. The available things are automatically discovered, and given that the avail-able curtain is closed (as illustrated in Figure 1), an EC formed of her smartphone, a light sensor, and the two lamps is enacted to achieve her goal. The light sensor measures the light level in the room, one of the two lamps is turned off, and the light intensity level of the second lamp is reduced.
1.1.2. The Smart Meeting Room Scenario
In a smart building, spaces such as meeting rooms and halls are set up au-tomatically through mobile walls based on the planned activity and the number of attendees. Participants in a conference organized in the build-ing express their interest in attendbuild-ing specific sessions usbuild-ing applications that run on their smart devices (e.g., smartphones). Accordingly, the ex-isting spaces are divided or combined automatically, and users are given directions to the sessions’ locations via their smart devices. When smart spaces are set up, the things available within a space might change. Fur-thermore, attendees might bring (personal) things with them (e.g., smart devices).
When a space is set up, its temperature is evaluated on whether it is within a specified comfort range (e.g., 20°– 22°). If the tempera-ture is not within the range, an EC (EC1from now on) is formed from
available things and enacted automatically. For instance, if the temper-ature in a space is above the range, the EC constituents could be two air-conditioners that are turned on automatically and set up to oper-ate in cooling mode with a temperature degree specified automatically. Compared to an ordinary air-condition system, EC1can forecast indoor
temperature and adjust its constituents automatically without human intervention. The functionalities of EC1are summarized as follows:
(F1) Get the current temperature. This functionality can be performed, for instance, by a temperature sensor.
(F2) Forecast temperature. This functionality can be performed, for instance, by a software program that aggregates data collected from available things such as humidity and temperature sensors, air-conditioning status (i.e., on/off), and air-conditioning temper-ature and uses those data to execute a Machine Learning (ML) model to forecast temperature.
(F3) Analyze data and make decisions. This functionality can be per-formed by a software program that takes as input the current tem-perature, desired temtem-perature, forecasted temtem-perature, and
avail-able actuators. It generates as output a set of tasks that can be performed by those actuators to reach the desired temperature. (F4) Adjust the temperature. This functionality can be performed by
actuators, such as connected heating units, air-conditioners, and fans.
After ECs are formed, their functionalities are deployed automat-ically within available hardware infrastructures (if possible). For in-stance, the functionalities of EC1 (listed above) can be deployed in the
smart building infrastructure, as shown in Figure 2a. Assume that the gateway GW1 gets disconnected suddenly. The event is detected, and
EC1is adapted automatically by redeploying F1 to another gateway, as
shown in Figure 2b.
(a) EC formation (b) EC adaptation
Figure 2.
Adapting an EC in response to changes in its deployment topology
To present his research, Adam expresses his goal to “give a presen-tation” using an application that runs on his smartphone. The goal is interpreted, the available things are automatically discovered, and an EC (EC2from now on) is automatically formed and enacted to achieve
it. For instance, as illustrated in Figure 3a, EC2constituents could be the
smartphone, the laptop, the smart projector, the light sensor, and the cur-tains actuator. The laptop connects and streams the presentation to the projector that illustrates it, while the curtains are closed automatically due to the high light levels detected by the light sensor. During the presen-tation, the projector turns off suddenly. The failure is detected, and EC2
is automatically adapted when Adam agrees to continue the presentation using the available smart screen (see Figure 3b). Since different display media require different light conditions, Adam is also offered the option to open the curtains when the presentation is resumed on the screen.
(a) EC formation (b) EC adaptation Figure 3.
The Smart Meeting Room Scenario
1.1.3. The Smart Hotel Suite Scenario
A smart hotel suite is equipped with various connected things, including curtains, lamps, TV, and different sensors placed across the room (such as temperature, light, door, and PIR motion sensors). Available things are configured to be controllable by people in the room. Alhasan checks in a smart hotel suite and brings with him a smartphone, a laptop, a tablet, and wireless speakers. During the daytime, Alhasan turns on his laptop and starts working on the table. His activity is recognized automatically by analyzing the data collected by the available sensors. For a better working experience, he is offered the following services via the available smart TV: (1) to adjust the light level in the room by increasing the inten-sity of the lamps and partially opening the curtains and (2) to facilitate his work by using the TV’s screen as an extended display to his laptop and the wireless speakers or the TV’s speakers as the sound output de-vice. Alhasan accepts both services and expresses using voice interaction that he prefers to adjust the light level using a lamp and the curtains, to set the lamp’s color to orange, and to use the speakers for playing sound. Consequently, ECs are formed and enacted automatically to provide the services. Alhasan also approves a request concerning performing these services automatically whenever he works on the table using his laptop or tablet.
