Heuristic Evaluation of
Network Management Systems
Using Axis Communications’ Network
Management System Music in Creation of
Usability Heuristics
Heuristisk Utvärdering av
Nätverkshanteringssystem
Användande av Axis Communications
Nätverkshanteringssystem Music för Skapande
av Användbarhetsheuristiker
Emma Johansson Vikström
Data- and information science Bachelor Thesis
15 HP
Spring term 2018
Abstract
Network management is a challenge for today’s enterprises. Network management systems are usually complex and error prone, making them tedious and difficult to work with for network managers. Related work show that these systems are often not very usable, the reason probably being that more focus is put on functionality rather than usability since security is a very important aspect of network management. However, a system not built according to usability and user experience guidelines will generate errors even though the functionality is correctly built. Related work also show that there is a lack of efficient usability testing methods specifically for network management. In this study, a set of heuristics (usability guidelines), tailor-made for network management, is being created. These heuristics can then be used in usability testing of network management systems. The study is conducted in collaboration with Axis Communications AB. Their network management system “Music” is used as a help in finding and validating appropriate heuristics, and the heuristics are also used for testing the usability of Music. A systematic literature review and user interviews at Axis are used to learn important aspects of network management systems. The heuristic set is then created by setting up a starting set of classical heuristics and modifying it according to previously found network management aspects. These heuristics are then validated by using them in usability tests of Music. The validation proves the new set of heuristics to be more effective in finding issues for a network management system than a classical set of usability heuristics (namely Nielsen’s heuristics). Besides the set of heuristics, the study also results in recommendations of improvements on the usability of Music, mock-ups proposing a new design for Music’s GUI and general recommendations for enterprises with network management systems.
Resumé
Hantering av nätverk är en utmaning för dagens företag. Nätverkshanteringssystem är ofta komplexa och felbenägna, vilket gör dem tröttsamma och svåra att arbeta med för nätverksansvariga. Tidigare forskning visar att dessa system oftast inte är särskilt användbara, med den förmodade anledningen att mer fokus läggs på funktionalitet än användbarhet då säkerhet är en så viktig del av nätverkshantering. Dock kommer ett system som inte byggs efter användbarhets- och user experience-kriterier att generera fel även om funktionaliteten är korrekt byggd. Tidigare forskning visar också att det finns en avsaknad av effektiva användbarhetstester specifikt för nätverkshantering. I den här studien skapas ett set heuristiker (riktlinjer för användbarhet), skräddarsytt för nätverkshantering. Dessa heuristiker kan sedan användas i användbarhetstester för nätverkshanteringssystem. Studien är genomförd i samarbete med Axis Communications AB. Deras nätverkshanteringssystem ”Music” används som en hjälp för att hitta och validera lämpliga heuristiker, och heuristikerna används också för att testa Musics användbarhet. En systematisk litteraturstudie och användarintervjuer på Axis används för att upptäcka viktiga aspekter inom nätverkshantering. Setet med heuristiker skapas sedan genom att sätta upp ett start-set med klassiska heuristiker och modifiera dessa utifrån de tidigare upptäckta viktiga aspekterna. Heuristikerna valideras sedan genom att använda dem i användbarhetstester av Music. Valideringen visar att de nya heuristikerna är mer effektiva vad gäller att hitta problem i ett nätverkshanteringssystem än ett klassiskt set av användbarhets-heuristiker (Nielsens heuristiker). Utöver setet med heuristiker resulterar studien också i rekommendationer på förbättringar av Musics användbarhet, mock-ups med ett nytt designförslag för Musics GUI och generella rekommendationer för företag med nätverkshanteringssystem.
Content
1. Introduction... 1
1.1 Background and previous research ... 1
1.1.1 Usability ... 1
1.1.2 Axis Communications’ network management system Music ... 1
1.1.3 Summary of problem description ... 2
1.2 Research questions ... 2
1.3 Scope ... 3
2. Related work ... 3
2.1 Heterogeneous approach to network management... 3
2.2 Reducing complexity in network management ... 4
2.3 Security of network management systems ... 5
2.4 Usability testing ... 5
2.5 User experience and wow-factor ... 6
2.6 Usability for different cultures ... 7
2.7 Network management for householders ... 7
3. Method ... 8
3.1 Methodology for developing heuristics ... 8
3.1.1 Step 1: Exploratory research ... 8
3.1.2 Step 2: Defining the domain ... 11
3.1.3 Step 3: Finding base heuristics ... 11
3.1.4 Step 4: Specifying new set of heuristics ... 12
3.1.5 Step 5: Validating the heuristics ... 12
3.2 Design mock-ups ... 13
3.3 Alternative methods ... 13
4. Results ... 14
4.1 User interviews ... 14
4.2 Characteristics/important aspects of network management systems ... 15
4.3 Base heuristics ... 16
4.4 New set of heuristics ... 19
4.5 Validating heuristics through heuristic evaluation ... 21
4.5.1 Heuristic evaluation of Music with Nielsen’s heuristics .... 21
4.5.2 Heuristic evaluation of Music with the new set of heuristics ... 22
5. New design proposal for Music ... 25 5.1 Front-page ... 25 5.2 MAC Address-tab ... 27 5.3 Form ... 27 5.4 Permission tab ... 28 6. Analysis... 28 6.1 The heuristics ... 28
6.1.1 Coverage of the field ... 29
6.1.2. Effectivity ... 29
6.2 Threats to validity ... 29
6.2.1 Generalizability ... 29
6.2.2 Enterprise collaboration ... 30
6.3 General recommendations for Axis and other similar enterprises ... 30
6.4 Comparison to previous work ... 32
7. Discussion ... 32
7.1 Scientific contribution ... 33
7.2 Implications from the results ... 33
7.3 Relations with previous work ... 33
8. Conclusion ... 34
8.1 Future work ... 34
1
1. Introduction
Today, a large and increasing amount of people all over the world have internet access (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). Networks are therefore constantly growing, and as is the importance of these networks being managed effectively and correctly. For managing large enterprise networks and keeping them “healthy”, network management systems and network managers to operate them are needed (Sung, Wong and Zeng, 2016). However, today’s network management systems are very complex (Dudkowski, 2009). They are challenging to design and operate, and the reason for this is the ever-growing complexity of different network technologies and network infrastructures. These systems are often large-scale deployments; heterogeneous systems provided by several stakeholders (Dudkowski, 2009). Such challenging design work might not lead to the most usable systems, which then automatically makes it harder to operate and understand. Overall, network management is difficult, costly and error prone (Ballani and Francis, 2006). Because of this, it is important to hide the complexity of the system and provide a simple, usable management interface. This is becoming an all the more relevant topic as network complexity continues to increase (Ballani and Francis, 2006).
