Safety risks with
ZigBee
smart
devices
MAIN FIELD: Informatics
AUTHOR: Axel von Bergen, Isak Alinger, Jesper Fältros SUPERVISOR:Sigurd Israelsson
JÖNKÖPING 2020 June
Identifying risks and countermeasures in ZigBee
devices with an eavesdropping experiment
This final thesis has been carried out at the School of Engineering at Jönköping University within informatics. The authors are responsible for the presented opinions, conclusions, and results.
Examiner: Anders Adlemo Supervisor: Sigurd Israelsson Scope: 15 hp
Abstract
With ZigBee being the world’s leading IoT protocol, users are vulnerable to attacks on the wireless communication between ZigBee devices and the information that can be gained from them. For users to protect themselves from potential attacks they need to be aware of what information can be extracted and how it can be countered.
Through an eavesdropping experiment, done using three individual sensors from different vendors, various packets with potential for misuse have been identified within the area of building security. With the potential areas of misuse identified, there is also a need for countermeasures against these threats. Countermeasures were identified through a collection of literature that was summarized in order to provide a wide range of alternatives, suitable to different scenarios. The experiment was limited to the functions of the sensors used, as well as traffic using the ZigBee protocol.
This study pinpoints a potential for misuse of the ZigBee traffic sent between devices and shows that the ZigBee protocol is fundamentally flawed from a security aspect. Whilst countermeasures exist, they are not applicable to every situation which is why the ZigBee protocol itself needs further development to be considered secure.
Keywords
ZigBee, IoT, Security, Eavesdropping, ZigBee Countermeasures, Home Automation, Wireless Traffic Exploitation.
Table of contents
1
Introduction ... 1
1.1 BACKGROUND ... 1
1.2 PROBLEM DESCRIPTION... 2
1.3 PURPOSE AND RESEARCH QUESTIONS... 2
1.4 SCOPE AND LIMITATIONS ... 3
1.5 DISPOSITION ... 3
2
Theoretical framework ... 5
2.1 CONNECTING RESEARCH QUESTIONS AND THEORY ... 5
2.2 TECHNICAL TERMS... 5
2.2.1 Beacon request: ... 5
2.2.2 CIA model: ... 5
2.2.3 Cryptography: ... 6
2.2.4 Default global trust center link key: ... 6
2.2.5 IEEE 802.15.4: ... 6 2.2.6 Key exchange: ... 6 2.2.7 Network Security: ... 6 2.2.8 PAN: ... 6 2.2.9 ZED: ... 7 2.3 THEORETICAL ATTACKS ... 7
2.3.1 Network Discovery and device identification attack: ... 7
2.3.2 Replay attacks: ... 7
3
Method ... 8
3.1 METHOD REASONING ... 8
3.2 RESOURCES AND DATA ANALYSIS ... 9
3.2.1 RESOURCES... 9
3.2.2 DATA ANALYSIS ... 11
3.3 EXPERIMENT ... 11
3.4 CREDIBILITY ... 12
4
Carrying out the experiment ... 14
4.1 ENVIRONMENT ... 14
4.2 SET-UP ... 14
4.4 SAMSUNG SMARTTHINGS MULTI SENSOR ... 16
4.5 PHILIPS HUE MOTION SENSOR ... 16
5
Results ... 18
5.1 EMPIRICAL DATA COLLECTED THROUGH SNIFFING ... 18
5.1.1 AQARA DOOR AND WINDOW SENSOR ... 18
5.1.2 SAMSUNG SMARTTHINGS MULTI SENSOR ... 20
5.1.3 PHILIPS HUE MOTION SENSOR ... 21
5.2 ANALYSIS OF DATA ... 22
5.2.1 AQARA DOOR AND WINDOWS SENSOR ... 22
5.2.2 SAMSUNG SMARTTHINGS MULTI SENSOR ... 23
5.2.3 PHILIPS HUE MOTION SENSOR ... 23
5.3 COUNTERMEASURES ... 23
6
Discussion and conclusion ... 26
6.1 DISCUSSION OF RESULTS ... 26
6.2 DISCUSSION OF METHOD ... 27
6.3 CONCLUSIONS AND RECOMMENDATIONS ... 28
6.4 FURTHER RESEARCH ... 29
1
Introduction
This chapter is an introductory chapter to the study and contain background information about what ZigBee is and what it is used for. In this chapter the problem description, purpose and research questions, scope and limitations, and the disposition of the study can be found.
1.1 Background
IoT (Internet of things) is a term which was first coined by Kevin Ashton, who is a pioneer in the IoT field and co-founder of Auto-ID who have built up a global standard for RFID and other sensors. Over time the IoT term have evolved and changed into something that today describes internet connected devices with sensors that can be located, identified, and operated upon (Rouse, 2019; Nh & Wakenshaw, 2017).
The common denominator for IoT devices are first of all the usage of sensors but also the utilization in the devices function to collect data together with the usage of communication hardware and the embedded systems in these devices, all while being connected to a network or the internet. These properties and functions are all part of the IoT devices today (Rouse, 2019). There are also several different protocols and standards in IoT and among these protocols is the ZigBee protocol, which is considered the world’s leading IoT protocol (Hatler, 2019).
ZigBee is based on the IEEE 802.15.4 radio standard, and is used in many things, from measuring temperature in buildings and sending information to house owners when a doorbell is pressed, activating internet connected cameras and remotely controlled light bulbs, triggered by movement sensors (Hatler, 2019).
The ZigBee protocol is designed to have a very low power consumption which can lead to security flaws in the devices because it cannot spare the computational power to use more intensive security features (Zillner, 2015). An increase in power usage leads on the other hand to a lower lifespan of the device because of the increased stress the device is exposed to. These security flaws in the ZigBee protocol introduces the possibility of being prone to e.g. eavesdropping attacks when the end devices connect and authenticate to the ZigBee control station (Morgner, Mattejat, Benenson, Müller & Armknecht, 2017). The ZigBee protocol can be used in critical security devices in buildings as some ZigBee products are equipped with various sensors such as motion sensors, door and windows sensors, temperature, and vibration sensors which all could be used in various scenarios to detect an intruder or other things that could be of interest to the owner. ZigBee sensors could be considered a cheap alternative, or complementing assets, to already existing security measures if configured and set up correctly (ZigBee Alliance, 2020).
The ZigBee stack is based on the IEEE 802.15.4 protocol and consists of four layers, which are the Physical layer (PHY), Medium Access Control Layer (MAC), Network Layer (NWK) and the Application Layer (APL) (Zillner, 2015).