Later at night, while preparing to sleep, Alhasan uses a voice com-mand to reduce the light level in the room. He is offered to close the curtains or turn off the lamps. He chooses to close the curtains, turn off a lamp, and change the color of another lamp to purple and reduce its in-tensity. Alhasan answers a request to specify the activity related to these services (i.e., sleeping). Based on his answer, he is given a suggestion to secure the room by locking its door and windows and to maintain the temperature during the night at 22◦by turning on the air-conditioner. He
accepts the services and requests that they are performed automatically whenever he issues the “prepare to sleep” voice command. Consequently, ECs are formed and enacted automatically to perform the services.
1.2. Research Questions
In this thesis, we address the four main research questions presented below. The first research question concerns the nature of IoT systems. The second, third, and fourth research questions concern the challenges of engineering IoT systems that can cope with dynamic and uncertain environments and the automated configuration of those environments according to their users’ preferences.
RQ1. What are the characteristics of IoT systems?
There is a lack of common understanding about IoT systems and their constituents. The objective of RQ1 is to identify a set of characteristics that distinguish IoT systems from other systems. Such a set would cap-ture the characteristics needed to be considered while engineering IoT systems. Several studies present characteristics of IoT systems (see Sec-tion 1.3.1); however, there is no effort that provided a systematic char-acterization of IoT systems.
RQ2. What is a suitable software architecture to enable the dynamic
formation, deployment, enactment, and adaptation of goal-driven IoT systems?
The objective of RQ2 is to design a suitable software architecture that supports the automated formation, deployment, enactment, and self-adaptation of goal-driven IoT systems in dynamic and uncertain envi-ronments. In this thesis, we do not focus on the hardware aspects of IoT systems. Nevertheless, we take into consideration aspects such as things’ power source types (e.g., batteries), connectivity status (i.e., con-nected/disconnected), and operational status (i.e., on/off) and the hard-ware capabilities of deployment infrastructures’ nodes.
Engineering software architectures requires making decisions about the system components, their responsibilities, their relationships, and the constraints on them [18, 19]. Several challenges have to be addressed to design a suitable architecture, including specifying the relevant context dimensions and the components responsible for representing, maintain-ing, and reasoning about those dimensions. For instance, context di-mensions that should be considered include available things and their status (e.g., connectivity status and battery levels), available hardware infrastructures (e.g., the processing and storage capabilities of available resources/nodes), and environmental conditions (e.g., the light level in a room).
Moreover, architectural decisions should specify proper relations and constraints among the components responsible for forming, deploy-ing, enactdeploy-ing, and self-adapting goal-driven IoT systems. Such decisions
include determining suitable communication protocols among those com-ponents as well as with the systems’ constituents. Several studies present architectures for IoT systems (see Section 1.3.2); however, none of them fully addresses the aforementioned challenges.
RQ3. How can goal-driven IoT systems be dynamically formed,
de-ployed, enacted, and adapted?
The objective of RQ3 is to devise processes that leverage the architec-ture proposed in answer to RQ2 to enable the automated formation, deployment, enactment, and adaptation of goal-driven IoT systems in dynamic and uncertain contexts. Devising such processes requires ad-dressing several challenges, including representing goals in a machine-understandable way that enables the dynamic formation, deployment, enactment, and adaptation of goal-driven IoT systems. Challenges also include proposing mechanisms to analyze how available things can col-laborate to achieve user goals. For instance, how is it determined that the user’s smartphone should connect and stream the presentation to the projector that then illustrates it? Additionally, users might compete on the use of the things available in their environments, and sometimes their goals cannot be achieved simultaneously.
Moreover, the deployment of goal-driven IoT systems is a complex process partly due to the following reasons. The number and types of things that constitute a system formed to achieve a goal can differ from an environment to another based on the available things. Moreover, multiple factors might drive the systems’ deployment decisions. Addi-tionally, the hardware infrastructures in different environments are het-erogeneous with respect to their processing and storage capabilities and interconnections.
Furthermore, maintaining systems’ context at runtime and detect-ing events that affect the achievement of user goals requires techniques. For instance, how can we maintain the status of the systems’ constituents and the hardware infrastructures? Moreover, mechanisms are needed to enable IoT systems to self-adapt in response to the detected events. For instance, how is it automatically determined that the user can continue the presentation via the available smart screen? Several approaches are developed in related studies (see Section 1.3.3). However, none of them fully addresses the highlighted challenges.
RQ4. How can environments be configured automatically according to
their users’ preferences?
The objective of RQ4 is to enable the provisioning of relevant services to users based on the context. Moreover, RQ4 aims at enabling the learning
of users’ preferences and the automated configuration of their environ-ments accordingly. In other words, ECs should be realized automatically according to users’ preferences without the need for users to request the achievement of each of the corresponding goals.
