Mälardalen University Press Dissertations No. 109
ON SAFE AND SECURE COMMUNICATION
IN PROCESS AUTOMATION
Johan Åkerberg 2011
School of Innovation, Design and Engineering
Mälardalen University Press Dissertations
No. 109
ON SAFE AND SECURE COMMUNICATION
IN PROCESS AUTOMATION
Johan Åkerberg
2011
Copyright © Johan Åkerberg, 2011 ISBN 978-91-7485-039-0
ISSN 1651-4238
Mälardalen University Press Dissertations No. 109
ON SAFE AND SECURE COMMUNICATION IN PROCESS AUTOMATION
Johan Åkerberg
Akademisk avhandling
som för avläggande av teknologie doktorsexamen i datavetenskap vid Akademin för innovation, design och teknik kommer att offentligen försvaras fredagen den 25 november 2011, 10.00 i Paros, Mälardalens högskola, Västerås.
Fakultetsopponent: Dr Lutz Rauchhaupt, ifak
Akademin för innovation, design och teknik Mälardalen University Press Dissertations
No. 109
ON SAFE AND SECURE COMMUNICATION IN PROCESS AUTOMATION
Johan Åkerberg
Akademisk avhandling
som för avläggande av teknologie doktorsexamen i datavetenskap vid Akademin för innovation, design och teknik kommer att offentligen försvaras fredagen den 25 november 2011, 10.00 i Paros, Mälardalens högskola, Västerås.
Fakultetsopponent: Dr Lutz Rauchhaupt, ifak
Abstract
In the process industry, network and system security have become important since the introduction of Ethernet-based fieldbus protocols. As an example, a successful attack on a power plant, supporting large cities with energy, could result in a temporal but total power loss. Such attacks could be devastating for the society. The security threats are real, and motivations for attacking industrial communication systems may be political or economical.
The visions of autonomous systems, which can be supervised, diagnosed and maintained from remote is not far from reality, but stress the need for security and safety measures. Wired fieldbus protocols are mature with respect to safety and there are existing standards for safe communication. However, the wired fieldbuses lack adequate security measures to be deployed in industrial automation. In wireless sensor networks security is addressed thoroughly in the standards, but is not mature with respect to safety. Future automation systems need ideally to seamlessly support safety and security in heterogeneous networks while hiding the complexity for the end-users in order to successfully manage large-scale industrial production.
This thesis presents one feasible solution towards safe and secure communication in heterogeneous industrial networks for process control. The presented solution addresses several other important aspects such that engineering efficiency, transparency, possibilities for retrofitting, coexistence with international standards in order to protect the return-of-investment of products, systems, and installed base within the area of process automation. Field trials show that several improvements of wireless sensor networks with respect to determinism in both the uplink and the downlink are needed. This is not only true when it comes to the research problems addressed within the scope of this thesis, but rather a necessity for market acceptance and deployment in process automation in general. The major contribution of this thesis is a method that enables end-to-end safe and secure communication in heterogeneous automation networks without major changes in existing standards, while preserving engineering and integration efficiency.
ISBN 978-91-7485-039-0 ISSN 1651-4238
List of Papers
This thesis is based on the following papers, which are referred to in the text by their Roman numerals.
I J. Åkerberg and M. Björkman, Introducing Security Modules in PROFINET IO, The 14th IEEE International Conference on Emerging
Technology and Factory Automation (ETFA), Mallorca, Spain,
September, 2009
II J. Åkerberg, M. Gidlund, T. Lennvall, J. Neander, and M. Björkman, Integration of WirelessHART Networks in Distributed Control Systems using PROFINET IO, The 8th IEEE International Conference on
Indus-trial Informatics (INDIN), Osaka, Japan, July, 2010
III J. Åkerberg, F. Reichenbach, and M. Björkman, Enabling Safety-Critical Communication using WirelessHART and PROFIsafe,
The 15th IEEE International Conference on Emerging Technology and Factory Automation (ETFA), Bilbao, Spain, September, 2010
IV J. Åkerberg, M. Gidlund, J. Neander, T. Lennvall, and M. Björkman, Deterministic Downlink Transmission in WirelessHART Networks Enabling Wireless Control Applications, The 36th Annual Conference
of the IEEE Industrial Electronics Society (IECON), Phoenix, USA,
November, 2010
V J. Åkerberg, M. Gidlund, T. Lennvall, J. Neander, and M. Björkman, Efficient Integration of Secure and Safety Critical Industrial Wireless Sensor Networks, EURASIP Journal on Wireless Communications and
Networking, September, 2011
VI J. Åkerberg, M. Gidlund, and M. Björkman, Future Research Chal-lenges of Industrial Wireless Sensor Networks, The 9th IEEE
Interna-tional Conference on Industrial Informatics (INDIN), Lisbon, Portugal,
July, 2011
Papers not Included in the Thesis
The following papers are not included in the thesis.
1. F. Barac, J. Åkerberg, and M. Gidlund, A Lightweight Routing Protocol for Industrial Wireless Sensor and Actuator Networks, The 37th Annual
Con-ference of the IEEE Industrial Electronics Society (IECON), Melbourne,
Australia, November, 2011
2. K. Yu, M. Gidlund, J. Åkerberg, and M. Björkman, Reliable and Low La-tency Transmission in Industrial Wireless Sensor Networks, The First
In-ternational Workshop on Wireless Networked Control Systems (WNCS),
Ni-agra Falls, Canada, September, 2011
3. J. Åkerberg, F. Reichenbach, M. Gidlund, and M. Björkman, Measurements on an Industrial Wireless HART Network Supporting PROFIsafe: A Case Study, The 16th IEEE International Conference on
Emerging Technology and Factory Automation (ETFA), Toulouse, France,
September, 2011
4. F. Ciccozzi, A. Cicchetti, T. Seceleanu, J. Åkerberg, J. Delsing, L.E. Carlsson, Integrating Wireless Systems into Process Industry and Business Management, The 15th IEEE International Conference on Emerging
Technology and Factory Automation (ETFA), IEEE, Bilbao, Spain,
September, 2010
5. J. Åkerberg and M. Björkman, Exploring Network Security in PROFIsafe,
The 28th International Conference on Computer Safety, Reliability and Se-curity (SAFECOMP), Hamburg, Germany, September, 2009
6. J. Åkerberg and M. Björkman, Exploring Security in PROFINET IO, The
33rd Annual IEEE International Computer Software and Applications Conference (COMPSAC), Seattle, USA, July, 2009
Abstract
In the process industry, network and system security have become important since the introduction of Ethernet-based fieldbus protocols. As an example, a successful attack on a power plant, supporting large cities with energy, could result in a temporal but total power loss. Such attacks could be devastating for the society. The security threats are real, and motivations for attacking industrial communication systems may be political or economical.