1.1 Background and previous research
One common task in network management systems is access control; to decide who/what is allowed in the network and if there should be any constraints to that access (Hinrichs, Gude, Casado, Mitchell, Shenker, 2009). Another typical task is Quality of Service (QoS), meaning that network managers allocates resources to different classes on the grounds of certain policies (rules). Working with translation maps between two pools of IP addresses is another typical task. Overall, there is a large focus on using policies to configure enterprise networks. For example, configuring virtual local area networks (VLANs) is important for enterprises (Hinrichs et al., 2009). A VLAN is a part of a network which is virtually isolated into its own local area network (LAN), while still technically being a part of the original network. The tasks of network management are however often very difficult to conduct (Ballani and Francis, 2006). Network management is also typically rather limited concerning testing usability and user experience (Warren, Nolte, Funk and Merrell, 2004). User dissatisfaction is usually only identified through explicit complaints. Network management tools can collect statistics, but not correctly interpret this information as to how it is affecting the users. Network simulation (creating a simulation of a network in order to perform tests on it) could be a useful method but it takes a large amount of time for a researcher to conduct (Warren, Nolte, Funk and Merrell, 2004). A relevant method for determining usability and user satisfaction is needed for these complex systems.
1.1.1 Usability
The term usability is usually correlated with five different attributes: learnability (new users’ ability to understand the system), efficiency, memorability (ease to remember information needed for use of the system), error tolerance and subjective user satisfaction (Murillo, Sánchez, Sánchez-Lara, 2015). All of these parts are important for a good user experience of any type of product, including network management systems. One common way of testing usability is using heuristics; guidelines which can be used for assessing how well a certain system is following usability standards (Ding and Lin, 2010).
1.1.2 Axis Communications’ network management system Music
This study is conducted in collaboration with Axis Communications AB (hereafter called “Axis”). Axis is a large IT-company focused on security and video
2
surveillance (Axis Communications, 2018). It is a global company with offices in 179 countries, one being its main office in Lund, Sweden. In order to learn about network management systems, and to evaluate the heuristics created in this study, I am using one of Axis’ network management systems called “Music”. As stated in Music’s technical documentation (Axis Communications AB, 2018), the purpose of Music is to handle temporary Axis devices wanting access to the Axis network. The main tasks to be conducted in the system is to administrate MAC addresses for the temporary devices, place devices in different groups and add policies to the groups. Different users have different user privileges and are placed in different subsystems of Music, based on which functions they should have access to (Axis Communications AB, 2018). Music is a complex system which is used in Axis’ offices all over the world. Axis motivation for taking part in this research is that they are going to release Music as an open source project, but first wants to ensure that the system’s complexity is hidden from the user behind a good design and good usability. They want to guarantee the quality of the system and make sure the user experience is positive.
1.1.3 Summary of problem description
As mentioned earlier, network management systems are largely focused on access control (Hinrichs et al., 2009); who/what gets access to the network. This means that security is highly incorporated into network management. Integrity management, confidentiality, availability and authentication are a few of the security concerns within network management (Murillo, Sánchez, Sánchez-Lara, 2015). Since the functionality and security are such important aspects in this type of system, a lot of focus is often on designing for the functionality, making sure everything works and is secure. However, there is often very little focus on making the interface personalized, efficient and cognitively ergonomic (Murillo, Sánchez, Sánchez-Lara, 2015). Usability is often not a priority in this type of system. Many network management tools are perceived to not be very usable, and have several serious usability problems such as difficulty to understand and difficulty to use (Yang and Edwards, 2015). Network management systems are also fairly limited as to which types of tests are suitable (Warren, Nolte, Funk and Merrell, 2004).
This points towards a research gap of appropriate methods for usability testing in network management. It is important to find methods which helps keeping the systems secure at the same time as it helps in giving a good user experience. How could a system stay secure if there is a high risk of users making constant mistakes because of difficulty in using the system? The main purpose of this study is therefore to create tailor-made heuristics for usability testing of network management systems. Heuristics (guidelines) specifically for this domain did, to the best of my knowledge, not exist prior to this study. During the study, Axis’ system Music works as an aid in creating the set of heuristics, and these are at the same time used to assess Music. Apart from the set of heuristics, this research also includes a set of mock-ups suggesting a new design for Music (based on a heuristic evaluation with the heuristics picked out in this study) and recommendations of improvements of Music’s usability (based on the results from the heuristic evaluation). General recommendations for enterprises using network management systems are also presented as an analysis of the results.
1.2 Research questions
This paper is based on the following two research questions:
1. Which usability aspects are particularly important for network management systems?
3
2. Which heuristics should be used for a relevant usability test of a network management system?
1.3 Scope
Besides a general understanding of the domain, focus lies on the GUI (Graphical User Interface) of network management systems. The usability test is created with the GUI in mind. The heuristics are imagined for use on a computer. However, the aspect of responsive design can still be included since one for example might view the system in different screen/window sizes. The focus lies on enterprise use of network management systems, not on home networks. Although the findings of this study might be applicable for all types of network management systems, the heuristics picked out are chosen with enterprises in mind.
2. Related work
The material in this section is a summary of articles related to the areas of this study, gathered through a systematic literature review.
As we in the future continue to extend our use of the internet, network management is playing a key role (Sollins, 2009). Network management is needed for keeping a network healthy and sustainable (Sung, Wong and Zeng, 2016). Network management could be described as keeping track of the state of different network components. It is used for managing the performance and behavior for transporting communications (Sollins, 2009). Network management includes tasks such as configuring devices, connecting devices to a network, setting up infrastructure devices (routers, wireless access points etc.), troubleshooting connectivity problems and managing security of the system (Yang and Edwards, 2010). Network managers can for example use these systems to create different policies for the network (Sollins, 2009). However, network management is challenging and complex. The practice takes a great amount of effort for network managers and is error prone (Sung, Wong and Seng, 2016). Managing a large, heavily utilized network is very challenging. Some examples of key challenges are storage (how to store information and how to make sure the information is always quickly available when needed), how to find and access needed information, how to best formalize the process of policy formation and how to make sure a network management system and its computations are efficient enough (Sung, Wong and Seng, 2016). Many decisions about objectives, requirements and constraints have to be made by network managers, and network management systems are supposed to aid them in this work (Sollins, 2009).
2.1 Heterogeneous approach to network management
The current approach is that each enterprise creates their own tools for network management, all built in different ways (Sollins, 2009). This has created the increasingly integrated, heterogeneous and widely distributed network environment we are facing as state of the art today. One suggested solution for the complexity of network management is one single architecture for network management systems (Sollins 2009). This would decrease complexity as all network management systems would be built in the same way; it would be homogeneous instead of heterogeneous. The suggested architecture would be based on an information plane (containing for example measurement tools and configuration files) and a knowledge plane (with capabilities of analyzing information from the information plane and act upon it). The idea is that the system following this architecture would be partly self-analyzing, self-diagnosing and self-managing as an aid for network managers. This would be an
4
appropriate architecture for providing scalable and adaptable network management (Sollins, 2009). However, this is only one dream-proposal and not state of the art today. Today, decisions on how to build the systems are made within each enterprise, often with complex results for the network managers (Sollins 2009).