Offering services to users requires analyzing the specific context and identifying relevant and achievable services. Automating users’ environ-ments requires learning users’ preferences and handling situations where those preferences are not achievable within the environments. A user has preferences about the types of services that support her/him to perform an activity, the things used to provide the services, and the settings of those things (e.g., a lamp’s brightness level). Those preferences are con-textual. For instance, a user prefers to reduce the light level by closing the curtains and reducing a light lamp’s intensity whenever she/he sleeps during the daytime. In contrast, she/he prefers to listen to music, open the curtains partially, and change the color of the lamp’s light and reduce its intensity during the night sleep. None of the approaches developed to engineer goal-driven IoT systems have addressed the aforementioned challenges (see Section 1.3).
Table 3 shows the correlations among the research questions, sce-narios, and requirements presented in Chapter 1.
RQ Scenario Requirement
RQ2, RQ3 The adjust light scenario (Section 1.1.1)
i (Achieving user goals seamlessly in arbitrary environments).
RQ2, RQ3 The smart meeting room scenario (Section 1.1.2)
ii (Coping with dynamic changes in environments).
RQ4 The smart hotel room scenario (Section 1.1.3)
iii (Offering relevant services to users).
iv (Automated environment’s configuration).
TABLE 3.
1.3. Related Work
In this section, we present a brief background on IoT systems and their constituents. Furthermore, we discuss related studies in the fields of Soft-ware Architectures, Self-Adaptive Systems, Multi-Agent Systems, and Edge-Cloud Computing.
1.3.1. IoT Systems
Four digitization waves have made significant impacts on our life. The first wave took place in the 80s, when people started using computers to develop software products. The second wave happened a decade later, when the Internet-enabled computers communicated, which helped peo-ple share and access information easily. The third wave, mobile Internet, enabled us to exploit Internet services wherever we are. Nowadays, we are witnessing the rise of the fourth digitization wave, referred to as the IoT, where digitization has expanded to include physical objects such as sensors, actuators, vehicles, and appliances. These objects, referred to as “things,” represent basic building blocks of IoT systems [3, 4]. They add a physical dimension that makes IoT systems different from traditional software systems.
There is no consensus about IoT systems and their constituents. For instance, some studies consider smartphones, tablets, and PCs as things [3, 20]; in contrast, other studies do not [21, 22]. Some studies present abstract characterizations of IoT systems [3, 23]. Other studies provide more detailed characterizations but take specific perspectives [24–26]. Multiple conceptual models for IoT systems have been proposed. Bauer et al. [27] present a model for the IoT domain represented using the Uni-fied Modelling Language (UML). Patel et al. [28] introduce a conceptual model for IoT applications. Ciccozzi el al. [29] develop a conceptual model for mission-critical IoT systems by building upon the models pre-sented in [27, 28]. However, none of these models offers a systematic characterization of IoT systems. In this section, we introduce the main aspects of IoT systems briefly, while we refer the reader to Paper I for more details.
Figure 4 illustrates a high-level representation of IoT systems. An IoT system comprises a set of things that are heterogeneous, often re-source constrained with respect to energy and processing capabilities, sometimes mobile, and can be autonomous. Connected things can be classified into the following three types:
1. Sensors or actuators. They provide the sensing or actuating func-tions to monitor or change the state of the environment, respec-tively. They represent the majority of the connected things and have negligible or lightweight processing capabilities [26, 30]. 2. Smart things. Physical objects are turned into smart things by
Figure 4.
A high-level representation of IoT systems
capabilities that run smart software. They can also be equipped with sensors and/or actuators [30, 31].