The visions of autonomous systems, which can be supervised, diagnosed and maintained from remote is not far from reality, but stress the need for se-curity and safety measures. Wired fieldbus protocols are mature with respect to safety and there are existing standards for safe communication. However, the wired fieldbuses lack adequate security measures to be deployed in indus-trial automation. In wireless sensor networks security is addressed thoroughly in the standards, but is not mature with respect to safety. Future automation systems need ideally to seamlessly support safety and security in heteroge-neous networks while hiding the complexity for the end-users in order to suc-cessfully manage large-scale industrial production.
This thesis presents one feasible solution towards safe and secure commu-nication in heterogeneous industrial networks for process control. The pre-sented solution addresses several other important aspects such that engineer-ing efficiency, transparency, possibilities for retrofittengineer-ing, coexistence with in-ternational standards in order to protect the return-of-investment of products, systems, and installed base within the area of process automation. Field trials show that several improvements of wireless sensor networks with respect to determinism in both the uplink and the downlink are needed. This is not only true when it comes to the research problems addressed within the scope of this thesis, but rather a necessity for market acceptance and deployment in process automation in general. The major contribution of this thesis is a method that enables end-to-end safe and secure communication in heterogeneous automa-tion networks without major changes in existing standards, while preserving engineering and integration efficiency.
Sammanfattning
Inom processindustrin har behovet av informations- och systemsäkerhet ökat markant sedan Ethernet-baserade fältbussprotokoll började användas i automationsutrustningar. En framgångsrik attack mot till exempel ett kraftverk som genererar elektricitet till stora städer skulle kunna resultera i ett tillfälligt och omfattande strömavbrott. Sådana attacker kan vara förödande för samhället. Hotbilden existerar och motiven för att attackera industriella kommunikationssystem kan vara såväl ekonomiska som politiska.
Visioner om autonoma system, som kan övervakas, diagnostiseras och underhållas från avlägsna platser kan snart realiseras, men kräver tillförlitliga lösningar för informations- och personsäkerhet. Trådbundna fältbussprotokoll är utvecklade med hänseende på personsäkerhet och det finns standarder för säkerhetskritisk kommunikation. De trådbundna fältbussarna saknar lösningar för informationssäkerhet som är gångbara i industriell automation. I trådlösa sensornätverk behandlas informationssäkerhet grundligt i standarderna, men lösningar saknas för personsäkerhet. Framtida automationssystem behöver stöd för informations- och personsäkerhet i heterogena nät, som samtidigt döljer komplexiteten för slutanvändarna för att framgångsrikt hantera storskalig industriell produktion.
Denna avhandling presenterar en genomförbar lösning för säker kommu-nikation i heterogena industriella nätverk för processtyrning. Den presenter-ade lösningen behandlar flera andra viktiga aspekter såsom enkelhet, effek-tivitet, dölja komplexitet, möjligheter för eftermontering och samexistens med internationella standarder för att skydda avkastning på investeringar av pro-dukter, system och installerad bas inom området processautomation. Fält-studier visar att det behövs flera förbättringar av trådlösa sensornätverk med avseende på determinism. Detta gäller inte bara inom ramen för denna avhan-dling utan är snarare en nödvändighet för att erhålla marknadsacceptans och användning inom processautomation i största allmänhet. Ett av de stora bidra-gen i denna avhandling är ett koncept som möjliggör en effektiv integration av informations- och personsäkerhet i heterogena automationsnätverk utan större förändringar av befintliga standarder.
Preface
I have many people to thank for making my industrial PhD studies and this doctoral thesis possible. It has been an intensive, educating, challenging, and stimulating journey since the summer of 2008 when it all began. First of all I would like to thank my supervisors Mats Björkman (MDH), Maria Lindén (MDH), Mikael Gidlund (ABB Corporate Research), and Kai Hansen (ABB Corporate Research) for all inspiration, encouragement and valuable discus-sions and advices.
I also have to thank Peter Löfgren, Dagfin Brodtkorb, Mirka Mikes-Lindbäck, Tomas Edström, and Helena Malmqvist from ABB Corporate Research for believing in me, and making it possible for me to start as an industrial PhD student. The work in this thesis has in part been financed by Industriforskarskolan RAP, CESAR, and TESLA.
Furthermore I have to thank all of my colleges at ABB Corporate Research for all discussions, reviewing, encouragement, support, and all the laughs. I es-pecially have to thank Tiberiu Seceleanu, Tomas Lennvall, Krister Landernäs, Jimmy Kjellsson, Dacfey Dzung, Martin Naedele, Daniel Grandin, Frank Re-ichenbach, Mikael Åkerholm, Tormod Wien, Jan Endresen, Erik Carlson, Ewa Hansen, Jonas Neander, and Pål Orten.
I dedicate this doctoral thesis to my wife Anna and my daughters Tindra and Alva.
Johan Åkerberg Västerås, September 10, 2011
Contents
Part I: Thesis 1 Introduction . . . 19 1.1 Research Problem . . . 21 1.2 Research Approach . . . 22 1.3 Thesis Outline . . . 23 2 Industrial Automation . . . 25 2.1 Automation Networks . . . 262.2 Wireless Automation Networks . . . 27
2.3 Secure Communication . . . 29
2.4 Safety Critical Communication . . . 30
2.5 Reflections on Safe versus Secure Communication . . . 33
2.6 Integration Transparency and Life Cycle Efficiency . . . 34
3 Related Work . . . 35
4 Included Papers and Their Contribution . . . 39
4.1 Paper I . . . 40 4.2 Paper II . . . 41 4.3 Paper III . . . 42 4.4 Paper IV . . . 42 4.5 Paper V . . . 43 4.6 Paper VI . . . 44 5 Conclusions . . . 47 5.1 Future Work . . . 48 6 References . . . 49
Part II: Included Papers 7 Paper I: Introducing Security Modules in PROFINET IO . . . 59
8 Paper II: Integration of WirelessHART Networks in Distributed Control Sys-tems using PROFINET IO . . . 69
9 Paper III: Enabling Safety-Critical Communication using WirelessHART and PROFIsafe . . . 77
10 Paper IV: Deterministic Downlink Transmission in WirelessHART Networks Enabling Wireless Control Applications . . . 87
11 Paper V:
Efficient Integration of Secure and Safety Critical Industrial Wireless Sensor Networks . . . 95 12 Paper VI:
Part I:
Thesis
1. Introduction
Automation is a broad area, which is commonly broken down in process automation, substation automation, factory automation, building automation, and home automation. The requirements differ in real-time performance such as, allowed jitter, cost, availability, maintainability, and also in safety and se-curity in the various automation disciplines. This thesis focuses on the process automation domain, but work already done in other domains is evaluated if it is feasible to reuse or adapt for process automation.
The importance of network- and system security are increasing in the pro-cess industry since the introduction of Ethernet-based fieldbus protocols in process automation that open up for new attack scenarios. As an example, a successful attack to a power plant [1], supporting large cities with energy, could result in a temporal but total power loss. Such attacks could be devastat-ing for the society. The security threats are real, and motivations for attackdevastat-ing industrial communication systems may be political or economical [2].