One important aspect of the layers within the ZigBee stack is the consideration of information security. Each of the layers in the stack implements its own challenges and opportunities regarding confidentiality, integrity, and availability. These three areas are primary concepts in information security and make together up the widely used CIA triad. This model is often used when issues regarding information security arise and can then be used as a reference and resource in finding an appropriate course of action to issues found (Perrin, C 2008). In this study, three individual ZigBee end devices were investigated through an experiment designed to emulate a realistic setting, to see what kind of information that could be extracted. Because the ZigBee protocol is used in so many devices, we believe that this study is important. The results from the experiment together with information gathered during the research process of the
study helped in identifyingrecommendations on different countermeasures that can be used or implemented to strengthen the security aspect of ZigBee devices.
1.2 Problem description
The protection of data is important, especially private data or information belonging to organizations, businesses, and people. To protect this data different methods or principles can be applied in order to improve the protection of this data. The EU General Data Protection Regulation (GDPR) has six data protection principles which can assist in this matter. (Lawfulness, fairness and transparency, Purpose limitation, Data minimization, Accuracy, Storage limitation, Integrity, and confidentiality) (ITGP, PTIP, 2017).
The GDPR guidelines and suggestions on protection of personal data is important and relevant for the protection of data and information security in IoT devices as well, as the IoT devices are often connected to networks which have other devices connected to them in order to use the functions of the IoT devices (ITGP, PTIP, 2017).
The security in the ZigBee IoT devices is weak and can be abused by attackers that can attack the IoT devices in order to try gaining access to the network. The network can have other devices connected to it, such as computers or phones containing sensitive or private information. The data sent by the IoT devices could also be used by attackers to gain information about the house or building in which the IoT device operates. To protect the data that the ZigBee devices sends, and reach the goals of the CIA triad, an AES encryption with a key length of 128 bit is used. This encryption is regarded as a strong but the fault in ZigBee’s security lies within the management of the exchange of the transport key (Zillner, 2015).
Earlier work (Van Leeuwen & Taku Ayuk, 2019) was able to intercept and decrypt the transport key exchange when the ZEDs (ZigBee End Device) were using the publicly known default global trust center link key, which is used to encrypt the transport key so that no other than the ZigBee devices should have access to the key. The default global trust center link key is however leaked and could now be considered as effective as no encryption at all. Using that default key made it possible to decrypt the transport key used for the encryption of all traffic between the ZEDs and the trust center.
In the same study (Van Leeuwen & Taku Ayuk, 2019), ZigBee light bulbs were experimented on in an eavesdropping experiment, with focus on decryption of the transport key and traffic. The traffic sent contained information which gave an insight to the building by showing when the light bulbs within the building were turned on or off. As most people turn their lightbulbs off during the night and when they leave home for work this could give attackers the information needed to know when a building is empty and could help in reducing the risk of getting caught while making a burglary.
The protection of the information sent over wireless networks is solved by encryption, but this encryption does not prevent attackers from recovering information about the network and its users. Leakage of information occurring in ZigBee networks have been noticed, recorded, and exposed with help of a cheap platform that enables data collection (Dos Santos, Hennebert, & Lauradoux, 2015).
From a safety point of view, installing ZigBee IoT sensors in a building could give attackers with technical knowledge more information about the use or activity inside of the building if the ZEDs are not secured or have been compromised. To prove this, an eavesdropping experiment was performed to truly find what these ZigBee devices are sending between each other.
1.3 Purpose and research questions
Since ZigBee is regarded as flawed in its security and key management (Morgner et al., 2017); (Zillner, 2015), in which known attacks were used to decrypt the transport key and through that be able to decrypt the traffic sent between the ZigBee devices. Furthermore, the results of earlier referenced work (Van Leeuwen & Taku
Ayuk, 2019) display screenshots of the decrypted traffic which showed the smart bulbs turning on and off with the command “ZCL OnOFF: On Seq: 15” in chapter 5 of their study. This led us to believe that other types of ZigBee devices also send their traffic in an easily read manner. In this study an attempt to decrypt the traffic sent by ZigBee motion sensors, door/window sensors, and multi-sensors was made to reflect how descriptive the data is to an outside attacker. If feasible, this would violate the confidentiality component of the CIA-triad as access to sensitive information would be possible (Perrin, C 2008).
The aim of the work presented in this study is to evaluate several different types of IoT sensors which make use the ZigBee communications protocol on how traffic could be interpreted and misused through experimentation and analyzing patterns in the decrypted traffic sent between the ZigBee devices.
Research questions:
• How can the traffic sent between ZigBee devices be misused?
• What countermeasures could be taken to limit or eliminate the misuse?
1.4 Scope and limitations
This study tested three ZigBee sensor device products (multi, door and motion sensor) in order to evaluate and see to what extent the traffic picked up through eavesdropping from the devices can be used for, which is to gain inside information about the insides or outsides of a building, if it is easy information to understand, what the common security issues are and how much of a safety risk it is to use these ZigBee devices. The reasoning behind the usage of these sensor devices is that the sensors fall under the category of building security, which means that these devices could be vital to the security and safety of the building and what is inside of it (ZigBee Alliance, 2020). The number of devices, in this case three, was based on the belief that it would be sufficient in order to generate the data necessary whilst covering several different building security aspects such as motion detection and door sensors.
Penetration attacks against ZigBee devices were not done in this study as the study is only focused on the traffic itself once an attack has been made. The traffic collected in this study was only collected from a temporary and separated network that had the sole purpose and function to communicate traffic to and from the ZEDs included in the study. The objective with the collection of data was to discover how the data was being sent and to analyze the content of the packets, in order to determine if any of the data can be exploited. Traffic that could not be of use in the study was filtered out.
Since ZigBee is based on IEEE 802.15.4 low rate wireless personal area networks the sniffer
used in the experiment captured them as
well. These packets are considered outside the scope of the study and are not analyzed. However, there is one screenshot in figure 5 in section 5.1 as an example of IEEE 802.15.4 traffic in that section.
As a result of every “thing” in IoT being connected, security threats in different areas emerge and make the security aspect in IoT very broad. It could refer to just about anything related to the CIA triad. Because of this, the “security” and “security threats” investigated in this study are mainly focused on how the traffic eavesdropped from ZEDs could be misused in an illegal or abusive manner (ITU-T Y.2060., 2012).
1.5 Disposition
With the purpose of maintaining a common thread throughout the study, it begins with connecting the research questions to relevant theory in chapter 2. After that, a summary of the method used and why it was used is described in chapter 3. Related methods that could be used in similar scenarios are also described as arguments to why they are not entirely applicable to this specific experiment. Chapter 3 also contains information regarding all the physical
resources as well as the software that was used in the experiment. Section 3.4 of the method chapter also includes a discussion about the study´s credibility.