3. Gateways. They are used to support connected things that do not possess the capabilities needed to connect, process requests, or handle security requirements individually. They represent the links between various involved things in an IoT system [31]. Their processing capabilities range between medium and high. Exam-ples of gateways are Arduino4and Raspberry Pi.5
Things connect, communicate, and collaborate to achieve IoT system goals [2, 4]. Communications should be enabled between users and (some) things and among involved things. For this purpose, several types of networks can be used, such as LAN, WLAN, WPAN [24, 32]. Further, several protocols operating at different layers can be exploited, such as MQTT,6CoAp,7RPL,8and HTTP9[33]. The data generated by
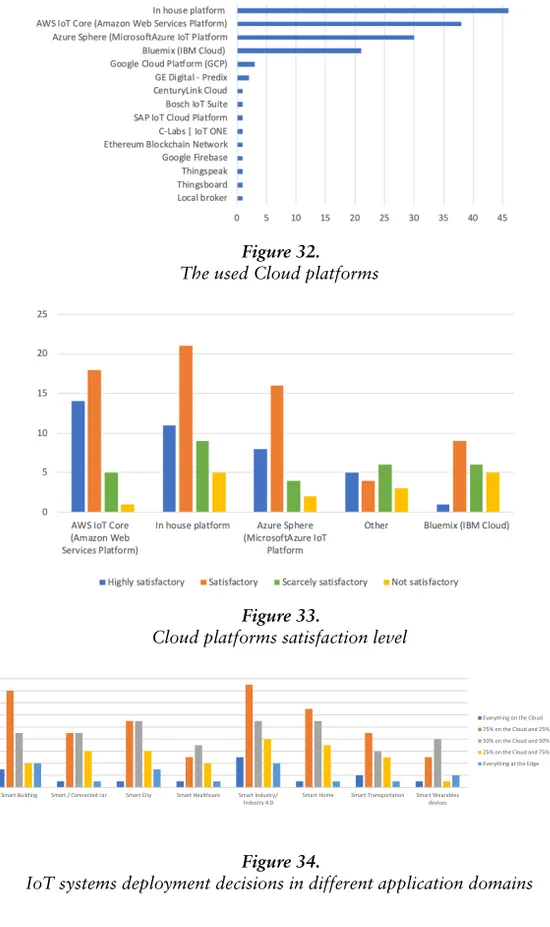
connected things and exchanged among them can be vast, especially in large-scale IoT systems. Such data is heterogeneous and can be of several types, such as textual, numerical, images, and videos [34]. IoT systems should be able to analyze such data and accordingly provide actionable insights in their environments [34, 35]. Several IoT platforms have been developed to facilitate the development of IoT systems, such as AWS IoT
4https://www.arduino.cc/ 5https://www.raspberrypi.org/ 6http://mqtt.org/ 7https://coap.technology/ 8https://tools.ietf.org/html/rfc6550 9https://www.w3.org/Protocols/rfc2616/rfc2616.html
Core,10Azure,11 and Google Cloud IoT.12They provide services such
as enabling things to communicate securely, monitoring their status, and processing the generated data.
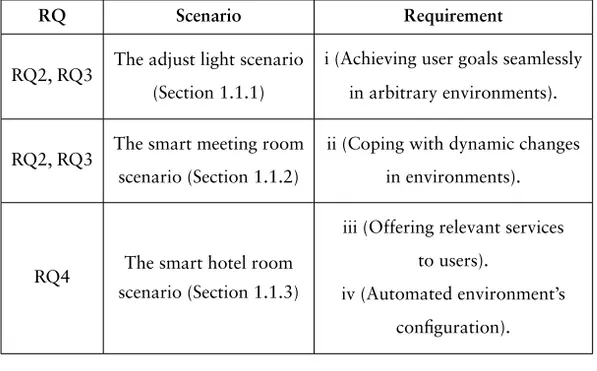
IoT systems can be deployed according to the following models [36, 37]:
1. Everything in the Cloud model. In this model, the software com-ponents of IoT systems are placed in the Cloud. It is suitable when the systems require significant elastic processing and storage capa-bilities or when their constituents are scattered in various areas. 2. Everything in the Edge model. The software components of IoT
systems are placed in networks of more constrained devices with respect to the Cloud (e.g., local servers and gateways), those de-vices are placed at the Edge of the network. In this model, the computational capabilities are lower than those within the Cloud-based model.
3. Hybrid Edge-Cloud model. The software components of IoT sys-tems are distributed across the Cloud and the Edge of the network. Thus, this model enables exploiting the advantages of the two other models. For instance, it supports deploying the components that should perform processes with low latency in the Edge of the network, and deploying those that perform resource-demanding processes in the Cloud.
These deployment models have different properties in terms of response time, availability, privacy, and other quality characteristics [36]. Section 1.3.5 presents related studies that investigate the deployment of IoT sys-tems. Finally, when deployed, IoT systems can be used by human or non-human users (i.e., [semi-] autonomous agents). [31].
To summarize, several studies present characteristics of IoT sys-tems. However, none of those studies offers a systematic charac-terization that provides a holistic overview of IoT systems.
1.3.2. Software Architectures
Software Architectures pervade and manifest themselves in all core as-pects of software systems, including their elements (i.e., components), interactions among those elements, and the constraints on the elements that enable systems to meet their design requirements [18, 19, 38]. Tay-lor et al. [39] refer to a system’s software architecture as the key design
10https://aws.amazon.com/iot-core/
11https://azure.microsoft.com/en-us/features/iot-accelerators/ 12https://cloud.google.com/solutions/iot/
decisions made during the system’s life cycle. The literature presents several methodologies to design software architectures [40, 41]. The dynamicity and uncertainty of IoT environments and human users’ in-volvement put additional requirements on engineering software archi-tectures for IoT systems. More specifically, such archiarchi-tectures should support the recommendation of services relevant to users’ contexts, the learning of users’ preferences, and the automated configurations of their environments accordingly. For these purposes, the architectures should enable the automated formation, deployment, and enactment of goal-driven IoT systems that can self-adapt in response to changes in their environments.