The operational requirements are different for automation and office IT. In automation the most important requirement is the safety of person, equipment, and environment. Security violations might affect the safety of the plant and its personnel. Availability, that is, to be in safe operation over long periods of time is the second most important requirement. Office IT security requirements focus on authorization, confidentiality, and integrity issues. Furthermore, it is difficult to apply IT system administration practices in automation where software-patches and rebooting are required when security vulnerabilities are identified [3].
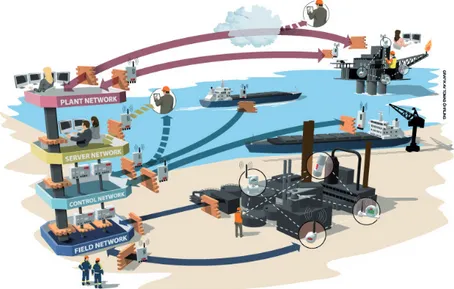
The measures against security attacks in the process automation standards are simply to keep the networks closed, i.e. no connections to the outside. If the control system must be connected to the outside, i.e. the Internet, a perimeter defense protects the entrance. On the other hand, the visions of autonomous systems, that can be followed, diagnosed and maintained from remote are not far from reality, but stress the need for security and safety so-lutions. Figure 1.1 illustrates one possible future scenario where both wired and wireless technologies are deployed on various automation network levels in order to automate distributed processes. The wired fieldbuses are mature with respect to safety and there are existing standards for safe communica-tion, for example PROFIsafe [4]. However, the wired fieldbuses lack adequate security measures to be deployed in industrial automation. In a setup like an autonomous system, or the scenario that is illustrated in Figure 1.1, which is 19
Figure 1.1: Example of a future architecture where wireless technologies are seam-lessly integrated in the automation systems on all network levels
supervised, maintained and diagnosed from remote, security measures over safe communication have to be taken into account.
IEC 62280-1 [5] deals with safety-related communication in closed trans-mission systems. PROFIsafe is based on the black channel principle from IEC 62280-1, where the standard transmission system can be used for both safety-related and non safety-safety-related messages. The main benefit with the black chan-nel principle is that the standard transmission system can be excluded from the functional safety certification. In the railway domain, especially in rail-way signaling, it is difficult, or economically infeasible, to have closed trans-mission systems. Therefore, in the railway signaling domain, where safety-relevant messages have to be transmitted on non-trusted networks, i.e. security attacks cannot be neglected, IEC 62280-2 [6] applies. IEC 62280-2 recom-mend cryptographic techniques to be used, in addition to the safety layer, to ensure integrity, authorization and confidentiality. Following the recommen-dations of IEC 62280-2, safety-relevant data is allowed to be transmitted over non-trusted networks, i.e. open networks.
The latest advancements in wireless networks, fieldbus systems and as-set management systems contribute to the efficiency of process systems [7]. Seamless horizontal and vertical integration of communication and informa-tion throughout the complete organizainforma-tions are necessary to master the com-plexities of production and business operations in process automation [7]. Us-ing Ethernet-based protocols at the fieldbus level simplifies vertical integration as the real-time protocols can co-exist with non real-time automation proto-20
cols. Vertical integration and wireless communication have unfortunately a negative effect on security, and the risks of security attacks at fieldbus level are increasing with the level of integration.
In wireless networks, security is a very important topic and is addressed thoroughly in the standards, e.g. IEEE 802.11 [8], IEEE 802.15 [9], and Wire-lessHART [10], since there is no possibility to keep the networks closed. On the other hand, safety is sparsely addressed, if at all addressed in the stan-dards. Even if safe communication is not a hard requirement today, develop-ing a certifiable safety solution would probably decrease the skepticism for wireless communication in industry. Another aspect is if you choose wireless equipment from different suppliers, one that has not addressed safety at all, the other has a safety implementation but not formally certified, which vendor would you choose? This is not only limited to safety, it is equally important with an overall security mechanism.
There is a focus to replace or complement the various fieldbuses with field-networks in the industry to gain bandwidth, functionality and flexibility dur-ing plant lifetime. As an example PROFINET IO [11] is startdur-ing to replace PROFIBUS [11] as the Ethernet successor in the process industry. Wireless communication is also possible at sensor level or even at network level, thus expanding the communication effectively into areas where wired communica-tion has challenges with respect to cost, mobility, or mechanical wear.
1.1 Research Problem
Safety of humans, environment, and property is the number one concern in large scale industrial automation. In addition, any downtime in production is typically associated with significant losses in production and economical in-come. Therefore, proper deployment of security measures plays an important role protecting both safety and the rate of production. Today’s increase of Eth-ernet and wireless communication demands more attention than previously in the area of safety and security in process automation. The problem is that, 1. security is not fully handled today in the safety certified fieldbuses. For
example the PROFIsafe [4] standard states that there are no additional security layers necessary. It tries to keep safety sub-networks as “closed systems” and protects network entries via “security boxes”. The research problem is: How can secure end-to-end fieldbus communication as well as efficient integration of security measures be developed without major changes in current standards?
2. security is well addressed and mature but safety is barely addressed at all in wireless field networks, such as WirelessHART [10] and ISA100 [12]. Ide-ally the wireless technology should be seamlessly integrated into the exist-ing automation systems and fieldbuses. The research problem is: How can safe wireless sensor networks, as well as efficient integration of wireless 21
sensor networks, be developed without major changes in existing automa-tion systems and standards?
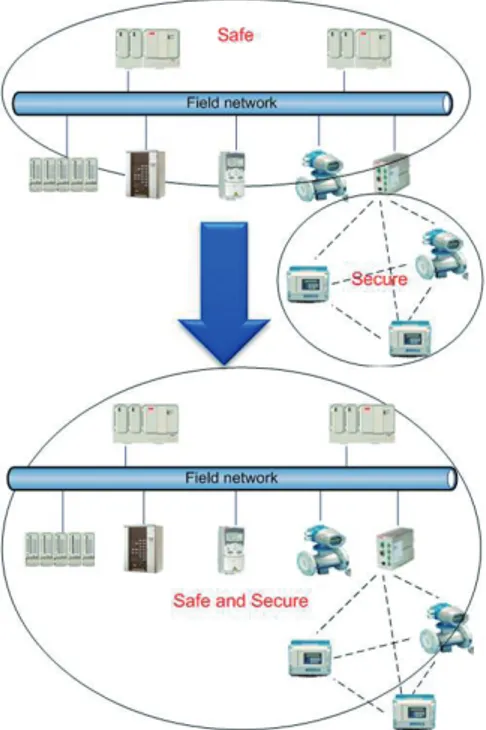
The research problem is illustrated in Figure 1.2, where ideally the hetero-geneous field networks should be both safe and secure, and not only safe or secure.