After presenting the foundation of the experiment, the study proceeds with a larger chapter describing the process of the experiment with a step-by-step approach in chapter 4, which then leads to the presentation of the gathered empirical data and a separate analysis of the data in chapter 5. Discussion of the results gathered in chapter 5 and the conclusions drawn from the experiment are presented, as well as suggestions for further research in chapter 6.
2
Theoretical framework
Chapter two contain information about the research questions and theory behind the research area and how these two were connected to fit the study. This chapter also includes information regarding technical terms and theoretical attacks.
2.1 Connecting research questions and theory
Firstly, basic information on ZigBee is needed; ZigBee security and the safety impact of using ZigBee in a building. ZigBee is the world's leading IoT (Internet of Things) protocol and is used in many different devices and machines (Hatler, M, 2019). ZigBee end devices are often powered by batteries and are designed to have a very low power consumption which the protocol itself is also designed around, in order to extend lifetime. (Zillner, 2015) reports that the low power consumption can lead to security flaws in the devices because the devices cannot spare enough computational power to use more intensive security features. An increase in power usage leads to a lower lifespan of the device, which in turn would damage e main selling points of the device being the efficiency of the battery and the battery life.
In order to collect important data about traffic sent to and from the ZEDs used in the experiment, sniffing was used. Verma (2015) defines sniffing as a way of “smelling” communication made on the network by using our nose. The “nose” in this case, is the tools used to sniff, capture, and collect network traffic and bandwidth information from the network. Sniffing is the technique of using a packet sniffer to “sniff” data flowing through the air or wires. The purpose of sniffing is to understand what kind of data is flowing through the networks. Malicious data can cause harm and have irreparable effect on the network and its devices. The difference between sniffing and eavesdropping is that the latter can be both physical and logical whilst the first can only be performed as a logical attack (Cambridge Dictionary, n.d; Verma, 2015). In this study both sniffing and eavesdropping will be used to describe the action of collecting wireless traffic.
As the hardware limitations in the study did not allow for testing of attacks and countermeasures, a literature review was conducted in order to investigate this further and to see if there was any information that could provide suggestions on the issues discovered through the experiment and aid in answering the second research question. The Western Sydney University defines the purpose of a literature review as a method to gain an understanding of existing research and to help build knowledge in the field of choice (Western Sydney University, 2017).
Internet Engineering Task Force (IETF) defines a countermeasure as “An action, device, procedure, or technique that reduces a threat, a vulnerability, or an attack by eliminating or preventing it, by minimizing the harm it can cause, or by discovering and reporting it so that corrective action can be taken.”(Shirey, 2000).
2.2 Technical terms
This section contains technical terms that are used in the study.
2.2.1
Beacon request:
The beacon request is a mechanism used by devices to scan for networks to join. The beacon request is used by devices in a ZigBee network such as the router to avoid conflicting PAN identifiers (Olawumi 2014).
2.2.2
CIA model:
The CIA triad is a model often used within information security and consist of three primary concepts which are: confidentiality, integrity, and availability.
The first concept of the CIA triad is confidentiality which is about data protection and how to protect data from those not authorized to view it. Confidentiality can be implemented in many things and on different levels in organizations and processes (Perrin, C 2008).
The second concept of the CIA triad is integrity, which refers to the ability of preventing data being changed by someone not authorized. This change of data could be deletion of data, which could be authorized but undesirable. In order to maintain integrity of data, means to prevent change of data is needed and need for the ability to reverse or undo changes that have already been made (Perrin, C 2008).
The last concept of the CIA triad is availability and this concept refers to the ability of being able to access the data when needed. Losing availability basically means loss of access to data, which could be caused by different problems or issues. Network attacks, loss of power to the devices holding the data, application or operating system failures could be examples of these issues or problems (Perrin, C 2008).
2.2.3
Cryptography:
The term cryptography can be used to describe what encrypted and unencrypted traffic means. A common example of cryptography is the conversion of plaintext to ciphertext which is makes the content unreadable through the usage of an encryption algorithm. The process of converting the plaintext to ciphertext is called encryption and the process of converting the ciphertext to plaintext is called decryption (Buchanan, 2017).
2.2.4
Default global trust center link key:
The default global trust center link key of ZigBee has the value of 5A 69 67 42 65 65 41 6C 6C 69 61 6E 63 65 30 39 (ZigBeeAlliance09) and is used by ZigBee devices if the application used by the devices have not specified any other link key during the time of joining a new ZigBee network (Rudresh, 2017).
2.2.5
IEEE 802.15.4:
IEEE 802.15.4 standard developed by the IEEE association is a low-rate wireless personal area network (LR-WPAN) standard and is the foundation on which ZigBee operates. The protocol is mainly used by short WPAN (Wireless Personal Area Network) devices which have low requirements regarding data-rate and power. Defined inside of the protocol is a variety of physical layers (PHYs) which are covering a wide range of frequency bands. This standard was first published in 2003 (IEEE, 2003) and has been updated several times since, the latest update came out in 2020 (IEEE, 2020).
2.2.6
Key exchange:
The key exchange process within ZigBee can work in different ways as there are a few methods that can be applied. The most basic method that can be used in both commercial and residential mode works as follows: The trust center receives a request for a key from a ZigBee end device. The type of key that is requested can be dependent of what mode is being used as within the residential mode the trust center only holds the transport key but in commercial mode it stores three keys. (Rudresh, 2017).
Network Security:
The term network security means protection of the network through a series of activities or processes to ensure usability and integrity of data (Andress, 2014).
2.2.8
PAN:
PAN stands for Personal Area Network. The nodes within a ZigBee PAN can only send data to other nodes in the same PAN. To create a ZigBee PAN, a ZigBee Coordinator (ZC) is used and the only way of creating a ZigBee PAN is through the usage of this ZC. ZigBee Routers (ZR) and ZEDs can join ZigBee networks or normal networks, but cannot create networks themselves (Gislason, 2008).
2.2.9
ZED:
Refers to ZigBee certified End Devices. Examples of this are temperature sensors, light bulbs, and door sensors.
2.3 Theoretical attacks
This section describes attacks that are mentioned throughout the study.
2.3.1
Network Discovery and device identification attack:
Network discovery and device identification attacks can be done with the help of software such as KillerBee. In a network discovery and device identification attack the software mimics the network discovery process and sends out a beacon request in order to gather information. When the information is discovered the software can be used to scan the ZigBee channels and hop between them. When the correct channel is found, the attacker can start intercepting packets (Olawumi et al., 2014).