Architectures have been the subject of several works. The IoT-A project presented a service-based reference architecture for the IoT [42]. Santos et al. [43] proposed an architectural style that provides guid-ance for architects to design IoT systems’ architectures. The style is com-patible with the ISO/IEC 30141 Standard and specified using SysADL [44], an architecture description language for software-intensive systems. Khan et al. [45] presented a layered architecture for the IoT. Kramer et al. [46] introduced another architectural model to support the automatic (re-)configuration of Self Managed Systems. The model exploits a repos-itory of predefined plans to achieve goals. New plans are generated in a time-consuming process to realize new goals.
Aura is an architectural framework that supports users to perform their tasks in mobile contexts by pre-compiling user tasks at design time and (re-)assigning appropriate services at runtime [47]. The Socrades In-tegration Architecture (SIA) is a service-oriented architecture that adopts a similar approach to enable the integration of IoT in enterprise services [48]. Business processes are modeled at design time using an extended version of BPEL that allows the dynamic (re-)assignment of services at runtime. Dar et al. [49] presented a high-level architecture to enable the adaptive composition of services in the IoT. The adaptation of com-posed services is performed at design time through user interfaces. Thus, automated adaptations are not supported.
Hachem et al. [50] developed a service-oriented architecture de-signed to address the heterogeneity, interoperability, and scalability in mobile IoT contexts. User goals are achieved by applying an ontological-based composition approach that exploits the notation of probabilistic registration and lookup mechanisms. The architecture addresses spe-cific types of requests related to real-world measurement in the physics and chemistry domains. Kalasapur et al. [51] proposed an architecture for enabling the dynamic service composition in pervasive environments. The mechanism wraps devices’ capabilities into basic services modeled as directed attributed graphs, maintains a repository of services, and com-bines basic services into complex ones to support users’ tasks.
De Sanctis et al. [52] proposed an architectural approach that en-ables the automated formation of most suitable emergent architectures of goal-driven IoT systems by reasoning about multiple quality attributes through a Quality-of-Service (QoS)-based optimization problem. Fur-ther, De Sanctis et al. [53] presented a self-adaptive architecture for microservice-based IoT systems. The architecture exploits Machine Learn-ing (ML) and QoS-aware service composition techniques to enable data-driven adaptations at the levels of things, microservices, and IoT sys-tems. Cámara et al. [54] developed an architectural approach that com-bines ML and probabilistic model-checking techniques to enable opti-mized adaptations of IoT systems with respect to energy consumption and network traffic. ML techniques are used to select the best adapta-tion pattern for a specific situaadapta-tion, and model-checking techniques are used to evaluate the selected pattern’s feasibility and provide feedback to the ML engine to enable the faster convergence towards optimal de-cisions. Oquendo [55] extended the SoS Architectural Description Lan-guage (SosADL) to enable the architectural description of SoS-based IoT systems that can cope with uncertainties related to the partial knowledge of their environments and the status of their constituents. For this pur-pose, the author exploited the notion of digital twins and extended the SosADL with new conceptual abstractions and constructs. Finally, Kozi-olek et al. [56] introduced a reference architecture for enabling “Plug and Produce” in industrial IoT systems to reduce things’ commission-ing times across vendor products. The authors consider settcommission-ings where system constituents are fixed for safety purposes.
To summarize, the majority of the existing architectures comprise repositories responsible for providing predefined execution flows to achieve user goals. Consequently, those systems have short-comings in coping with dynamic context changes. Moreover, none of the existing architectures enables the automated provi-sioning of relevant services to users based on the specific context, the learning of users’ preferences, and the automated configura-tion of users’ environments accordingly.
1.3.3. Self-Adaptive Systems
To enable (IoT) systems to cope with dynamic and uncertain environ-ments, including human users’ involvement, they are engineered as Self-Adaptive Systems [57, 58]. A well-established technique in the field of Self-Adaptive Systems is the implementation of feedback loops [59].