Figure 1.2: Desired future scenario, where the automation systems are both a safe and secure
1.2 Research Approach
Ideally, to protect the return of investment (ROI) on existing automation equipment, the security problem in process automation should be solved by retrofitting security without any changes with respect to infrastructure, standards, and products. Therefore, an engineering approach is taken rather than a theoretical approach in order not to develop new solutions from the beginning, but rather to improve existing solutions with respect to network security and safety. Compared to office IT, automation has different requirements with respect to security, i.e. integrity and authentication is more important compared to confidentiality. In process automation it is more important that for example a transmitted command to control a machine is 22
not tampered with, than the risk of exposing the content of the command to an adversary.
In the same way, to protect the ROI when extending existing automation equipment with wireless technologies, the existing standards, infrastructures, methods of integration, and products should ideally be unchanged while sup-porting safety. Last but not least safety and security should ideally be possible to be engineered, deployed, and maintained where needed and independently of the usage of wired or wireless communication technologies.
The work is based on an experimental approach, where initially the possibil-ities of dangerous security vulnerabilpossibil-ities are evaluated, on existing automa-tion equipment, using standardized fieldbus protocols and funcautoma-tional safety profiles such as PROFINET and PROFIsafe. The concept of Security Modules is introduced to retrofit authentication, integrity, and optionally confidential-ity. Then the concept is extended using Industrial Wireless Sensor Networks (IWSN) while supporting both functional safety and security. The major goal of this thesis is to propose solutions that can be retrofitted to existing products without major changes in the standards, with respect to functional safety and security. Proof-of-concept implementations on existing automation equipment have been used to validate and evaluate the feasibility of the solutions.
1.3 Thesis Outline
The thesis is organized in two parts. In Part I the research problems are de-scribes as well as an overview of the research areas, related work, and contri-butions. In the end of Part I conclusions and future work are presented. Part II includes six peer-review scientific papers that are published and presented in international conferences or international journals.
The rest of Part I is organized as follows.
Chapter 2: This chapter is an introduction in industrial automation,
automation networks, security, and functional safety.
Chapter 3: This chapter presents the related work.
Chapter 4: This chapter presents the included papers and the contribution of
the thesis.
Chapter 5: This chapter presents the conclusions and future work.
2. Industrial Automation
As mentioned in the introduction, automation is wide area and with differ-ent requiremdiffer-ents with respect to safety and security in the various automation disciplines. Security concerns protecting systems and devices by e.g. prevent-ing unauthorized access, or preventprevent-ing malicious people from gainprevent-ing some benefit, getting attention, or harming somebody/something. Moreover the tra-ditional definition of a safety system is to automatically bring the process into a state in which no dangers remain to human, machine and environment.
In the remainder of this section process automation is introduced, as well as some requirements that needs to be addressed in order to design systems and solutions that can be used within process automation. Some typical exam-ples of process automation industries are: pulp and paper (see Figure 2.1(a)), mining, steel, oil and gas (see Figure 2.1(b)) to mention some. The main
(a) Pulp and paper (b) Oil and gas
Figure 2.1: Examples of process automation
characteristic that groups them together is that the products are produced in a continuous manner, i.e. the oil is produced in a continuous flow. In discrete manufacturing, the products are produced in discrete steps, i.e. the products are assembled together using sub assemblies or single components. Typical examples of discrete manufacturing industries are automotive, medical, and the food industries. Discrete manufacturing relies heavily on robotics and belt conveyors for assembly, picking, welding, and palletizing. To generalize, dis-25
crete manufacturing normally have stricter requirements with respect to la-tency and real-time requirements compared to process automation. The main reason for this generalized assumption is that in order to pick, assemble, or palletize at high speed, the latency, refresh rates, and real-time requirements are stricter compared to a tank level control in process automation to achieve the required production quality. However, as always there are cases when this general assumption is not true.
In the automation domain, many different communication protocols exist on various media such as fiber, copper cables, radio, or even power-line carrier communication. Since the automation equipment ranges from high-end server hardware from the IT domain, down to small tailored embedded systems with 8 bit processors and just a few kilobytes of memory, it is a challenging task to solve all needs with one single protocol. From an automation application point of view, communication is for example used for
• interconnection of automation equipment distributed over large
geographi-cal areas
• interconnection of dedicated real-time automation systems with operator
work-places for control and supervision
• closed loop control, ranging from slow processes such as tank level control,
to fast processes such as motion control
• interlocking and control, a major part of control applications in process
control require discrete signaling. For example, a machine might have start, stop, and safety interlocks.
• monitoring and supervision, where large amount of data is transmitted and
evaluated to predict and avoid interruption of production.
In the following sections the communication architecture, protocols, as well as the state-of-the-art in security and safety will be introduced.
2.1 Automation Networks
As illustrated in Figure 1.1 the automation networks are divided into several different networks, with different demands and importance of various proper-ties. Typically, the higher levels of the automation networks, i.e. server net-works, have more relaxed constraints on for example latency and real-time properties, compared to the field networks. On the other hand, the field net-works have in general relaxed constraints with respect to throughput, as real-time behavior, low latency, and low jitter are more important for process con-trol.
On the higher levels of the automation network, Server Network in Figure 1.1, one of the most common protocols are Object Linking and Embedding (OLE) for Process Control [13], or OPC for short. Another common proto-col, mainly residing on the Control Network is the Manufacturing Message 26
Specification [14] (MMS). MMS is using TCP/IP for transportation as well as OPC. For historical reasons there exist many proprietary protocols on both the server and control network, the main reason is that the equipment on both server and control network are provided from one vendor, and the proprietary protocols remain due to backwards compatibility issues.
On the field network level, the IEC 61784-1 standard specifies 9 different communication profiles [11]. Additional protocols, based on Real-Time Eth-ernet are specified in IEC 61784-2 [15]. In Table 2.1 the protocols from IEC 61784 are listed. Many other protocols exist as well and the aim is not to make this a complete list, but an overview of the multitude of different protocols on the market. When it comes to market shares, there are two dominant protocols
Table 2.1: Standardized fieldbus protocols from IEC 61784
IEC 61784-1 IEC 61784-2 Foundation Fieldbus CIP
CIP PROFIBUS & PROFINET PROFIBUS & PROFINET P-NET
P-NET INTERBUS
WorldFIP Vnet/IP INTERBUS TCnet CC-Link EtherCAT
HART Ethernet Powerlink
SERCOS EPA
MODBUS RTPS SERCOS
namely Foundation Fieldbus (FF) and Profibus & Profinet. FF is dominant in the United States, and Profibus & Profinet are dominant in Europe. The total installed base is in order of hundred of million devices and increasing.