2.3.2
Replay attacks:
The concept of replay attacks is based on an attacker retransmitting captured packets that has been intercepted through eavesdropping. This can be done with various intents such as stealing money (Kaspersky, 2020).
3
Method
This chapter explains the reasoning behind the method chosen for the study and alternatives to the chosen method are also brought up. The aspect of credibility is also presented in this chapter.
3.1 Method reasoning
Zobel (2014) explains different purposes as to how and
why experiments are used, in this study the method is used as a way of verifying something, which is suitable considering the research questions. Experiments can be further explained as something in which researchers select one or more samples from a target group and subject these devices to various treatments, the effect of this treatment is then compared to the effect of the other subjects with the goal of trying to see differences between them. A more concise explanation for an experiment would be the part of the research in which the variables of the experiment are manipulated and the effects upon them are observed. (Steffe, L. P. & Thompson, P. W., 2000). The ZigBee devices from section 3.2.1 were experimented on in chapter 4 of this study, in order to find useful information to the issues mentioned in the problem description.
A risk with the choice of method was that the information in the data sent from the ZEDs was mostly unknown, but the existence of interesting data was confirmed by earlier work such as the study by Van Leeuwen & Taku Ayuk (2019). There was uncertainty in whether the data sent from the ZEDs was sufficient in order to answer the research questions. The risk of this was rebutted when the experiment was performed and exposed valuable data containing information usable in correlation with the research questions.
Another method that could have been chosen instead of the experiment could have been an interview with the developers or creators of the ZigBee devices or protocol. This method would have been a good alternative to the method that was chosen for this study as it would produce and provide other results than the results found in the experiment.
The eavesdropping type of experiment was chosen as the preferred attack method for the experiment since this type of attack through sniffing, sniffs data packets sent over the network, to and from the chosen ZEDs. With help of a program like Wireshark, individual data packets from a sniffing attack can be captured or collected and further inspected, which allows for more information to be analyzed and gathered. The eavesdropping part in the experiment was done by using the program Wireshark, in which the data captured can be analyzed on, at a data packet level.
Network attack methods other than eavesdropping, like Denial-of-service attacks, that disable or overload the network were not an alternative as the gathering of information after a ZigBee network had been compromised was of interest and would not be possible if the network stopped working.
A man-in-the-middle attack is, according to Glass, Muthukkumarasamy, Portmann (2009), an attack in which a legitimate party communicates via a hostile medium without the legitimate parties' knowledge or consent. The hostile medium has complete control over the communication link and can modify the traffic in any desirable manner. Since the collection of information in the experiment is done passively, a man-in-the-middle attack is not needed.
A penetration attack against the network on which the ZEDs operate could work as a way of getting access to the network if the network were unknown. In this experiment this was not the focus, as stated earlier in the study, others have already proved the ZigBee security to be flawed (Van Leeuwen & Taku Ayuk, 2019). For the research purposes of this study we only wanted to see how the ZigBee traffic itself could be used in order to benefit someone with malicious intent when a ZigBee network have
The second research question regarding countermeasures against misuse of ZigBee traffic serves as a complement to the first question, and the problems we identified through the experiment, is answered through a summary of collected literature from Google Scholar and Jönköping University’s online library. This summary of literature was performed in a systematic fashion in order to extract literature relevant to the research area.
A systematic literature review in which specific studies relevant to the research area of an approved level or quality threshold is used, is important in search of the whole truth (Booth, Papaioannou, Sutton, 2012). In scientific terms, the aim of developing an artifact that can be tested is normally based upon a systematic approach, involving a review of relevant literature and knowledge in the research area (Middleton, Gorard, Taylor, Bannan-Ritland, 2008). In the systematic review of literature in this study, the following process was used to find literature suitable in answering the second research question.
First of all, a decision in the selection of search terms within the research area was done in order to narrow down the search for literature so that it would include relevant information to the research area and could be used in context to study and the second research question. A keyword in the search terms was the name of the protocol of the devices used in the study, which is ZigBee. This keyword was combined with different relevant words to the study, the research area, and the topics of interest regarding the research questions at hand, in order to find contributive results.
Each time a new potential literature source was found it was reviewed to see if it contained valuable information that could benefit the study and the research questions. The review was performed in the way of literature found being read briefly and if the information and content of the literature was relevant it was kept and added to the list of references to be further reviewed.
The following search terms were used for the literature review, on their own, and, or in combination with the keyword ZigBee - security flaws, eavesdropping, countermeasures, network attacks, flaws, issues, network traffic, experiment, extraction, misuse, protocol, weaknesses.
Approximately 100 literature sources were reviewed in this fashion and of these results seven were selected to be further reviewed and used in the study. The results from the literature review helped in answering the second research question, in which alternatives and recommendations on countermeasures were suggested and can be utilized in order to protect the traffic of ZigBee devices from being misused.
3.2 Resources and data analysis
In this section the resources used in the experiment have been highlighted, why they were chosen and the process behind choosing these resources for the study is explained here. This section also includes a description of the type of data that have been collected and processed with examples of how the data could be generated.
3.2.1
Resources
To perform the experiment, three different ZigBee certified ZEDs were chosen. These devices were chosen first and foremost because they were within the research area of building security as mentioned in section 1.4. With this in mind, filters were then applied, based on the price, function, and manufacturer of the devices, in order to find the right devices for the experiment. Each device in the experiment is on the cheaper side of IoT devices because there was a limited budget. All the devices used are shown in figure 1. From left to right: Aqara Door and Window Sensor, Samsung SmartThings Multi Sensor, Philips Hue Motion Sensor, Trust ZigBee Z1 Control Station, and Asus RT-AC66U Router
Figure 1. Picture of devices used in the experiment.
The reason for including different types of sensors with different functions in the experiment was to generate more diverse types of data and to allow more data collection. To see if the form or amount of data generated would vary, different manufacturers were chosen for each device. A basic ZigBee controller was needed to configure the ZEDs and the Trust Z1 control station was selected based on costs. A basic commercial home router was used for the network, brand and model makes no difference as only basic router functionality is required. It was only used to connect the control station to the internet to be able to control it with the Trust SmartHome app. Certain software was also needed to perform the experiment. Wireshark is the most popular packet analyzer with functionality on multiple platforms with support for a lot of protocol families with a simple GUI (Verma, 2015). Unlike other packet sniffing programs like Savvius Omnipeek, Wireshark is free, and we have prior experience working with it.