Several approaches have been developed to engineer self-adaptive IoT systems. Hussein et al. [60] introduced a model-driven approach
where an IoT system’s states and adaptation triggers are modeled at de-sign time. When an adaptation is triggered at the runtime, the system’s state is changed based on the designed models. Marrella et al. [61] pre-sented SmartPM, a framework that enables the automated adaptation of processes using situation calculus and AI planning. In this framework, processes are defined by designers using a graphical editor. Events and ex-ceptions that disrupt the processes’ enactment are detected and recovery procedures are generated automatically to adapt faulty processes. Seiger et al. [62] developed a framework that implements the Monitor-Analyze-Plan-Execute plus Knowledge (MAPE-K) feedback loop to enable the automated adaptation of workflow-based Cyber-physical Systems. The framework requires specifying systems’ constituents and their tasks at de-sign time. Suri et al. [63] proposed a semantic-based framework, which comprises an ontology, to develop IoT-aware business processes. To en-able the adaptation of business processes, the framework requires devel-opers to specify the thing(s) that can substitute an IoT system constituent if it becomes unavailable. Specifying systems’ constituents (as in [62]) or predefined adaptations (as in [60, 63]) at design time limits the systems’ flexibility; as foreseeing all available things and all situations in dynamic and uncertain IoT environments can be difficult.
Some approaches adopt the Web of Things (WoT) standards to en-able the dynamic formation of IoT service mashups. Mayer et al. [64] presented an approach to enable the dynamic composition of service-based IoT mashups to achieve users’ goals. Connected things are mod-eled as semantic services, and users’ goals are described in a machine-understandable way. Given the description of a goal and a list of ser-vices, the approach enables the composition of a service-based mashup to achieve the goal. The proposed approach also supports the auto-mated adaptation of mashups apropos the dynamic availability of ser-vices. Sohrabi et al. [65] developed a similar approach that leverages a logic programming language to enable the composition of web services. In general, in approaches that adopt WoT standards, services are anno-tated to model things’ properties. Static properties, such as things’ capa-bilities, can be annotated easily. However, annotating dynamic proper-ties (e.g., battery levels) is more complex, and it has not been adequately investigated in the literature.
To summarize, the majority of existing approaches rely on pre-defined processes to achieve users’ goals, thus limiting IoT sys-tems flexibility. Therefore, there is a need for less-constrained ap-proaches that enable the automated formation, deployment, and enactment of IoT systems to achieve the goals in specific contexts. Such approaches should also support the automated adaptation of IoT systems in response to changes in their dynamic and un-certain environments. Moreover, existing approaches do not con-sider users’ preferences and do not support their environments’ automated configurations. Instead, they enable the achievement of goals only in response to users’ requests.
1.3.4. Multi-Agent Systems
An “agent” is an autonomous computer system situated in a possibly dy-namic and uncertain environment in which it tries to achieve its goals [66, 67]. There has been an increasing interest in exploiting agent tech-nology to engineer IoT systems [68]. One of the most common models for programming intelligent agents is the Belief-Desire-Intention (BDI) model introduced by Rao and Georgeff [69]. BDI-agents make rational decisions about their actions by reasoning about their (i) beliefs about themselves and their environments; (ii) desires, which correspond to goals; and (iii) intentions, which represent the desires that agents com-mit to achieving [69]. BDI-based agents are autonomous, goal-directed, and context-aware, and they can communicate and collaborate to form Multi-Agent Systems (MAS). These characteristics make them very suit-able for realizing ECs [68, 70, 71].
Several approaches have been developed to engineer MAS. How-ever, more efforts are needed to concretely address the problem of en-gineering self-adaptive MAS in a goal-oriented manner [10]. Ciortea et al. [72] presented an approach where things are wrapped as agents or artifacts. When an agent cannot achieve a goal individually, agents col-laborate in a framework called Socio-Technical Network to compose a goal-driven IoT mashup. However, the approach does not support the automated adaptation of the mashup in response to dynamic changes in the environment. Other approaches exploit agents for designing manu-facturing systems [73] or modeling ambient assisted living environments [74, 75].
Preisler et al. [76] developed a framework to enable self-organizing MAS to coordinate separately from applications’ logic. More specifically, the coordination is managed by an external coordination layer where the logic can be distributed over several agents. However, the framework does not link the coordination components with the agents’ decision
making and planning processes [10]. Meanwhile, Viroli et al. [77] pre-sented TuCSoN, a framework for developing self-organizing MAS using a reactive rule-based programming model. TuCSoN enables probabilis-tic and timed coordination among the involved agents. However, it does not provide a mechanism for achieving goals.
Bures et al. [78] presented DECCO, a formal approach and frame-work that enables agents’ coalitions in collective adaptive systems using autonomic component ensembles. For this purpose, the authors pro-posed and exploited the notion of Invariant Refinement Method (IRM), which supports the iterative refinement of system goals to generate sys-tem architectures (i.e., components and ensembles). However, the au-thors state that it is hard to use the framework to develop real-life sys-tems where ensembles are dynamically formed in a distributed manner. To address this issue, the authors proposed TCOEL, a specification and implementation language based on Scala internal DSL [79].