2.2 Reducing complexity in network management
Network management, including tasks such as installation, configuration, monitoring, testing and debugging, requires detailed knowledge of many different network components (Ballani and Francis, 2006). One of the big complexity-problems in network management is configuration (Sun and Xie, 2013). Configurations often have an excessive amount of commands and dependencies, and errors are likely. One router configuration file can contain more than 10 000 command lines (Ballani and Francis, 2006). Also, many of the components often have varied management interfaces which are difficult to use and constantly evolving. This complexity is hindering the work of the network manager and will inevitably lead to errors (Ballani and Francis, 2006). Reduction of complexity is not an articulated goal in today’s network design, even though many products are error prone and non-optimal to use (Sun and Xie, 2013). Making the systems less complex is a necessity for reducing errors and improving ease-of-use for the network manager (Ballani and Francis, 2006). A common operational objective to reduce complexity is needed to improve network management (Sun and Xie, 2013). One example of a solution is a methodology suggested by Sun and Xie for reaching minimum configuration complexity (2013). This design methodology includes a model for simplifying the interplay between VLANs and IP-addresses, with the purpose of easing these complex configurations for network managers (Sun and Xie, 2013). Since many of the difficult configuration tasks include human interaction the systems are at risk of human error, which could result in high-profile incidents (Sung, Wong and Zeng, 2016).
The related work is also presenting two examples of possible architectures for reducing complexity. One possible architecture, which is in use by Facebook today, is called Robotron (Sung, Wong and Zeng, 2016). It is a top-down network management approach, with the purpose of minimizing human interaction. With this approach, network managers will not have to do e.g. configurations themselves (Sung, Wong and Zeng, 2016). Instead they express their intent as a high-level command, which is then translated to low-level device configurations by Robotron. Robotron can also be used for monitoring the state of the different components of a system. In other words, Robotron is one current approach for relieving network managers of complexity in their work (Sung, Wong and Zeng, 2016). Another suggested architecture called CONMan also has the goal of excluding/hiding complexity. The way to achieve this according to CONMan is to make the management plane operationally independent; it should be able to “attach” to a system without pre-configuration, and therefore improving configuration complexity (Ballani and Francis, 2006). Also, CONMan advocates for a single, simple management interface for all data protocols. Details about protocol implementation should be an issue solely for the protocol implementer, while management interfaces stay as simple as possible, focused only on necessary tasks (Ballani and Francis, 2006).
Currently, development is also progressing concerning the languages used for configuration of enterprise networks (Hinrichs et al., 2009). Access control, quality of service and admission control are examples of tasks within network management where declaring different policies is necessary (Hinrichs et al., 2009). For declaring policies, it is possible to use certain configuration mechanisms such as VLANs, policy-routing and admission control systems.
5
However, declarative policy languages are being developed, trying to improve the ease of declaring policies and configuring systems. One example is the Flow-based Management Language (FML) (Hinrichs et al., 2009).
2.3 Security of network management systems
Security is an important part of network management systems, which means that today’s systems are often built by security experts (Murillo, 2015). The systems therefore often complies with the technical objective and meets security principles concerning e.g. integrity, confidentiality, availability and authentication. However, the results of employees using the systems are sometimes still not as expected (Murillo, 2015). This is caused by the fact that technical security experts are often not experts within the domains of usability or human computer interaction. The tools might therefore work as expected but not give the users a good user experience (Murillo, 2015). The tools might for example be confusing and therefore error prone even though they are built correctly and are very secure. In order for a tool to have a good user experience, it needs to be easy to learn for new users, efficient and error tolerant (Murillo, 2015). Also, it should be easy for occasional users to remember how to use the system, and it needs to give users subjective satisfaction (Murillo, 2015). This is very important, not least within network management since it is highly involved with security. The system should help the users perform important tasks correctly. Before graphical user interfaces (GUI), network management systems were administered by command line interfaces (CLI) (Murillo, 2015). One suggestion is that today’s graphical interfaces could be complemented by the possibility to use CLI to give users a wider freedom of choice. It could improve user satisfaction since users can choose between performing tasks in the GUI or in the CLI. The CLI might also support tasks which cannot even be found in the GUI (Murillo, 2015). However, this is only a small part of a possible solution. It is important to factor in usability aspects in all parts of the system design (Murillo, 2015).
2.4 Usability testing
Usability, often defined as ease of use, is a key factor of users’ acceptance and satisfaction with a product and an important part of software quality (Choma, Zaina and da Silva, 2016). Usability is made up of five characteristics: learnability, efficiency, memorability, low error rate and satisfaction. There are usability guidelines (called heuristics) with the goal of keeping these 5 characteristics balanced in a software project (Choma, Zaina and da Silva, 2016). Several evaluation methods to test usability have been developed. One type of evaluation method is called expert-based evaluations, or usability inspection methods. With these methods, the researcher and/or other experts performs an analytic review of an interface to find flaws in the design and usability (Choma, Zaina and da Silva, 2016). Another common method for testing usability and user satisfaction is user testing (Murillo, 2015). Users are often included in tests and studies to determine the current degree of usability and find out what users want out of the product/service. For example, users can assess a product leading to a usability score, they can be interviewed, answer questionnaires etc. Users can give valuable input in the development of a product (Murillo, 2015). A company with usability in mind often involves users in the different development phases (Hoonhout, Meerbeek and Buie, 2012). User testing is almost always necessary within usability testing (Choma, Zaina and da Silva, 2016). However, an expert-based evaluation could be appropriate before user testing in order to find existing design flaws and guide the user tests accordingly. When performing expert-based evaluations a user survey can be conducted to find major flaws and particularly important aspects. The
6
evaluation can focus on both more technical/functional details and pure user experience-based details based on the particular domain (Choma, Zaina and da Silva, 2016). From the results of the evaluation, usability indexes can be calculated and analyzed. With this method, you have the possibility to incorporate both technical details, usability characteristics and user experience and get an overview of how usable the product is (Choma, Zaina and da Silva, 2016). It is common to develop heuristics for a specific type of application in order to ensure that the heuristics are effective in that specific domain (Quiñones Otey, 2017). However, in order to be certain of the heuristics effectivity and that they are really appropriate for the area, they need to be developed with a formal methodology. This minimizes the subjective part of choosing usability heuristics since they are chosen on scientific grounds (Quiñones Otey, 2017). One existing formal methodology is roughly based on the following: conducting a literature review within the specific domain, choosing the main concepts within the area and which aspects are important to evaluate, selecting heuristics based on this information, validating and refining (Quiñones Otey, 2017).
Currently, network management systems are rather limited in the ability of determining whether the system is meeting user needs or if users are dissatisfied with certain features (Warren, Nolte, Funk and Merrell, 2004). As mentioned, network management tools can collect certain statistics, but not correctly translate them in order to learn something about the user experience. However, one technique which can be used to assess this is network simulation. In this method, a network analyst extracts network data from the network management system and sets up a simulated network which can then be tested (without having to use the real system with security concerns etc.) (Warren, Nolte, Funk and Merrell, 2004). The problem is that extracting data, setting up and executing a simulation and translating the results into useful information takes a large amount of time for the network analyst. Creating a real-time simulation with all of the necessary functions could also be very challenging (Warren, Nolte, Funk and Merrell, 2004). However, research is currently being conducted on accelerations of this type of test. Tools and architectures for increased ease of doing this kind of test have already been developed (Warren, Nolte, Funk and Merrell, 2004).