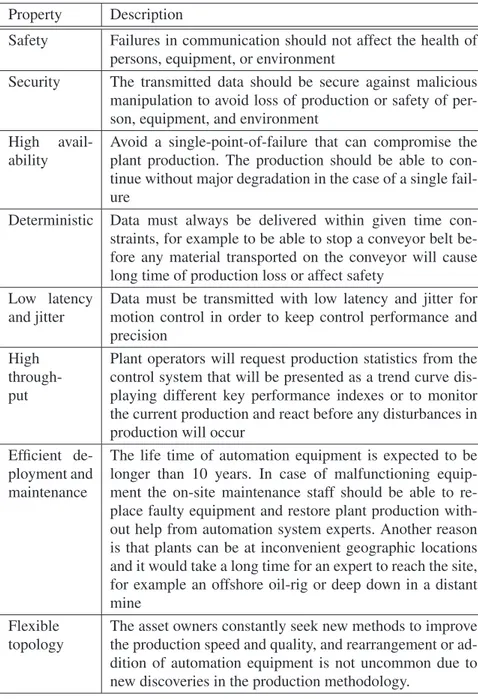
Since fieldbuses are used to transmit data for interlocking, closed-loop con-trol, and monitoring there exist several important properties. Some of the most important and sometimes even contradicting properties of industrial commu-nication at various levels are given in Table 2.2.
2.2 Wireless Automation Networks
The use of wireless technologies in automation is not something new, it has been around for quite some time. For example wireless LANs, long-haul wire-less links are commonly found in industrial automation on the higher levels in the communication architecture. It is even found on the factory floors for real-27
Table 2.2: Important properties of industrial communication
Property Description
Safety Failures in communication should not affect the health of persons, equipment, or environment
Security The transmitted data should be secure against malicious manipulation to avoid loss of production or safety of per-son, equipment, and environment
High
avail-ability Avoid a single-point-of-failure that can compromise theplant production. The production should be able to con-tinue without major degradation in the case of a single fail-ure
Deterministic Data must always be delivered within given time con-straints, for example to be able to stop a conveyor belt be-fore any material transported on the conveyor will cause long time of production loss or affect safety
Low latency
and jitter Data must be transmitted with low latency and jitter formotion control in order to keep control performance and precision
High through-put
Plant operators will request production statistics from the control system that will be presented as a trend curve dis-playing different key performance indexes or to monitor the current production and react before any disturbances in production will occur
Efficient de-ployment and maintenance
The life time of automation equipment is expected to be longer than 10 years. In case of malfunctioning equip-ment the on-site maintenance staff should be able to re-place faulty equipment and restore plant production with-out help from automation system experts. Another reason is that plants can be at inconvenient geographic locations and it would take a long time for an expert to reach the site, for example an offshore oil-rig or deep down in a distant mine
Flexible
topology The asset owners constantly seek new methods to improvethe production speed and quality, and rearrangement or ad-dition of automation equipment is not uncommon due to new discoveries in the production methodology.
time communication, where IWLAN [16] and WISA [17] have been success-fully deployed. In addition, one international and industrial standard for Wire-less Sensor Networks (WSNs) exists: WireWire-lessHART [10]. WireWire-lessHART 28
provides means to automate areas where wired fieldbuses have challenges with respect to mechanical wear and cost. ISA-100 [12] and WIA-PA [18] are possibly two emerging IEC standards, or WirelessHART, ISA-100a, and WIA-PA may merge into one industrial standard in the future. The WSNs are also deployed in the automation industries, but mainly in smaller installations, providing additional services such as condition monitoring, and monitoring of non-critical process values.
2.3 Secure Communication
For historical reasons, security has got little or no attention in the automation domain. The reason is that the automation equipment has initially been placed in a central physical location. The automation equipment, i.e. controllers, I/O, and field devices are connected in a marshaling room. The marshaling room is a central place, where all “field communication” is passing through, com-pare with old telephone systems. The communication between the controllers and operator stations were based on proprietary solutions with no connections outside the physical location, where only authorized personnel may enter. In a way, security was based on security-by-obscurity and physical security.
Over time, the demand for more information from the field equipment was necessary to refine the control algorithms and to improve the quantity and quality of the final products. The control systems went from central controllers to distributed control systems (DCS). The latest advancements in wireless technology and condition monitoring allow and demand even further verti-cal and horizontal integration, or even connections to the Internet. Since al-most 10 years ago, security in the automation domain has gained a lot of attention [19, 20] and the next paragraphs will describe the state-of-the-art in process automation.
The server network communication protocols are security aware. For exam-ple OPC relies heavily on the user configuration of the security. As OPC relies on DCOM (Distributed Component Object Model) [21] the security also re-lies on the limited set of operating systems. This problem has been solved with OPC Unified Architecture (OPC UA) that is platform independent [22]. MMS has no security countermeasures by definition, but provides mechanisms for access control.
The closer to the sensors and actuators we get, the less aware of security the protocols get. The main reason for this is due to the history of fieldbus communication and the initial proprietary protocols. As the fieldbus proto-cols have emerged to Ethernet-based communication, security is still lacking, mainly due to restricted resources and lack of feasible countermeasures to de-ploy. One exception is that wireless technologies used at fieldbus levels are already security aware, providing countermeasures for integrity, availability, and confidentiality. However, many important issues are still open with re-29
spect to integration into automation systems, and simple maintenance that is required to minimize production downtime.
To add further security countermeasures, firewalls are used to limit the com-munication to and from the server networks when connecting them to enter-prise networks or the Internet. Also VPN is used to tunnel traffic between different sites over the Internet.
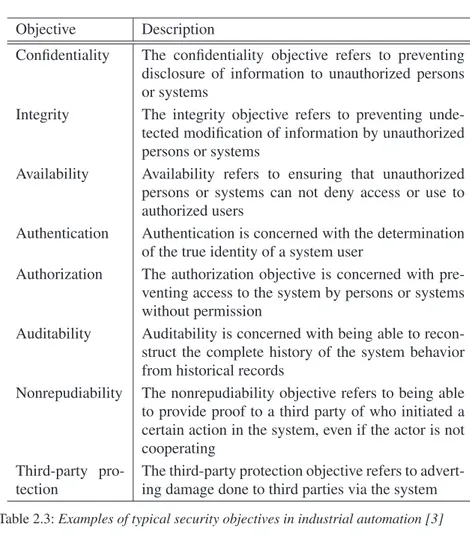
At fieldbus level, the state-of-the-art is to protect even single production cells with a dedicated network protected by a firewall [23]. With this approach each communication segment is protected by a firewall and an adversary has to penetrate several firewalls to reach the field equipment. The horizontal com-munication below a firewall is based on trust, and all nodes can communicate with each other without any restrictions. The concept of different security zones is also covered in the ANSI/ISA standards [24, 25]. ISA have ongo-ing standardization activities in the area of safety and security for industrial automation and control systems (ISA99 WG7) which at current state is not advancing [26]. Table 2.3 summarizes typical security objectives that can be used as a framework for categorizing and comparing security mechanisms amongst systems [3].
2.4 Safety Critical Communication
While secure communication has got little attention in automation in the past, safe communication has got lot of attention and is standardized and mature. However, many proprietary protocols still exist. The main reason for the pro-prietary safety protocols are that not all available safety protocols could be included in the standards. The ones that did not make it to the standard, had an installed base before the final selection for standardization and need to be maintained for years to come.