There has been an increasing interest in developing MAS-based IoT systems by exploiting the Interaction-oriented Programming (IoP) parad-igm. This paradigm is concerned with the languages of interactions among agents, the semantics of those interactions, and the tools and tech-niques for realizing MAS [80]. In [81], the authors motivated the use of decentralized MAS to realize IoT systems. Further, the authors discussed several related challenges, including the need for IoP paradigms for MAS-based IoT systems. Christie et al. [82] developed Protocols over Things (PoT), a decentralized approach that exploits the notion of roles and agents to realize IoT systems. The approach compiles protocols into in-teractions’ constraints on communications among roles. To adopt roles, agents perform the decision-making required to enact the specifications of those roles. A rich evaluation of communication protocol languages that can be exploited to engineer MAS is presented in [83]. However, no approaches have exploited IoP paradigms to enable the automated adaptation of MAS-based IoT systems and the configurations of users’ environments.
To summarize, approaches that exploit agent technology to en-gineer goal-driven and self-adaptive IoT systems contribute to a promising unexplored research direction in both MAS and IoT field [10, 68, 70].
1.3.5. Edge-Cloud Computing
As already presented in the subsections above, some approaches have contributed towards enabling the dynamic formation, enactment, and adaptation of goal-driven IoT systems. However, none of those
approach-es addrapproach-essapproach-es deployment issuapproach-es, such as the automated placement of the systems’ functionalities within a hardware infrastructure. The placement problem has been widely studied by considering various factors, such as data size [84], communication and computation time [15, 85], user-application context [86, 87], and cost [86, 88]. The majority of the devel-oped methodologies often rely on mathematical approaches attempting to optimize different trade-offs (e.g., latency and resource utilization). In case of failures, applications are deployed in the Cloud in the major-ity of the approaches. Filiposka et al. [89] introduced a location-aware resource management technique for Edge Computing to support the au-tomated migration of live services when users or devices move.
Very few approaches aim at enabling IoT systems to self-adapt to dy-namic changes in their deployment topologies [90, 91]. Contreras et al. [92] introduced an architecture to support the availability of services in mobile and dynamic Edge environments. When an Edge node becomes unavailable, the service consumers automatically elect another node to run a service replica. Heuristics drives the election process based on the hardware capabilities and battery levels of available nodes. Conse-quently, when two Edge nodes have equal battery levels, a service will be deployed to the node with the highest computational capabilities, even though the other node might be able to run it satisfactorily. Skarlat et al. [93] presented an approach that enables the placement of IoT services on Edge resources optimally by considering QoS constraints such as dead-lines on applications’ execution time. The service placement problem is formulated as an integration linear programming problem where the possible solutions are evaluated in terms of execution cost and QoS ad-herence. Accordingly, the services are placed on Edge nodes. However, in case of any failure, the services are allocated to the Cloud. Sahni et al. [94] developed a task allocation technique based on a genetic algo-rithm that aims at optimizing the energy consumption of tasks deployed at the Edge. However, the technique does not support IoT applications to adapt to the changes in their deployment topologies.
To summarize, existing approaches do not support the dynamic deployment of goal-driven IoT systems and the automated adap-tation of those systems in response to changes in their deployment topologies.
1.4. Thesis Outline
This thesis addresses and contributes to the project Emergent Configura-tions of Connected Systems (ECOS)13 within the Internet of Things and
People (IOTAP)14 Research Profile. The thesis is divided into two parts:
the first part describes a comprehensive summary of it, while the second part presents eight papers that form this thesis’s actual research.
The remainder of Part I is organized as follows. Chapter 2 de-scribes the research methodology applied to address the research ques-tions. Chapter 3 presents the main contributions to the body of knowl-edge. Chapter 4 concludes the thesis and outlines possible future work directions.
13http://iotap.mau.se/projects/ecos/ 14https://iotap.mau.se/
2. Research Methodology
This chapter introduces the research methodology applied to address the research questions presented in Chapter 1. We applied a mixed research method [95–97] that involves the Systematic Mapping Study (SMS), the Design Science Research (DSR), and Surveys presented in Sections 2.1, 2.2, and 2.3, respectively. We considered the peer-reviewed literature as the main source of knowledge.
2.1. Systematic Mapping Study
To address RQ1 (in Paper I), we conducted a SMS—a well-known method-ology in the Software Engineering community [96]. The study identified the characteristics of IoT systems by analyzing and synthesizing existing taxonomies. In general, taxonomies are reference models that facilitate the engineering and development of (software) systems [98]. The study followed the most commonly applied guidelines for conducting system-atic mapping studies [96]. Specifically, the applied method involved three stages: planning, conducting, and reporting.