2.5 User experience and wow-factor
Products today will not appeal to users by merely being functional (Hoonhout, Meerbeek and Buie, 2012; Väänänen-Vainio-Mattila and Wäljas, 2009). Product innovation is no longer only about using technologies to create a useful product. It is equally as much about creating an appealing user experience (UX) (Hoonhout, Meerbeek and Buie, 2012). Products need to have something “extra”; be fun, cool and extraordinary to really stick to a user’s mind. The importance of the “wow-factor” is growing (Hoonhout, Meerbeek and Buie, 2012). The core question early in the development process should be how to make a product or service appealing and pleasurable. “Traditional” usability is not enough anymore, it needs to be combined with a focus on user experience to keep the users happy (Hoonhout, Meerbeek and Buie, 2012). UX include both functional and psychological aspects of the use of a product/service. A user needs to be able to find and access the desired functions and fulfill the goal he/she has with using the product or service (Väänänen-Vainio-Mattila and Wäljas, 2009). At the same time, the user also needs to like the product psychologically and emotionally. It needs to have a symbolic value for the user and give positive emotions (Väänänen-Vainio-Mattila and Wäljas, 2009). However, there is no clear-cut guide for how to achieve this appealing, pleasurable solution (Hoonhout, Meerbeek and Buie, 2012). Designers need to work based on what has been successful before and what has not.
7
Many UX-models have been developed and are in use today. Despite this, there are domains which are not yet covered with enough characteristics, UX-models and/or usability tests. For example, characteristics affecting the UX of web services have not been studied systematically (Väänänen-Vainio-Mattila and Wäljas, 2009). UX evaluation methods is one area which is also lacking. There are almost no low cost evaluation methods within the field of UX. However, a few appropriate methods exist, expert-based evaluation methods (e.g. heuristic evaluation) being one example of a low cost evaluation method which can be used to cover both the functional and psychological aspects of UX (Väänänen-Vainio-Mattila and Wäljas, 2009). These methods can be used to test interfaces (e.g. web interfaces such as Facebook or TripAdvisor). Usability heuristics can be created, which can then act as a support in product and service development (Hoonhout, Meerbeek and Buie, 2012). They can be created for a specific domain and can therefore always be adapted to a specific application type (Väänänen-Vainio-Mattila and Wäljas, 2009).
2.6 Usability for different cultures
Today, people all over the world have internet access (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). Even though it is a good thing that people have access to information on the internet, it complicates effective delivery of information by web developers. People from different cultures might have different views on what is a good user experience, and this has to be taken into account by web developers (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). Something which is found clean and effective in one culture might be considered boring in another. In order to design for this, there is a cultural dimensions-model which can help differentiating desired characteristics between different cultures. The model consists of 6 cultural dimensions, e.g. the individualism index (IDV) and the power distance index (PDI) (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). Different cultures will have different scores for these indexes, and the scores can then be used for guiding the design. A set of heuristics specifically for intercultural design on the web have been created. An example of a heuristic in this list is “aesthetic and minimalist design” (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). For a culture with a high IDV-score, this heuristic should be followed. The interface should be clear of “visual noise”. However, for a culture with a low IDV-score, this heuristic should not be followed. People of this culture would appreciate animations and color over cleanliness (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013).
2.7 Network management for householders
Today, network management is something which is not only relevant for enterprises, but also for householders (Yang and Edwards, 2010). The tasks of network management are relevant for most “ordinary people” today. Householders need to configure routers, setup wireless connection points etc. However, “ordinary people” might not have the same knowledge as people working with networks on enterprises (Yang and Edwards, 2010). Many users find that network management tools for home use have severe usability issues (Yang and Edwards, 2010). Many find the tools hard to understand and to use, that user interfaces of the tools are inconsistent and that manuals/instructions are unusable. The tools often require a rather high level of technical knowledge. They are in great need of a more easy-to-use design, especially when they are guided towards householders who might not have very sophisticated technical knowledge (Yang and Edwards, 2010).
8
3. Method
The main purpose of this study is to create a tailor-made set of heuristics, specifically for usability testing of network management systems. These heuristics will at the same time be used to assess the usability of Axis Communications network management system Music. This is achieved by using a formal methodology for the creation of heuristics.
3.1 Methodology for developing heuristics
The creation of this set of heuristics is based on a specific formal methodology for developing usability heuristics by Quiñones Otey (2017). Originally, this method consists of 7 steps, but for this study a few changes have been made to the method. The changes made to the method was merging two similar steps together, deleting a few steps and adding a new one. The reason for these changes was mostly to simplify and clarify the method since some of the steps were somewhat short, redundant or similar enough to be merged. Some of the names of the steps have also been changed into one’s more descriptive for the specific tasks conducted in this study. The 5 steps used for this study and how each of the steps were conducted are described below. The methods of step 1-2 helps answering research question number 1, and step 3-5 helps answering research question number 2. A brief summary of the steps is found below.
Step 1: Exploratory research – Literature review and user interviews for
gathering domain knowledge (for research question 1)
Step 2: Defining the domain – Defining characteristics/important aspects for
network management systems (for research question 1).
Step 3: Finding base heuristics – Gathering existing heuristics to use as a
starting point in the creation of the new heuristic set (for research question 2).
Step 4: Specifying new set of heuristics – Creating the new set by modifying the
base heuristics (for research question 2).
Step 5: Validating the heuristics – Validating the heuristics by using them in a
heuristic evaluation, and comparing the results to the results of existing heuristics (for research question 2).
In the following sections, the steps are explained in greater detail.
3.1.1 Step 1: Exploratory research
This step is about getting familiar with the specific domain, which features are important within this domain and what research is previously done within the area (Quiñones Otey, 2017).
3.1.1.1 Literature review
In this step, a systematic literature review has been conducted with the purpose of gaining knowledge about network management, usability and how usability testing can be performed within this particular field. The reason for choosing a literature review over another method was that it is an appropriate method for getting a broad overview of an entire field (Webster and Watson, 2002). It is an essential part of any study for creating a firm knowledge foundation (Webster and Watson, 2002). The literature review was started by finding an appropriate amount of articles by searching in databases using search strings relevant to the subject of the study. The desirable amount of articles was controlled by balancing the need to cover the area and the time available. Enough articles were needed to cover the state of the art without becoming too many for the given scope and resources of the study. 3 searches with different search strings were conducted, which resulted in 241 articles as a starting point. The articles which were going to be used for the final review summary were then selected
9
through certain conditions, shown below (the table also shows the search strings used for finding the initial articles). After applying these criteria, a total of 13 articles remained. These articles were then summarized, creating a “related work”-section covering the area. The summary of the review is presented in section 2.