The IEC 61784-3 [27] standard specifies general rules and functional safety profiles for the fieldbus profiles specified in IEC 61158, IEC 61784-1, and IEC 61784-2 according to the general functional safety standard IEC 61508. The safety profiles specified in the IEC 61784-3 standard are all based upon the
black channel principle from the experiences from the train signaling domain,
IEC 62280-1 [5]. The principle of the black channel simplifies the overall safety certification process, as the standard transmission system does not have to be part of the safety certification, see Figure 2.2 for an illustration of the black channel. Using the black channel principle, a safety layer is added on top of the standard transmission system that will detect all errors in a deterministic way without relying on any measures of the standard transmission system.
The possible types of communication errors related to functional safety and IEC 61784-3 are presented in Table 2.4. All safety-profiles have to deploy measures to handle the possible communication errors in a deterministic way while not relying on the mechanisms in the underlying black channel. 30
Objective Description
Confidentiality The confidentiality objective refers to preventing disclosure of information to unauthorized persons or systems
Integrity The integrity objective refers to preventing unde-tected modification of information by unauthorized persons or systems
Availability Availability refers to ensuring that unauthorized persons or systems can not deny access or use to authorized users
Authentication Authentication is concerned with the determination of the true identity of a system user
Authorization The authorization objective is concerned with pre-venting access to the system by persons or systems without permission
Auditability Auditability is concerned with being able to recon-struct the complete history of the system behavior from historical records
Nonrepudiability The nonrepudiability objective refers to being able to provide proof to a third party of who initiated a certain action in the system, even if the actor is not cooperating
Third-party
pro-tection The third-party protection objective refers to advert-ing damage done to third parties via the system
Table 2.3: Examples of typical security objectives in industrial automation [3]
Figure 2.2: Using the black channel principle to avoid functional safety certification of the standard transmission system
Table 2.4: Possible communication errors from IEC 61784 [27]
Error Description
Corruption Messages may be corrupted due to errors within a bus par-ticipant, due to errors on the transmission medium, or due to message interference
Unintended
repetition Due to an error, fault, or interference, old not updated mes-sages are repeated at an incorrect point in time Incorrect
se-quence Due to an error, fault, or interference, the predefined se-quence associated with messages from a particular source is incorrect
Loss Due to an error, fault, or interference, a message is not re-ceived or not acknowledged
Unacceptable
delay Messages may be delayed beyond their permitted arrivaltime window, for example due to errors in the transmission medium, congested transmission lines, interference, or due to bus participants sending messages in such manner that services are delayed or denied
Insertion Due to a fault or interference, a message is inserted that relates to an unexpected or unknown source entity
Masquerade Due to a fault or interference, a message is inserted that re-lates to an apparently valid source entity, so a non-safety relevant message may be received by a safety relevant par-ticipant, which then treats it as safety relevant
Addressing Due to a fault or interference, a safety relevant message is sent to the wrong safety relevant participant, which then treats reception as correct
Several standardized safety profiles are specified in IEC 61784-3. The dif-ferent fieldbuses and their safety profiles are listed in Table 2.5. In addition,
Table 2.5: Standardized safety profiles
IEC 61784-1 IEC 61784-3 Foundation Fieldbus FF-SIS
CIP CIP-Safety
PROFIBUS & PROFINET PROFIsafe
INTERBUS INTERBUS Safety
several proprietary safety protocols exist as well, but these are not consid-ered here. With respect to market market shares Fieldbus Foundation Safety 32
Instrumented Systems (FF-SIS) and PROFIsafe dominates the market with a installed base in order of millions of devices.
2.5 Reflections on Safe versus Secure Communication
In the development and design of safety-critical systems all possible error cases which can lead to a dangerous situation are identified in a structured way before the system is put into service. The design and development of se-cure systems are executed in a similar way. Even if it is extremely difficult or practically impossible to design a 100% safe system today, the identified risks are not changing over time as the IEC 61508 life-cycle model covers the complete life-cycle of the safety-critical system from initial design to de-commissioning and disposal. In security the risks will change over time, for example if a weakness in a specific crypographic algorithm is discovered, the security countermeasure might not be sufficient any longer. In safety-critical systems the manufacturer can specify under what circumstances and opera-tional conditions the system can be used. It is not that simple to specify that a security countermeasure should not be broken or weakened by adversaries.To generalize, the main difference between safe and secure communication is the use of Cyclic Redundancy Checksums (CRC) or cryptographic check-sums (MAC or Message Integrity Code, MIC) [28]. The CRCs are designed to detect unexpected and randomized transmission errors and are not strong enough to withstand intentional misuse by adversaries. However, the MAC and MIC protecting the payload data units are designed to make it trouble-some for an adversary to change the payload without any detection by the communicating peers. Thus the MAC and MIC are based upon the use of pre-shared secret keys, while the CRC does not rely on any secret keys.
There are many commonalities and differences with safe and secure com-munication. However, some of the measures taken in the safety protocols can be exchanged with countermeasures from the security domain to make it more difficult for an adversary to manipulate the payload without detection [28]. In the work of Novak et al. [28] the IEC 61508 life-cycle model is extended with security related phases in the life-cycle model to address both safety and security.
Security countermeasures can also be used as safety measures. The sand-boxing technique from the security domain could be used to isolate safety-related applications from errors caused by other (non) safety-safety-related applica-tions. Using sandboxing would increase the confidence of programming lan-guages such as assembler, C, and C++ in safety-critical systems, instead of recommending for example ADA for mission-critical safety systems [29, 30].
2.6 Integration Transparency and Life Cycle Efficiency
Since the life-time of automation systems and equipment can be more that 20 years, engineering efficiency and maintenance are key factors in industrial au-tomation. Further complexity is added due to the fact that there are few green field installations today in countries with an high level of automation. In those countries, continuous upgrades and improvements are conducted and a mul-titude of different automation systems cooperate in order to fully automate the processes. It is not uncommon that you find automation systems that were installed as state-of-the-art since the 80’s fully cooperating with more recent technologies. In order for the asset owners to be productive and adaptive to recent process optimizations, maintenance, technologies, the automation sys-tems must hide as much complexity and technology dependent engineering as possible. This is also true with respect to current state-of-the-art, as the plant operators might not know, or even care, if a field device for instance is communicating wirelessly. The same goes for the maintenance personnel, it is challenging to keep up with the old installed base, and new technologies should ideally not be different from an engineering and maintenance perspec-tive.With this in mind, retrofitting security and safety is a must in order to protect the return-of-investment. This means that, from a technology point of view, the most recent or best technologies are not necessarily the best choice. Rather a selection of technologies and techniques that are possible to retrofit as well as perform well in the future is desired. In other words, a migration plan is the most desired solution.