Wireshark is an open source program used to analyze network protocols and packets (Wireshark, n.d). Wireshark was used to eavesdrop packets to and from the devices through the live capture function in Wireshark. A plugin for Wireshark is necessary to convert the ZigBee packets to be analyzed in Wireshark. The plugin is called Wireshark packet converter and can be acquired for free through Texas Instruments.
Trust SmartHome app is an application which allows the user to connect and control their smart devices from a phone or tablet (Trust Smart Home, 2020). This application was used to configure the Trust Zigbee Z1 control station during the initial stages of the experiment. The SmartRF Flash programmer software from Texas Instruments was used to flash the firmware of the CC2531 USB dongle.
Hardware:
• Samsung SmartThings Multi Sensor GP-U999SJVLAGA • Philips Hue Motion Sensor 929001260761
• Aqara Door and Window Sensor AS006UEW01 • ZigBee controller - Trust ZigBee Control Station Z1 • Network Gateway – ASUS RT-AC66U
• TexasInstrumentCC2531USBdongle-ZigBeesniffer/transmitter (transceiver) • CC debugger for radio frequency (RF) system-on-chip
Software:
• Wireshark
• Trust SmartHome app
• TI Wireshark Packet Converter v1.11.7 or later • SmartRF Flash Programmer
The ZigBee Control Station Z1 is a physical device which allows the user to connect smart devices to the SmartHome application. The control station is a product from Trust and can be used with various ZigBee devices. A key feature of the device is that the user can control and configure the smart devices directly from the application (Trust, 2020).
The following is a description of the devices that were tested and analyzed through the experiment:
Samsung SmartThings Multi Sensor is the device with the most amount of functions in this experiment. The Samsung Multi Sensor can detect the status of a door or window as well as measure the temperature of its location and detect vibrations (Samsung, 2020).
The Philips Hue Motion Sensor is a cube-like device that can be installed in most places of a building. The main function of the device is to detect movement and can be used as a security device or as a device to automate lights within a building based on movement (Philips Hue, 2020).
The Aqara Door and Window Sensor is a small device that with two separate parts. The larger part of the device is the sensor unit and the smaller part contains a cylinder-shaped magnet. These two parts work together to detect the status of a door or window based upon separation between them, which at most can be 22mm for the sensor to be considered closed. Aqara claims that their product is energy efficient as a battery can last over two years, depending on usage (Aqara, n.d.).
3.2.2
Data analysis
This study started with a quantitative phase of data collection where data was sniffed to find packets of interest in the traffic to be able to monitor the movements of people and usage of different sensors depending on what sensor was being tested. After the quantitative phase, a qualitative phase took place where analyzation of the packets of interest was conducted to interpret what was found and to draw conclusions from the collected data (Borrego, Douglas, Amelink, 2009). With the sensors used in this experiment, traffic that indicates when a window or a door is either open or closed is of great interest. Through the Samsung SmartThings Multi Sensor traffic regarding temperature within a building is something that can be analyzed as well. All of the traffic mentioned within this section can be of aid in the process of surveying the activity within a building and will be discussed in the results and conclusions chapter.
3.3 Experiment
The following process is a summary of how the experiment was carried out. It is further explained in chapter 4.
An eavesdropping type experiment was carried out on the selected ZEDs. A basic home network was set up and would act as the foundation of the experiment. A figure of this is seen in figure 2 below.
Figure 2, Network topology used in the experiment
With the network being simple itself does not mean that the experiment is inapplicable to businesses since the authentication modes that were used in the experiment could also be used in both home and business applications if the users wish.
A home network which was configured with internet connectivity was tested. The experiment started with the chosen ZED connecting to the Trust ZigBee Z1 controller. This is where interception of the transmission of the transport key happens in order to be able to decrypt the traffic. Following this there were a series of tests in which the products were used as intended to generate traffic. We moved in front of the motion sensor in different directions in an open space. The multi sensor has a temperature sensor, vibration sensor which was put to a test as well. The device traffic and communication were sniffed by the ZigBee sniffer, saved by Wireshark, and further analyzed for information and patterns later in this study.
3.4 Credibility
There are many ethical aspects that needs to be considered when research of any kind is performed. It is of great importance that a scientific study follows ethical guidelines as science is built on trust (Zobel, 2014).
The foundation of the study´s credibility is based on using cited work within the research area. Usage of existing, relevant information in the description of the method used and process behind the experiment with the purpose of allowing others to easily recreate the experiment for validity purposes. The manufacturers website has been used as the source for the description of the devices with the purpose of removing personal opinions of the devices as authors of the study.
To further increase the credibility of the study, ethical aspects have been kept in mind as in the eavesdropping part of the experiment where the sniffing of traffic occurs. It is important to emphasize on that to avoid ambiguity in what kind of traffic was sniffed in the experiment. Filters in the software was used and applied on the traffic to refine the results gathered to solely show results that are of use to the study and of the ethical kind. Filters could be applied using certain keywords that could be found in specific packets. An example of a filter
that was used, was “zbee_aps”, and the usage of that filter sorted the traffic so that it showed the ZigBee Application Support Layer traffic.
In addition to applying filters to the traffic sniffed, the ethical aspect and the credibility of the experiment was further reinforced by assuring that the experiment was compliant with Swedish law. According to the Swedish law (SFS 1962:700), illicitly listening on telephone calls or conversations without participating is against the law and can result in a fine or up to two years in prison. If this law was to also include sniffing of network traffic, the experiment performed in this study would still not violate this law as it was performed in a controlled environment, where the only network traffic that was getting sniffed was being sent to and from the devices, on a network set up by ourselves. This section exists with the purpose of showing that the experiment is conducted with awareness of the laws in a way that ensures that no criminal activity is performed, further interpretation by a professional within the area of law may be needed to fully explain what this specific law states.
4
Carrying out the experiment
Chapter 4 contain information about the environment and where it was performed, but mainly contain the process of how the experiment was set up and performed which can aid in replication of the experiment.
4.1 Environment
The experiment was performed within a computer laboratory environment at the School of Engineering, Jönköping University. During the time of the experiment, there was without a doubt an increased amount of people staying home because the experiment was performed during the COVID-19 pandemic and therefore decreased the amount of network traffic from different devices in that environment. More people staying home result in less people in the university which means less interfering network traffic. This was one of the reasons why the experiment was performed there.
Because of ethical reasons we performed the experiment in the laboratory which was the correct choice for this, as there is minimal interference and the environment there is optimal. The laboratory is a computer laboratory environment at Jönköping University which has a separate network for experimental and educational purposes.