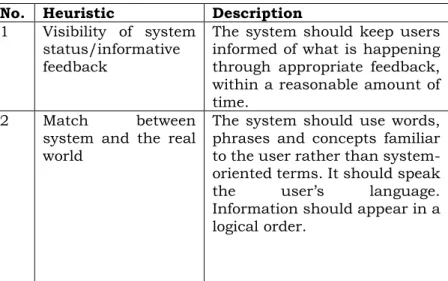
Table 1. Inclusion and exclusion criteria for articles in the literature review.
Inclusion/exclusion criteria
Description Motivation
Relevant databases,
keywords and year of publication
Only publications from the ACM database.
For search 1: Articles should
include the keywords
“network management”,
“user” and “experience”, and be published no earlier than 2008.
For search 2: Articles should
include the keywords
“usability”, “heuristics” (in
abstract) and “user
experience, and be published no earlier than 2005.
For search 3: Articles should
include the keywords
“Network management” (in title), and be published no earlier than 2003.
ACM contains relevant
information within the fields researched, and it is easy to find an appropriate amount of articles for this specific subject.
The keywords are relevant
either for the research
questions, the purpose of the essay and/or descriptions of the concerned areas.
The years of publication are decided from a balance
between not including
outdated information and including enough material.
Publication form Only journal articles or
conference articles.
These article types guarantee trustworthy, scientific text.
Title and abstract
content
Only articles which seem relevant when reading the title and abstract should be included.
Articles with no relevance for the topic are sorted out. Duplication elimination If the same article is found
more than once (e.g. in the different searches) duplicates should be removed.
It is unnecessary to include an article more than once. Full text content If an article still feels relevant
after reading the full text, it should be included among the final articles.
The full text might not include exactly what one expects when reading the abstract. Therefore, the full text should be read before the final choosing of articles.
3.1.1.2 User interviews
As a complement to the literature review, user interviews have been conducted at Axis to get a deeper understanding of how and for what a network management system is used at an enterprise. Finding important tasks, complex parts of network management and how users feel about using such system was part of the purpose with the interviews. Two interviews were conducted: one interview with an employee from the infrastructure team at Axis and one group interview with three employees from Axis’ IT-operations team.
The interview method chosen is semi-structured interview. In a semi-structured interview, the interviewer uses a set of pre-defined questions, but the
10
conversation may also divert from the questions and lead into new areas (Fylan, 2005). This method is appropriate when the questions which need to be answered are known, but it is still possible that more information than what is covered in the questions could be useful for the researcher (Fylan, 2005). If the researcher is not an expert within the area, the interview subject could provide the researcher with information which they previously did not even know they needed (Fylan, 2005). Since network management was an entirely new area for me as a researcher when starting this thesis, but a few important main questions could still be formulated, this was an appropriate method. The reason for performing one of the interviews as a group interview instead of three individual interviews was the interview subjects’ lack of time for scheduling different meetings. It was easier for the interview subjects to schedule one meeting instead of three. Arguably, all of the interviews should have been conducted in the same way for consistency. Meeting the interview subjects individually would also ensure the opportunity for each of the subjects to share their view of the topic. However, since the interviews were semi-structured they would not have been performed in the exact same way even if they were all conducted individually. All of the three interview subjects in the group interview still contributed in answering the questions. In addition, being in a group sometimes sparked longer discussions and more new topics than in the individual interview. The interview subjects were chosen by recommendations. Interviewing the employee of the infrastructure team was a recommendation from my supervisor at Axis. The subsequent three interview subjects were recommendations from the first interview subject, of people in a different position who might provide further useful information.
The interviews were specifically revolving around Axis’ network management system “Music”. This resulted in specific knowledge about Music and network management at Axis, which alongside the findings from the literature review could be used to generalize important aspects of network management systems. The following questions were used for the interviews:
Table 2. Interview questions for semi-structured interviews at Axis. No. Question
1 What role do you have at Axis?
2 Which role/-s do you imagine others who are working with Music might have?
3 How would you rate your knowledge about the use of Music, on a scale from 1-5?
4 Describe a normal workday for you.
5 How would you describe Music and what it can be used for? 6 For which of your work tasks can you use Music? What is the
purpose of Music for you?
7 What is the purpose of Music for Axis?
8 Do you think that people who are going to use Music need certain specific knowledge? If yes, what knowledge?
9 Are there any functions in Music which you would describe as more important than others? Are there any functions which you would describe as more complex than others?
10 Do you feel that it, overall, is easy or difficult to perform the tasks you need to perform in Music?
11 Can you remember that you have recently encountered any problem when using Music?
- Could you describe the problem?
- What would you say is the cause of this problem? - How do you think it should have worked instead?
11
Interview questions should be created based on the goals of the interview and what is important for the researcher to learn (Fylan, 2005). In this case, what network management is, which tasks it could involve and which parts are complex was important to learn. Using Music as the topic of the interview made it easier for interview subjects to answer the questions than if they would have to speak generally about network management. As mentioned, the results can then be generalized together with the findings from the literature review, making the findings appropriate for both Music and other network management systems. Since the interviews were semi-structured the conversation also moved on to general discussions about network management, with Music as a base of the discussion. The reason for choosing interviews over another method was that it was an appropriate way to get a view into a company working with network management and receiving subjective views of user experience from network managers.
An interview can be used to learn about the subject’s thoughts, feelings and actions. (Fylan, 2005). This is incorporated into the interview by formulating the questions in different ways. Sometimes the questions are asking for what the subject thinks about something, sometimes how something feels, and sometimes what the subject does in the system. The ordering of the questions should based on topics (Fylan, 2005). As seen in table 2, e.g. all of the questions about roles are gathered in the beginning, then all of the questions about tasks are following etc. The last of the interview questions (no. 11) is created with the method “critical incident interview” (Flanagan, 1954) in mind. One common purpose of using this method is to learn about human behavior in certain situations. One way to use this interview method is to ask the interview subject to describe a certain incident (within a specified topic or context), which can then be used for discussion (Zakariasen Victoroff and Hogan, 2006). This method was incorporated into question no. 11 by asking the subject to describe a recent incident/problem they have had when using Music. This could then be further discussed by the follow-up questions (see question no. 11 in the table 2).
3.1.2 Step 2: Defining the domain
This step is for characterizing the system type and highlighting important topics of the domain (Quiñones Otey, 2017). After conducting the literature study and Axis user interviews enough knowledge had been gathered within the domain of network management (and network management in relation to usability) to decide on important aspects and characteristics of network management. Things which are important to network management systems, specific tasks which are often complex, important functionality etc. could now be clarified in order to characterize this type of system. This was done through summarizing the results from the literature review and the interviews and finding recurring themes.