In the planning stage, we produced a well-defined review protocol. For this purpose, we carried out several activities, including confirming the need of the study, formulating the study goal, defining the RQs, for-mulating the search string, and generating selection criteria. Moreover, we developed mechanisms to analyze and synthesize the identified taxo-nomic dimensions. In the conducting stage, we set the developed proto-col in practice, and we reported the results of the study in the reporting stage. Furthermore, we performed quantitative analysis to provide in-sights about the direction of the future research concerning IoT systems.
2.2. Design Science Research
We applied the design science research to address RQ2, RQ3, and RQ4 (in Papers II, III, IV, VI, VII, and VIII) in an iterative way to devise ap-proaches that realize the ECs vision. We chose this research method because we aimed to create innovative artifacts to solve practical
prob-lems, and this is supported by the methodology. The applied method comprises five stages—namely, problem explication, requirements defi-nition, artifact design and development, artifact demonstration, and ar-tifact evaluation [97].
In the problem explication stage (in all the papers mentioned above), we explored different aspects of the problem by studying the literature, including examples of IoT systems, and evaluating related studies. By leveraging the knowledge gained from answering RQ1 and the contri-butions of Papers I and V, we identified the characteristics of the IoT systems addressed in this thesis (i.e., ECs). In the requirement definition stage, we formulated the requirements that ECs should meet.
In the artifact design and development stage, in [16], we proposed an abstract architectural approach for realizing ECs. Then, we devel-oped six approaches that refine it as follows. In Paper II, we presented an approach that enables connected things to engage into agreements autonomously to form and adapt ECs. In Paper III, we developed the IoT-FED approach to enable the automated formation and enactment of ECs. In Paper IV, we introduced the ECo-IoT approach to enable the automated formation and self-adaptation of ECs. In Paper VI, we presented an approach that supports the automated deployment of ECs and self-adaptation in response to changes in their deployment topolo-gies. In Paper VII, we developed an approach to enable the distributed formation, enactment, and adaptation of ECs, and the conflict resolu-tion among them. Finally, in Paper VIII, we proposed an approach that enables the recommendations of relevant services to users based on the specific context, learns users’ preferences, and configures users’ environ-ments accordingly and automatically.
In the artifact demonstration stage, we developed four prototypes that realized the scenarios presented in Chapter 1.1. These prototypes are described in Papers III, IV, VI, VII, and VIII. In the evaluation stage (in Paper III), we conducted experiments to (i) evaluate the ability of the IoT-FED approach to form different ECs based on available things and (ii) gain insights on the IoT-FED performance. In Paper IV, we conducted experiments to get initial insights on some key components’ performance in the ECo-IoT approach. In Paper VI, we conducted experiments to evaluate the performance and scalability of the presented approach when generating deployment topologies for ECs and adapting those ECs in response to changes in their topologies or constituents. In Paper VII, we conducted experiments to evaluate the ability of the approach to forecast environmental changes in dynamic environments and gain insights into the developed approach’s performance and scalability. Finally, in Paper VIII, we conducted experiments to evaluate the approach’s performance and scalability when recognizing users’ activities and automating their environments in centralized and distributed deployment settings.
2.3. Surveys
Surveys are used to gather information about the actions, characteristics, or opinions of a large group of people—referred to as the population [99]. Surveys are characterized by producing quantitative descriptions through analyzing the data collected by asking structured and predefined questions to a population sample. Further, the data should be collected from a large enough sample to enable the statistical analysis and the findings generalization [100].
We applied this research methodology in Paper V to address RQ1, RQ2, and RQ3. The goal of Paper V is to identify the main drivers of the deployment decisions of IoT systems from the architects point of view. The studies followed the commonly applied guidelines for conduct-ing surveys [101, 102]. Specifically, the applied method involved three phases: survey definition, survey design, and survey implementation and execution.
In the survey definition phase, we formulated the study goal and defined research questions. In the survey design phase, we carried out several activities, including defining the target population, deciding the data collection approach, and specifying the data analysis approaches. We chose to collect the data using an online questionnaire as the targeted population works worldwide. Finally, in the survey implementation and execution phase, we exploited Google Surveys to create the question-naire and make it available online. We then distributed the questionquestion-naire to the targeted population and collected the responses. The survey com-prised 15 questions answered by 66 IoT architects from 18 countries across the world.



![Figure 15 shows a possible refinement of the abstract architecture pre- pre-sented in [1]](https://thumb-eu.123doks.com/thumbv2/5dokorg/3948254.71831/131.892.178.766.479.719/figure-shows-possible-refinement-abstract-architecture-pre-sented.webp)