In order to prevent any illicit sniffing from happening during the experiment, different filters were applied in Wireshark, so that the number of packets collected were limited to only ZigBee traffic and not any other traffic from other devices within the range of the sniffer. This was done in order to prevent any unethical eavesdropping which was also part of the reasoning as to why the experiment was performed in the university.
4.2 Set-up
A simplified step-by-step instruction is presented with the purpose of thoroughly demonstrating how this was done and to help should this experiment be recreated.
The first step of the experiment was to install the software applications listed in the 3.2.1 resources section. One notable step in this process was that Wireshark needed a target command in the Wireshark.exe shortcut to function properly with the Texas Instruments packet converter.
The line “-i\\.\pipe\tiwspc_data -k“ was easily added as shown in figure 3.
Figure 3. Wireshark.exe - shortcut properties.
After completion of the installations, manually updating the firmware of the CC debugger with a cebal hex file was needed. This file could be found in the CC debugger driver archive and was done in order to find the CC debugger in the TI (Texas Instruments) SmartRF Flash Programmer software. The firmware of the CC2531 Dongle was then flashed so it could function with the TI Wireshark packet converter. When finished, the CC
The step after that was to configure the home router so that it could be used within the laboratory environment. The outer interface of the ASUS router was configured with an IP-address dedicated to us by the university which allowed the experiment to be executed in the isolated laboratory network.
When the router had been configured, the Z1 Control station was connected to a power outlet and connected to the ASUS router through a wired connection. When the control station was up and running it could be paired with the “Trust SmartHome App” in which an account was made so that all the devices could be managed from the application.
With the application installed the next step was to open the “Texas Instrument Wireshark Packet Converter” software and select the CC2531 Dongle and configure the correct channel. The correct channel could easily be found by going through all the channels available, looking for traffic from the control station. Since no other ZigBee traffic was being sent by other parties this was very straight forward.
At this point the default trust center link key was inserted into Wireshark and sniffing of traffic begun as seen in figure 4. The purpose of this was to decrypt the transport key. The default trust center link key was found online, without any noteworthy issues.
Figure 4. Wireshark ZigBee Preferences with default trust center link key inserted.
The last thing done before the eavesdropping started was to have the sensor devices paired with the Z1 Control Station, following the Trust SmartHome application instructions and manuals for the ZEDs. When this was done the CC2531 EMK was waiting to intercept the transport key. Figure 5 shows the captured and decrypted transport key packet sent from the Z1 Control Station to the Aqara Door sensor. Which was inserted just like the trust center link key in figure 4.
Figure 5. transport key ready to be taken and used to decrypt every packet sent in this ZigBee
Network.
4.3 Aqara Door and Window Sensor
After completion of the above steps, sniffing of traffic from the Aqara Door and Window Sensor began. As with all the ZEDs, the first observation was the pairing of the device with the Z1 control station. Subsequently traffic was generated by opening and closing the magnetic sensor to simulate the closing and opening of a door. This was tried in a few separate ways to see if different outcomes were possible, for example, opening and closing the sensor slowly, fast, in different orientations but it all yielded the same result and the same kind of traffic, which is discussed later in this study.
4.4 Samsung SmartThings Multi Sensor
The Samsung SmartThing Multi Sensor includes a few different functions all in one package which are: a door sensor, temperature sensor and a vibration sensor. The door sensor was tested in the same way as the Aqara Door and Window sensor. The temperature sensor was tested by being placed by an open window while the temperature outside was colder compared to the room in which this experiment took place, but also in combination with being put inside a pocket to increase the temperature. The Z1 control station did not send a bind request, which is a way of asking a ZED to start sending information from one of the sensors, in this case the Samsung SmartThings vibration sensor, the reason why a bind request was not sent is not known to us. Because of this, the vibration sensor feature could not be tested.
4.5 Philips Hue Motion Sensor
Philips states on their product page that their Hue Motion Sensor only includes a sensor that is able to detect motion and sun light. However, while pairing this device to the Z1 control station, it also seemed to include a temperature sensor. Testing of this device was not as easy as the previous devices because of unexpected compatibility issues. Prior to purchasing the equipment, on the product pages of the Z1 Control Station its stated that it was compatible with the Philips Hue line of products. After heavy testing and still having issues with the Philips Hue Motion Sensor, the Klikaanklikuit/Trust support was contacted for troubleshooting. They responded that their support only extends to the Philips Hue light bulbs and not their sensors. Because of this compatibility issue, the testing of this device was done with little success but still gave interesting points. The Philips Hue Motion Sensor was effortlessly paired with the Trust Z1 Control Stations, but the device never sent any meaningful motion-related traffic back to the control station.
The plan to generate traffic was to move in front of the device and to confirm this movement a notification would be received from the Trust SmartHome detected by the push notifications in combination with analyzing the traffic sent between end device and control station.
5
Results
Chapter 5 includes all the significant results gathered during the study from all of the devices included in the experiment and the countermeasures found through the literature review.
5.1 Empirical data collected through sniffing
In the experiment a total of 80620 packets sent to and from the ZEDs were collected. Many of the packets contained IEEE 802.15.4 data requests and acknowledgements with connectivity information like received signal strength indicator (RSSI), an example of this can be seen in figure 6 below.
Figure 6. Screenshot of IEEE 802.15.4 packet number 37298.
The following sections present different types of packets generated by the ZEDs, though they do not include the IEEE 802.15.4 data requests and acknowledgements that was presented in this section as it is outside the scope of this study. All the remaining packets were sent using the ZigBee protocol and contained data with information that could be misused.
5.1.1
Aqara Door and Window Sensor
In figure 7 and 8 the Aqara Door and Window Sensor sends Report Attributes packets to the control station containing information about whether the door/window sensor is in an opened or closed state. Figure 7 shows the “On/off Control” as “On” which was captured when the sensor did not detect the magnet. Figure 8 shows the opposite when the magnet was near the sensor unit itself.
Figure 8. On/off Control: Off. Door and Window Sensor is closed.
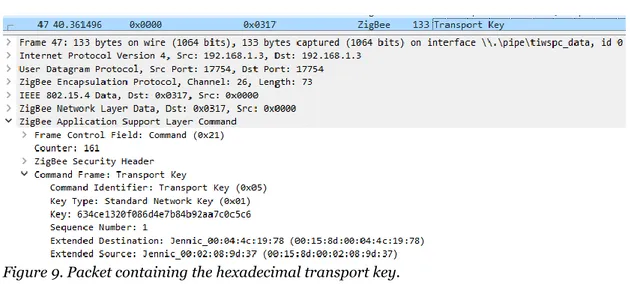
When the Aqara Door and Window Sensor had been connected to the Trust ZigBee Z1 Control Station a transport key was sent from the control station to the sensor. The packet containing the transport key is shown in figure 9.