3.1.3 Step 3: Finding base heuristics
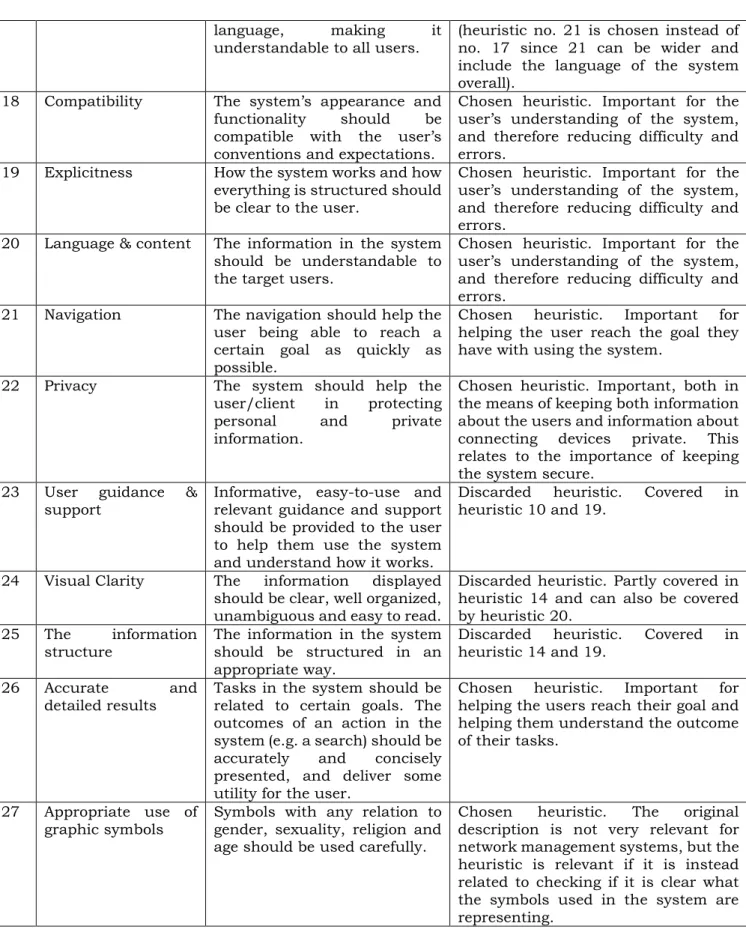
In this step, existing heuristic sets are selected as a base for the new heuristic set (Quiñones Otey, 2017). These base heuristics can then be reviewed to see which of these heuristics match the characteristics and important aspects of the domain. These should then become a part of the new set (Quiñones Otey, 2017). Some sets of heuristics used as base heuristics in this study were found through the systematic literature review, and a few complementary sets were found through extra research specifically for this step. The criteria for choosing a set were that they should be suitable for web systems/web applications or contain a heuristic which might prove to be important in correlation with the characteristics found in step 2.
12
The base heuristics used in this study are gathered from 5 different sources. Some sets partly overlapped, but duplicates have been removed. What might be referred to as “Nielsen’s usability heuristics” (Nielsen, 1995) are very commonly used within the field of usability (Ding and Lin, 2010). They are principles focused on user interface design and interaction design (Nielsen, 1995), and are therefore relevant for this study. Several articles encountered during research for this study where heuristics were used have either only used Nielsen’s heuristics, or used them as a part of their set of heuristics (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013; Abdollah, Sivaji, Tzuaan, Md Nor, Ngip Khean, Woodhull and Arumugam, 2014). The fact that these heuristics are constantly recurring in scientific studies implies that they are relevant today. Therefore, they are included in the base set of this study. Another set is, besides Nielsen’s heuristics, containing heuristics concerning cultural differences (Díaz, Rusu, Pow-Sang, Roncagliolo, 2013). These heuristics are relevant for applications which might be used in several different cultures. The third set of heuristics used is mainly focused on cross-channel UX, but might still provide some relevant heuristics for smooth, simple and enjoyable use of web systems/web applications on a computer (Resmini and Rosati, 2011). The fourth set contains heuristics for web-based systems (some of Nielsen’s heuristics are incorporated while some are specifically focused on web-based systems) (Abdollah et al., 2014). The fifth set contains a few specialized heuristics for critical applications with critical information (Alves, Gresse von Wangenheim, Savaris and von Wangenheim, 2014). They were created for laboratory systems but might be suitable for other critical systems as well.
3.1.4 Step 4: Specifying new set of heuristics
In this step, the new heuristic set is created. Each heuristic in the base set is either chosen for the new set or discarded (Quiñones Otey, 2017). In order to create the new set of heuristics, the base heuristics from step 3 were reviewed. Each heuristic was either chosen to be appropriate for network management systems or discarded (based on the characteristics found in step 2). Each heuristic was also evaluated regarding whether it was appropriate for network management as it was, or if it needed a change of name or description. Then the chosen heuristics with the proposed changes were gathered in a final list. The list of heuristics was then checked against the characteristics specified for network management systems to see if every important aspect was covered. Two new heuristics created by me were then added to the list in order to cover all of the main characteristics found in the interviews and the systematic literature review.
3.1.5 Step 5: Validating the heuristics
In this step, the new set of heuristics is validated regarding effectiveness and efficiency, e.g. through a heuristic evaluation or expert opinion (Quiñones Otey, 2017). The set of heuristics has been validated by using them in a heuristic evaluation. In heuristic evaluation, the researcher uses the heuristics to evaluate whether e.g. a website or other interactive system follows guidelines for usability and design (Ding and Lin, 2010). Axis’ network management system Music was used for validating the heuristics. Two heuristic evaluations were conducted; one using the new heuristics and one using Nielsen’s set of heuristics (Nielsen, 1995). Nielsen’s heuristics are created based on years of experience in the field and proven to be capable in finding usability problems (Ding and Lin, 2010). By ensuring that the new set of heuristics is more effective in finding usability issues in network management systems than Nielsen’s heuristics, the set can be considered validated. The reason for choosing heuristic evaluation is that it is a common technique for finding usability issues in all types of web applications and interactive systems (Ding and Lin, 2010). It is a
13
quick and easy method, but is still useful in finding important problems. Heuristic evaluation is also recommended specifically for validating new heuristics (Quiñones Otey, 2017). By performing heuristic evaluation on Music, I also learned problems in the usability and design of Music at the same time as the heuristics were validated.
Heuristic evaluation is conducted by one or more usability/design professionals, who uses the heuristics as a checklist for the system (Ding and Lin, 2010). With my three year experience in usability and GUI-design from Malmö University, it can be acceptable to consider myself to have enough knowledge within these areas to conduct the heuristic evaluations of Music. Arguably, the best solution would be that several professionals who have suitable knowledge within both usability and network management should perform the heuristic evaluations. However, due to a lack of resources for scheduling such sessions, conducting the tests myself was the best way to reach finished results within the given timeframe. Also, the employees I have been in contact with at Axis have been network management professionals, but not design professionals, which is very important when assessing usability and design (Ding and Lin, 2010). Through the literature review and user interviews I have gathered knowledge about network management (and how Music works, which functions it includes etc.) which was used together with my design- and usability experience when conducting the tests. In the heuristic evaluation, Nielsen’s heuristics were used. The heuristics were used as a checklist, and Music either “passed” the heuristic or a usability problem was found. Then, the same thing was done to the new set of heuristics. Since Music is a rather small system (few functions and few tabs) the entire system was considered when assessing it instead of e.g. targeting a specific page/function at a time.