3. Related Work
There exist a lot of work for security within the IT domain while security for industrial automation has been a white spot for a long time but now it has started to gain more attention in both academia and industry [31]. Dzung
et al. present a comprehensive article about relevant specifications and
stan-dards for industrial automation which serves as a good introduction to the area [3]. Savola presents an overview of challenges of information security management in a modern industrial automation environment and concluded that the main challenges comes from the diffusion of new ICT technology [32]. Reinelt et al. give an overview for security relevant considerations and also propose a first approach for a structured methodology to classify com-munications to be able to deduce security-relevant use cases and proper meth-ods [33]. Naedele points out the expectations that various stakeholders have regarding initiatives to standardize information system security for industrial plants [34]. In particular, a deeper investigation of ISA SP99, NERC CIP and IEC TC65 [35] was done and the conclusion was that each of the particular standardization bodies only matches a subset of stakeholders. Furthermore, Naedele addresses the key challenges commonly mentioned in the context of control system security (also referred to as “SCADA security”) and dis-cusses feasible solutions to most of them [36]. In addition, that article argues that the main obstacle to control system security is not technical, but rather financial. Tretyl et al. analyze the situation of security measures for indus-trial fieldbus systems and proposed some simple enhancements for IP-based fieldbus systems [37]. Schwaiger and Sauter discuss the increased security threat with gateway interconnections between fieldbus systems and IP-based local area networks (LANs) [38]. They propose two different ways to apply appropriate authentication and encryption mechanisms. Schwaiger and Tretyl implement security systems using a smart card by using a LonWorks field-bus system targeting energy metering, security and safety systems, home au-tomation and remote control of critical infrastructure [39]. Nevertheless, their approach may lead to a new fieldbus system that supports the conceived secu-rity services. Object linking and embedding for process control (OPC) unified architecture (OPC UA) is a software interface specification and application framework based on web service for plant automation systems which com-municate with each other over Internet. Renjie et al. analyze the security envi-ronment and requirements for OPC. Furthermore, they presented an improved security model for OPC UA systems [40]. Recently, industrial wireless sen-35
sor networks (IWSN) has gained a lot of attention and is starting to get de-ployed in process automation. This may lead to a potential security problem and in [41], the authors made an experimental study on intrusion detection methods for IWSN and proposed a hierarchical framework for intrusion de-tection. Recently a lot of attention has been into security and safety within building automation and control system (BACS). In the work of Novak et
al. [28] the use of MACs, cryptographic checksums, are evaluated with respect
to building automation. Both the increase of bandwidth utilization and other typical run-time figures for different security algorithms are presented. The main concerns are that security countermeasures add too much computational resources and network bandwidth utilization in a typical building automation node without use of hardware acceleration. Novak and Gerstinger present a common approach on how to engineer a safety and security related building automation technology [42]. Granzer et al. present a security threat analysis and identifies the main challenges of providing security in building automa-tion [43]. The weakest point of encrypautoma-tion and cryptographic checksums are normally not the algorithms themselves, but the way the “secret keys” are dis-tributed, since the keys have to be exchanged at some point in time and might be exposed. Implementation of such key distribution schemes are a bigger challenge than to find resources for the execution of the security algorithms. One such key distribution scheme has been presented for building automation by Granzer et al. [44]. Moreover, to eliminate a single point of failure in that infrastructure, a redundancy concept featuring multiple key servers was pre-sented. Some methods and attempts to attack industrial automation systems are reported. Baud and Felser try different methods to attack PROFINET IO nodes but their attempts were unsuccessful. However, it was stated that if stan-dard Ethernet switches are used, it should be possible to deploy a successful man-in-the-middle attack, where an attacker can get in a position between the nodes, relaying and manipulating messages [45]. A Denial-of-Service (DoS) attack, draining network and CPU resources to reduce the availability or deny service completely, is a non-trivial security threat that cannot be prevented with cryptography. A generic approach how to deal with DoS attacks in au-tomation systems is presented by Granzer et al. [46].
The security threats to automation systems have been researched, and exist-ing IT security solutions for use in automation networks [3, 37, 47] have been evaluated as well. In the work of Dzung et al. [3] and Treytl et al. [37] exist-ing security protocols, such as Transport Layer Security (TLS) [48], Secure Sockets Layer (SSL) [49] and IPsec, are evaluated for use in the automation domain. A Virtual Automation Network (VAN) [50–53] is a heterogeneous network consisting of wired and wireless LANs, the Internet and wired and/or wireless communication systems. The aim of VANs is to transfer data through a heterogeneous network, through an end-to-end communication path, in the context of automation application. VAN is not a new set of protocols; it aims at reusing as much as possible from the LAN, Wide Area Network (WAN) 36
and industrial communication. From substation automation, the Generic Ob-ject Oriented Substation Event (GOOSE) [54, 55] protocol from IEC 61850 can be extended with security countermeasures [56]. The Substation Configu-ration Language (SCL) file has to be extended to hold, for example, the serial number of the certificate to be used. The real-time Ethernet frames are pro-tected by a MAC, a RSA signed message digest, and optionally the payload is encrypted. This standard is currently being reworked as it is economically infeasible to apply RSA on real-time communication on intelligent electrical devices that communicate on millisecond basis. The state-of-the-art in au-tomation security is to use perimeter defenses, i.e. firewalls, to restrict in-coming and outgoing traffic to the networks. Firewalls can be deployed be-tween different automation cells, i.e. server, control, and fieldbus networks, and even protect a single automation cell with a dedicated firewall [23]. Func-tionality provided by using Ethernet technology at field device level, such as web services (HTTP) [57], file transfer (FTP) [58], and network manage-ment (SNMP) [59] can be enabled on Ethernet cards by uploading modified firmware [60]. Peck et al. [60] discusses possible scenarios and threats to Su-pervisory Control And Data Acquisition (SCADA) systems by utilizing the firmware upload vulnerability found on the Ethernet card.
Wireless extensions of automation networks and fieldbuses have been re-searched in different forms. Willig et al. discuss many issues and solutions related to wireless fieldbus systems [61]. In [62], Gungor and Hancke present the state-of-the-art of industrial wireless sensor networks and open research issues. In [63], Vitturi et al. present results from an experimental evaluation using experimental industrial application layer protocol on wireless systems. In [64], Ishii presents results on multiple backbone routers to enhance relia-bility on wireless systems for industrial automation. In [65], Haehniche and Rauchhaupt present radio channel characteristics and the R-Fieldbus approach for industrial environments and applications. In [66], Miorandi and Vitturi an-alyzed the possibilities of implementing Profibus DP on hybrid wired/wireless networks, based on Ethernet and Bluetooth, respectively. In [67], Rauchhaupt presents the RFieldbus system architecture that supports real-time wireless communication based on PROFIBUS DP. In [68], Sousa and Ferreira discuss and describe the role of simulation tools in order to validate wireless sions of the Profibus protocol. Other related research work on wireless exten-sions for traditional Profibus can be found in [17, 69–74]. Recently, Wireless HART has received a lot of attention in both academia and industrial automa-tion. In [75], Lennvall et al. present a performance comparison between the
Wireless HART and ZigBee standards. Their conclusion is that ZigBee is not
suitable for wireless industrial applications due to poor performance, and se-curity is optional while in the Wireless HART standard it is mandatory. Se-curity in industrial wireless sensor networks have been heavily discussed and in [76], Raza et al. present a security analysis of the Wireless HART proto-col against well known threats in the wireless media. Wireless HART has also 37
been considered for control applications in process automation [77]. In [78], Nixon et al. present an approach to meet the control performance requirements using a wireless mesh network (e.g., WirelessHART). Their main conclusion is that device and network operation must be synchronized. In [79,80], Taylor
et al. present a safe communication scheme for wireless networked control
systems, that monitors the control performance and communication metrics and opens a closed-loop in case of control performance degradation.