Figure 9. Packet containing the hexadecimal transport key.
The packet shown in figure 10 is another “Report Attribute” packet that contains an attribute which identifies the sensor as a magnet sensor to the control station.
5.1.2
Samsung SmartThings Multi Sensor
The Samsung SmartThings Multi Sensor includes a contact switch that can be used as a door or window sensor, much like the Aqara device in the section above. This can be seen in figure 11 as the as the attribute “ZoneType” is set to Contact switch.
Figure 11. Read Attributes Response. ZoneType: Contact switch.
As described earlier in this study, this device also has a temperature sensor which can be seen reporting the temperature of the room the experiment was conducted in, seen in the last line of figure 13. Figure 13 is a response to the packet seen in figure 12.
Figure 12. Control station asking the Samsung SmartThings Multi Sensor to report temperature with an interval between 60 and 10800 seconds.
Figure 13. Read Attributes Response from the temperature sensor.
The transport key was sent twice with five seconds between the two packets to this device. This is shown in figure 14
Figure 14. Transport keys sent to Samsung SmartThings Multi Sensor at 2 different sessions.
When the contact switch no longer detects the magnet housed in the second piece, the sensor unit sends a “Zone Status Change Notification” to the control station in order to inform it about the change. When this magnet is detected again the device sends another notification. These two packets can be seen in figure 15 and 16.
Figure 15. Zone status change notification. Alarm 1: Opened
Figure 16. Zone status change notification. Alarm 1: Closed
5.1.3
Philips Hue Motion Sensor
The control station sent the transport key to the Philips Hue Motion Sensor three times with 19 hours between the first and second one as shown in figure 17. This is the transport key output from the first of two captures regarding the Philips Hue Motion Sensor.
Figure 17. Transport keys sent to Philips Hue Motion Sensor.
Figure 18 shows the Philips Hue Motion Sensor binding its occupancy sensing to the control station, meaning the device should transmit data when motion is detected.
Figure 18. Bind Request, Occupancy Sensing
Figure 19 shows an “Unbind request” to the Philips Hue Motion Sensor temperature sensor. No bind request for this cluster was observed.
Figure 19. Unbind Request, Temperature Measurement
5.2 Analysis of data
This section includes the analysis of data found for all the devices included in the experiment.
5.2.1
Aqara Door and Windows Sensor
In figure 7 the Aqara device sent a packet to the control station stating that the sensor was open, indicating that the door or window that the sensor was placed on had been opened. Shortly after that the device sent another packet stating that the sensor was closed, as shown in figure 8. These two packets are the result of testing the functionality of the device by separating the sensor unit and the magnet. The information describing the status of a door or a window could be used to monitor and to map out activity within a building if it is decrypted.
The transport key was sent from the control station to the Aqara device as show in figure 9. As previously mentioned, the transport key was decrypted by inserting the default trust center
decrypting the transport key, the eavesdropper can insert it in the same way as the default trust center link key and obtain all other related ZigBee traffic captured and decrypted as well. Possession of the transport key opens for a lot of potential misuse.
In figure 10 a broadcast packet was sent from the device containing the attributes of the sensor which allowed other devices to identify the model of the Aqara sensor. The most interesting content of this packet in relation to the research question is the identification of the magnet part of the device as it contains information about how the sensor works and is a potential aspect which could be misused.
5.2.2
Samsung SmartThings Multi Sensor
Firstly, the Samsung SmartThings Multi Sensor gave us clearer information on whether the door sensor was in an opened state or not compared to the Aqara sensor as the text line Alarm 1 changed between Opened or alarmed to Closed or not alarmed. As seen in figure 15 and figure 16, the device very clearly indicates that something has been opened and closed.
In figure 12 it is stated that the device reports temperature with an interval between 60 and 10800 seconds, or one minute and three hours. This seemed to be the only factor that was considered when reporting was made. The device was exposed to air by being next to an opened window for one hour (which was enough to cool down the device). After one hour, the temperature was around the 10 C mark and the change in temperature should be sufficient to trigger any reporting if a substantial temperature change was a factor. This proved true when moving the 10 C degree device and heating it up in an approximate body temperature (30-34C) pocket, for another hour which did not trigger any temperature reporting as well.
The vibration sensor that should be part of the Samsung SmartThings Multi Sensor was found to never have sent any bind requests or traffic thus resulting in the belief of this feature not being supported by the Trust Z1 Control Station.To us, a vibration sensor does not seem like it would send anything that could be exploited but since we do not have any data from that sensor, this cannot be confirmed and further studies would need to be performed.
5.2.3
Philips Hue Motion Sensor
Due to unexpected compatibility issues between this device and the control station it was not possible to capture motion-related traffic. Figure 18 shows a bind request for occupancy sensing which indicates that the motion function is detected by the control station and that the Philips device is ready to transmit traffic regarding potential motion detection, but no additional motion-related packet was captured. The occupancy sensing essentially tells the user that it should work, which is problematic when it does not as it might enable the user to depend on the device for what could be an important security feature.
Just like the other devices the Philips Hue Motion Sensor received a transport key from the control station, show in figure 17. The main difference between the transmission of the transport key with this device in comparison to the Aqara device is that the Philips Hue Motion Sensor received the key three times at different times throughout the capture sessions.
In figure 19 an unbind request packet from the control station to the Philips sensor is shown. This unbind request was connected to a temperature measurement function, which is not an advertised functionality with this device, although some reviews on Amazon of the product have mentioned it as a surprise function. It could be regarded as a security issue if the device reports the temperature data without the user even knowing that it is a function.
From a security standpoint, the following countermeasures should be considered when using ZigBee devices as suggested by the following sources.
One way of protecting a network from attacks is to perform a “hardening process” (Markert, Massoth, Fischer-Hellmann, Furnell & Bolan, 2011). The hardening process is an improvement of a technology with reduction of attack vectors. The intention of the process is to improve reliability and availability which in ZigBee’s case could be achieved with the application of methods for encryption (Markert et al., 2011).
Against a ZigBee network key sniffing attacks, one countermeasure that can be used is to pre-install the network key (when using Standard Security level). By pre-pre-installing the network key there is a trade-off between usability and security, at least when applied in a large network as it would require configuration and set-up of each device individually (Vidgren, Haataja, Patino-Andres, Ramirez-Sanchis & Toivanen, 2013; Olawumi et al., 2014). Instead of using the Standard Security level, it would be better to use the “High Security” level in safety-critical Zigbee-enabled system as it makes it so that the network key is never transported over-the-air.