3.2 Design mock-ups
Based on the problems found in the heuristic evaluation concerning the GUI of Music, mock-ups have been created showing an alternative design for the system. The purpose of the mock-ups is to show how the problems found in the heuristic evaluation can be fixed in practice, and give Axis a suggestion of a design more in line with the usability heuristics. This gives value to Axis in the form of a new possible design with a better user experience, and it also overall shows the type of changes and results a company might achieve by testing with these usability heuristics. The design mock-ups were created with the tool “Moqups” (Moqups, 2018). They are based on screenshots from the real system, with new elements added with the Moqups-tool.
3.3 Alternative methods
One method which is very typical within usability testing is user testing (Hoonhout, Meerbeek and Buie, 2012). Including users in the process of creating/updating systems is important for any enterprise concerned with usability and a good user experience. This may rise questions as to why user testing was not chosen as the main method of this paper. User interviews were performed in order to understand network management and Axis’ system, but creating heuristics and performing heuristic evaluation is the main theme of this study. However, this does not mean that enterprises should exclude user testing or only perform heuristic evaluation. Heuristic evaluation is very useful for finding flaws in the design and usability of an interactive system (Choma, Zaina and da Silva, 2016). It is a useful beginning of usability testing. Then, if one wishes to get more detailed information regarding these issues, the problems found in the heuristic evaluation can be used to guide user tests. The user tests can be mainly focused on the big problems found in the heuristic evaluation (Choma, Zaina and da Silva, 2016). The user tests can then show what kind of
14
feelings and problems the issues rise for users or how users might want the system to work instead. Finding usability issues, e.g. through heuristic evaluation is important for knowing which aspects future user tests should be focused on (Choma, Zaina and da Silva, 2016). To conclude, user testing should not be excluded from usability testing of network management. On the contrary, it is essential. Besides user testing and expert-based evaluation methods, simulating the network and performing tests on the simulation is a method mentioned in correlation to network management (Warren, Nolte, Funk and Merrell, 2004). However, this is a very expensive and time consuming method, and therefore not appropriate for this thesis. Instead of user interviews, observations could have been conducted, were the employees could have been observed while using Music. However, observations might not have given the same knowledge about the basics of network management and the specific answers needed for this study which were gotten through the interviews.
4. Results
Based on a literature review and user interviews, heuristics have been created with the purpose of starting to fill the gap of usability methods for network management. The results from the user interviews, the creation of the heuristics and the validation (showing if the heuristics should be used for network management systems) are presented below.
4.1 User interviews
The results of the user interviews conducted at Axis shows how one example of a network management system (Axis’ system Music) is used and the network managers’ feelings and thoughts about working with the system. Regarding knowledge about using the system, three out of the four interview subjects consider themselves to be at level 4 or 5 on a scale from 1-5. One of the interview subjects stated their knowledge to be at a level of 1, the reason being them starting their employment at Axis only a month ago. The interviews show that network management system Music is used as a sort of “rulebook” for the Axis network. One of the most important tasks is giving the correct devices access to the correct networks. It is very important that no unauthorized devices enters their office networks. At the same time, authorized devices always need to be able to get the correct access quickly in order for employees to be able to continue with their work. Music is a GUI for a system where Axis can work with this authentication. There is a MAC-database, storing the MAC-address of all devices allowed to connect. These devices can then be put in different groups, and policies (rules) can be added to the groups. These policies guide which VLAN a group of devices should be able to access. What the system does is to guide the devices to different VLANs. An interview subject also discussed that the system is used when setting up new network equipment. Each time new equipment is added, it needs to be configured in Music (with policies etc.). When a new device need access, that device needs to be added in a table of devices allowed to make requests. Axis have high demands, both from the inside and outside of the company, to only let known devices connect. When a completely new office is set up, the infrastructure team makes a complete reconfiguration of Music. Music, according to one of the interview subjects, makes work more dynamic, and removes the need of manually tagging VLANs. Music can be used for managing networks for all of Axis’ offices around the world, from one place. The results of the interviews also show that there are three groups of people at Axis working with this network management system: helpdesk, IT-operations and the infrastructure team. Helpdesk is using the system for solving problems employees might have with the network, e.g. connection-problems. Helpdesk can use the system for helping the devices reach the correct VLAN. IT-operations
15
is working with network troubleshooting and maintenance of Axis’ IT-systems. When troubleshooting they can for example use Music to change policies and temporarily give authorization to devices they are using for testing. They are also solving problems which cannot be solved by helpdesk. If a problem cannot be solved by IT-operations it moves to the infrastructure team. The employees of the infrastructure team are also the ones who set up new network equipment and handle the configuration of this. All interview subjects talked about how security is a main concern. Doing the correct configurations and giving groups the correct policies (and putting devices in the correct group) is very important. Otherwise, for example a client device might end up in a server network.
Three out of the four interview subjects find the user interface of Music overall easy enough to use to achieve their daily work goals. However, one out of these three states that even though it is easy enough there is still a lot of complexity. For example, the system does not give you any hints as to what might be wrong if you for e.g. forget to add a certain group. The interview subject expresses an explicit wish that the system would show this. The reason for the complexity is, according to one interview subject, that there have not been the time or the option to develop more than what was absolutely necessary. The demands of Axis has in this case first and foremost been on the functionality, not the usability. Even though it is a complex system, it works and could therefore be considered good enough for its purpose. The fourth of the interview subjects (who did not find the system usable) claims to not have any understanding at all of how to perform their daily tasks in the system, with the reason of being newly hired. All agree that there is room for improvement. One suggestion besides showing hints to the reason of errors is clear documentation.
The interviews reveal that certain education and knowledge is needed for properly using the system. Some education in using the interface is needed according to one of the interview subjects, and all agree that a thorough knowledge of how the network at Axis is built is necessary. In order to correctly map a group to a policy it is important to know which devices should have access to what networks, otherwise a device might get access to things it should not. Such information must be remembered by the network manager. It is not easy to check which policy and group should belong together. This cannot be checked in Music, the network manager has to find the correct configuration file and find the policy there (which might not be named with a descriptive name). However, the employees state that this is quite easy to remember after working with it for a while, since there are not that many exceptions. The function of mapping groups and policies together is overall considered complex by the interviewed employees, and they think it is easy to create errors. At the same time, several of the interview subjects also consider it to be the most important functionality. Besides this, several interview subjects agree that configuration is one of the most complex tasks, one that the employees would rather avoid. Other than this, the interview subjects states that there has been a few problems with authentication (such as making the system realize that a device is indeed legitimate) and a few bugs. Several of these problems are however being worked on. Another problem mentioned by one of the interview subjects is that test environments for network management is missing in most cases. If you commit something, it is rather permanent.
4.2 Characteristics/important aspects of network
management systems
The results from the interviews were used as a help in defining what a network management system can be used for, its tasks, complex parts etc. The interview results together with the results from the systematic literature review (in section
16
2) makes it possible to characterize network management systems, its important parts and its complexities. Security is a very important aspect of network management. Authorization and policies absolutely needs to be done correctly. Despite its importance, mapping policies correctly is a function which might be very complex. Configuration (which needs to be done e.g. when new network equipment is added) is a critical part of network management and often very difficult to do. In order to use a network management tool within an enterprise you need a lot of knowledge about how that particular network is built, the different network components, network access etc. Also, a lot of this information often needs to be remembered by the network manager. Complex configurations, remembering a lot of information, and varied, complex interfaces are examples of things which might complicate the use of network management systems. Network management is overall difficult and error prone, with tasks causing strain on network managers. Errors often appear within this domain which may cause costly, high-profile incidents.
The most important aspects of network management systems, realized from the user interviews and systematic literature review, are summarized below:
Security, very important that only authorized devices are allowed Memorability
Difficult, error-prone systems Complex configurations
Important to formulate policies correctly and map them to groups of devices correctly
Interfaces for such systems need to be simple and hide complexity
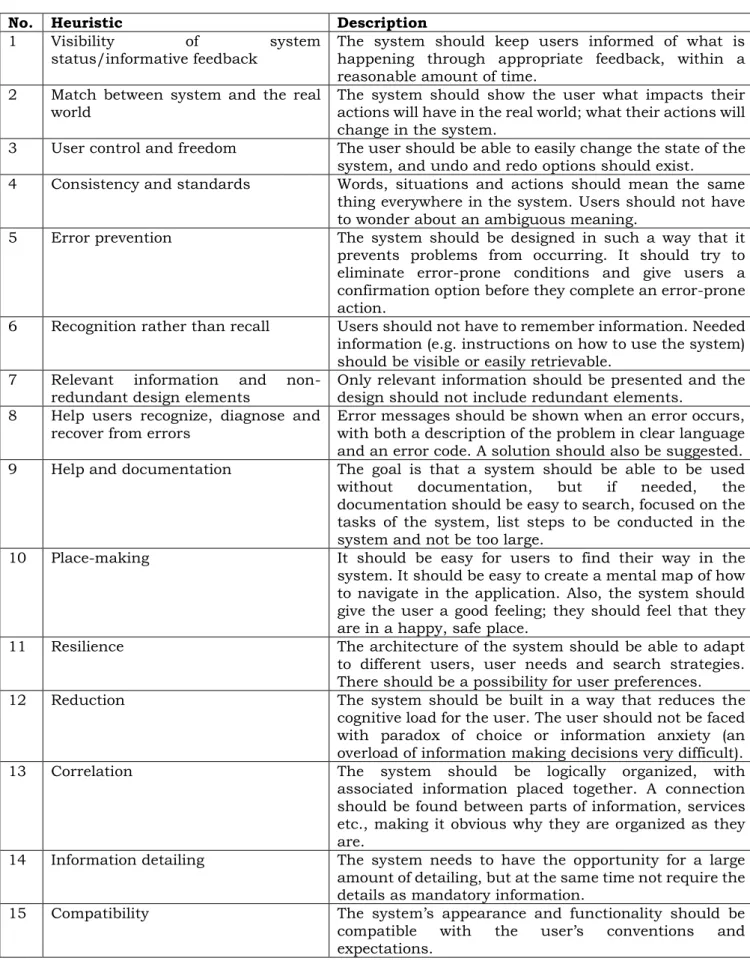
4.3 Base heuristics
In order to create the new set of heuristics, a few existing sets of heuristics were used as a base. These heuristics could then be checked against the characteristics specified in section 4.2, and either chosen or discarded for the final set. After combining the base sets and removing duplicates, the following list of base heuristics remained, written as they are named and described in their respective sources (sometimes descriptions are slightly shortened or worded slightly different, but with the same meaning). In the column on the right, each heuristic is either chosen or discarded for the final network management heuristics. In this same column there is also a description as to why the heuristic is included/not included, and if anything about the heuristic needs to be changed for network management systems.
Table 3. Base heuristics used as a starting point for the new set of heuristics.
No. Heuristic Description Chosen/discarded
1 Visibility of system status/informative feedback
The system should keep users informed of what is happening through appropriate feedback, within a reasonable amount of time.
Chosen heuristic. This can be considered relevant for all systems. Users need to understand what is happening, the impact of their actions etc.
2 Match between
system and the real world
The system should use words, phrases and concepts familiar to the user rather than system-oriented terms. It should speak
the user’s language.
Information should appear in a logical order.
Chosen heuristic. This is relevant for help in understanding the system, especially for new users. However, the heuristic description can be slightly changed. Within this field, it might be necessary to use some system-oriented terms because of the very technical work within this domain. It needs to be clear exactly which part of the technical work each task relates to.
17
But at the same time, all terms need to be easily understood in order to avoid unnecessary errors. However, this might be moved to heuristic 21 (below) about language. This heuristic (no. 2) might, in this domain, instead address the fact that it could be helpful if the system showed the user what impact their actions will have in the real world (match between system and the real world).
3 User control and
freedom
The user should be able to easily change the state of the system, and undo and redo options should exist.
Chosen heuristic. The state of different components and functionality is
important within network
management. It is also important that the user can undo a faulty action.
4 Consistency and
standards Words, situations and actions should mean the same thing everywhere in the system. Users should not have to wonder about an ambiguous meaning.
Chosen heuristic. This is important for every system in order to avoid confusion and errors.
5 Error prevention The system should be designed
in such a way that it prevents problems from occurring. It should either eliminate error-prone conditions or give users a confirmation option before they perform an error-prone action.
Chosen heuristic. This is important for all systems, and very important to focus on within network management since it is so complex and error-prone. At the same time is very important to keep the system secure. Therefore
there could be a benefit to
strengthening this heuristic even more, saying the system should both try to eliminate error-prone conditions and make the user confirm.
6 Recognition rather
than recall Users should not have to remember information. Needed information (e.g. instructions on how to use the system) should be visible or easily retrievable.
Chosen heuristic. Very important within network management since it could help in reducing errors. It also reduces confusion and gives a better user experience.
7 Flexibility and
efficiency of use
The system should contain “accelerators” – shortcuts and
effective methods which
experienced users may use. Users should be able to tailor their frequent actions.
Discarded heuristic. Shortcuts are not the most relevant part of network management. Instead, the focus should lie on creating a clear path of tasks and on the user understanding the work flow. Important parts about flexibility is better described for network management in heuristic 12.
8 Aesthetic and
minimalist design No should be shown. Rarely irrelevant information needed information should not “compete” with the important parts.
Chosen heuristic. This is a relevant heuristic for ease of use. However, a
design can sometimes be too
minimalistic and/or not contain enough information, and that also needs to be detected in the evaluation. Not enough information is a bad thing too. The name of the heuristic can be misleading since the description does not involve anything about aesthetic design. Therefore, the name could be changed to show that this heuristic is about highlighting important parts
and not showing unnecessary