A central component in a ZigBee network is the ZTC (ZigBee Trust Center). All devices in a ZigBee network trust the ZTC which stores and distributes keys to other ZigBee devices and performs trust, network, and configuration management. To achieve maximum security, the best approach would be to only use pre-loaded keys into ZigBee devices directly (Masica, 2007).
Limiting the time an attacker has available to exploit the transport key by implementing key rotation that would change the transport key periodically. This would also improve security as the transport key stays the same by default (Zillner, 2015).
The following principles should be considered and are recommended when deploying a ZigBee network or in the design or architecture of a LR-WPAN solution (Low Rate - Wireless Personal Area Network). In order to control access to mission critical systems and networks which are often targets in attacks, Principle 1’s approach involves implementing several layers of security measures. The reason for having multiple security layers is so that if one layer is breached, others remain for protection of the target environment. Separation and segmentation of the ZigBee network from the wired network in order to have a secure perimeter. (Masica, 2007). This could also be done in the ZigBee network itself by creating multiple networks.
To avoid attacks or configuration failures Principle 2 suggests analyzing every aspect of the environment in order to find areas which can be hardened (Masica, 2007). Hardening of all components in a system is suggested when deploying or expanding, especially if the ZigBee network is being integrated into an existing enterprise (Masica, 2007).
The third and final principle suggests that in order to secure the ZTC component of the ZigBee network, an implementation of a better security architecture should be considered. The security architecture should improve the protection of the ZTC with help of strong policies, procedures, and technical control measures. The ZTC is a core component in the ZigBee security architecture and compromise of this device would undermine the entire trust model (Masica, 2007).
By using targeted regular expression and analyzation of in-depth-datasets collected from three experiments, a reconstruction of a network topology from metadata was possible with the information extracted from a ZigBee network by using Wireshark. In the communication made, exchange in clear and ciphered messages was extracted, in which the identification of the role of the motes, their capabilities and activity were possible. A way of countering these weaknesses which is considered a critical obstacle in the deployment of a ZigBee WSN (Wireless Sensor Network) at a large scale, is to implement simple and pragmatic solutions in order to preserve the privacy into ZigBee WSNs (Dos Santos, Hennebert, & Lauradoux, 2015).
information about it, then all other attacks against ZigBee-enabled networks become easier (Olawumi et al., 2014). To prevent this attack, a possible way would be to implement a type of intrusion detection/prevention system in the ZigBee network which would be triggered once a network is formed, for continuous monitoring of the beacon frame process (Jokar & Leung, 2016).
Countermeasures for the Network Discovery and Device Identification attack is difficult since the beacon request mechanism in ZigBee is used by a ZigBee coordinator or router to identify other networks in order to avoid PAN identifier conflicts. The best way to counter this attack would be to disable the beacon request but this is not possible since the request is essential to ZigBee and therefore cannot be disabled. This means that attackers can use the same technique against ZigBee network discovery (Olawumi et al., 2014).
Replay attacks are efficient against unencrypted ZigBee networks as it is possible to retransmit original frames more than once by an attacker (Olawumi et al., 2014). There are countermeasures against this type of attack, but they are not mandatory in the ZigBee specification and are based on knowledge gained from research work and understanding of the ZigBee protocol stack. These countermeasures include a configuration of the ZigBee stacks so that they confirm the sequence number of the received frame and make sure that the next frame´s sequence number is of at least one greater than the previous successfully processed frame´s. The recommended method to prevent replay attacks would be a type of time-stamping mechanism that should be integrated into the encryption process of ZigBee (Olawumi et al., 2014).
6
Discussion and conclusion
In this chapter the results from the experiment are discussed and the choice of method is discussed here. The chapter ends with conclusions and suggestions for different countermeasures and what should be done for the future regarding ZigBee.
6.1 Discussion of results
The aim of the work presented in this study was to evaluate several different types of IoT sensors which could make use the ZigBee communication protocol, on how traffic could be interpreted and misused through experimentation and by analyzing the content of the decrypted traffic sent between the ZigBee devices.
When performing our experiment, we found that all the communication sent between the ZEDs and control station was easy to read and filter once we had found what kind of packet we were looking for. The traffic was decrypted with the leaked default trust center link key and the captured transport key. This is with the exception for the Philips Hue Motion Sensor, with the already mentioned compatibility issues, in which we combed every kind of ZigBee packet it sent for any data that could be of use in this study.
Regarding the research question about how the traffic can be misused; The Aqara Door and Window Sensor, and the Samsung Multi Sensor could both be used to monitor the activity in a building to gain information about when a building might be empty, leaving it more vulnerable to an attack. As heat in buildings should rise with use, not only from the people occupying it, but also from their activities within. Computers turning on, food being cooked, and TVs all generate heat that would spread and be picked up by the temperature sensor in the Samsung SmartThings Multi Sensor. In case of the complete building being ventilated or cooled, this would be harder to detect. Despite that, the Samsung device would help possible attackers by being able to map the activity inside of a building without the right to do so. By analyzing the patterns of door usage and temperature over time would give insight into a buildings use.
Potentially, devices that only relies on magnets to properly function could also be vulnerable to attacks such as spoofing and disruption of the magnet. By using an external magnet that is stronger than the magnet used in the device, an attacker could force the sensor to bind itself to the external magnet which could be placed on the opposite side of a door for example and this would allow someone to open the door without the sensor detecting it. This was not tested so this is speculative.
The equipment used in the experiment, the CC2531 EMK, CC Debugger, and downloader cable cost about 1000SEK with fast international shipping from Amazon. If more time were available, the purchasing cost of the equipment would have been even lower as better prices could have been found. With the help of this equipment, listening on ZigBee traffic is possible and enables the possibility of exploiting these devices. There are more transceiver options as well, such as the RZRaven USB transceiver, Sewino Sniffer, and the MoteIV Tmote Sky to name a few. A reproduction of the CC2531 can be found on AliExpress for as low as 5 USD, though we do not know the quality or how well that device would perform in practice. The cost of attacking ZigBee is not very high, which is troublesome and can perhaps be one additional incentive to attack ZigBee over other protocols as they may cost more to attack.
With the transport key being the biggest attack vector that could enable people with ill intent to misuse this flaw, it is fitting to discuss the countermeasures for securing this aspect first. In order to secure the transport key from attacks a countermeasure using pre-installed keys can be used. Currently there is no universally embraced solution that does not include a trade-off between security and usability, which is unfair to the consumers. The trade-off is worth it from a security aspect, as it is the main countermeasure to protect the transport key, it is however not possible to use the pre-installed key on a larger scale. However, proposals such