Functional safety and communication in open transmission systems have been laid down in IEC 62280-2 [6], and Deuter et al. address this in their work with Virtual Automation Networks (VAN) [81]. Industrial WLAN (IWLAN) can be used to extend Ethernet networks tunneling PROFIsafe in safety-critical applications [16]. In [82], Trikaliotis and Gnad evaluate different mapping solutions for Wireless HART integration. There are ongoing standardization activities for integrating Wireless HART devices into Profibus/Profinet networks within Profibus International [83] and wireless cooperation team [84]. However, the main difference is that we include safety and security that is not considered for standardization so far.
In safe and secure communication there are commonalities and differences. Some of the measures taken in the safety protocols can be exchanged with countermeasures from the security domain to make it more difficult for an adversary to manipulate the payload without detection [28]. In the work of Novak et al. [28] the IEC 61508 life-cycle model is extended with security related phases in the life-cycle model to address both safety and security. A similar approach of combining security and safety in development of medical devices is presented by Zafar et al. [85].
4. Included Papers and Their
Contribution
The first paper presents the concept of security modules to ensure integrity and authentication of real-time messages in PROFINET IO. The concept of security modules is introduced towards a solution for secure real-time com-munication using PROFINET IO and can be retrofitted without any major changes in the standards.
In Paper II, we address and propose a method how to integrate and main-tain Wireless HART into distributed control systems using PROFINET IO. The proof-of-concept implementation of the proposed method shows that it is possible to download configuration to all Wireless HART components as well as process controller configuration using existing central engineering tools. Thus the end-users do not need any additional tool-specific training, as exist-ing tools are reused for Wireless HART. In addition, maintenance is greatly simplified as the actual configuration of Wireless HART devices will be auto-matically downloaded by the distributed control system when faulty devices are replaced.
Paper III, extends Paper B by introducing a method to integrate, config-ure, and tunnel the functional safety profile PROFIsafe to the Wireless HART devices, to achieve safe communication between a DCS and Wireless HART devices. A proof-of-concept implementation is presented that shows that the method is possible to deploy using existing products and standards.
In Paper IV we point out that the current Wireless HART standards lacks support of actuators, which plays an important role in automation. We pro-pose periodic and deterministic downlink functionality to Wireless HART, as well as a method to integrate fail-safe states of actuators. A fail-safe state (normally closed/off) is of outmost importance even if the application is not safety-critical by definition, as actuators cannot remain in their last position in case of communication failures. We define new HART commands extending the interface without affecting available services, to support the integration of actuators.
Paper V combines the results from Paper I-IV towards an efficient integra-tion method of safe and secure Industrial Wireless Sensor Networks. Further-more, we analyze and improve the Safety Function Response Time utilizing the proposed methods from Paper IV.
Finally, Paper VI summarizes gaps and future research challenges identified throughout the work in Paper A-E that could not be covered within the scope of this thesis.
4.1 Paper I
J. Åkerberg and M. Björkman, Introducing Security Modules in PROFINET IO, The 14th IEEE International Conference on Emerging Technology and
Factory Automation (ETFA), Mallorca, Spain, September, 2009
Short Summary. In this paper we show that it is possible to retrofit a security layer on top of PROFINET IO without changing the underlying transmission system or standards. By introducing security modules, end-to-end network se-curity can be achieved and ensure authentication, integrity and confidentiality for real-time communication.
The concept of security modules is a flexible framework and countermea-sures can be changed, as security threats and exploits are changing over time. A proof-of-concept implementation shows that it is possible to implement se-curity modules on existing products in order to secure them against, for exam-ple, man-in-the-middle attacks.
Process data transmitted on the fieldbus level normally contain a limited set of information, i.e. sensor readings and set points for actuators along with some measurements. Protecting the integrity of process data requires rela-tively large cryptographic checksums in addition to the process data. How-ever, in most of the cases the net increase of bandwidth utilization is zero, as the minimum allowed packet size on Ethernet is 64 bytes and the padding is replaced by security relevant information.
Contribution. The main contributions in this paper are summarized as fol-lows:
• It is shown that the concept of security modules can be implemented in
existing products to retrofit security in PROFINET IO without violating the standards
• It is shown that the concept of security modules prevents
man-in-the-middle attacks on PROFINET IO.
Author’s Contribution. The author proposed and implemented the security modules to retrofit security in PROFINET IO. Furthermore, the author evalu-ated security modules implementation with industrial automation equipment and wrote most of the text for the paper. The concept of security modules is based on the same idea as PROFIsafe, where a safety layer is put on top of the transmission system. This approach was mentioned by Treytl et al. in a larger context and it was stated that this approach could cause problems with interoperability with the underlying fieldbus systems [47].
4.2 Paper II
J. Åkerberg, M. Gidlund, T. Lennvall, J. Neander, and M. Björkman, Inte-gration of WirelessHART Networks in Distributed Control Systems using PROFINET IO, The 8th IEEE International Conference on Industrial
Infor-matics (INDIN), Osaka, Japan, July, 2010
Short Summary. In this paper we describe a method to integrate WirelessHART networks in Distributed Control Systems (DCS) using PROFINET IO. By modeling the WirelessHART network in the Generic Station Description file, that describes a PROFINET IO device, the WirelessHART related configuration can be distributed from the central engineering stations. In this way, both process controller configuration and WirelessHART network configuration is engineered and maintained from a central location. Thus the end-user does not need any additional tool-specific training, as the existing tools are used to engineer the WirelessHART networks. We base the method of integration on the keywords simple deployment and maintenance, and flexible topology.
A proof-of-concept implementation of the proposed method shows that it is possible to download WirelessHART configuration both to the Wire-lessHART network managers, as well as the WireWire-lessHART sensors. By inte-grating WirelessHART in this way, maintenance is greatly simplified as the ac-tual configuration will be downloaded automatically by the DCS when faulty field devices are replaced.
Contribution. The main contributions in this paper are summarized as fol-lows:
• An integration method for WirelessHART networks in distributed control
systems using PROFINET IO. Our proposed concept provides connectiv-ity between the wireless sensor network and the fieldbus network. Further-more it reduces the need of application specific configuration in the Wire-lessHART gateway.
• Our proposed method uses user-friendly tag names, that are already used
in the DCS, instead of network addresses. In addition the mapping between WirelessHART and PROFINET is automatic.
• Our proposed method do not need a WEB server in the WirelessHART
gateway to enable configuration and maintenance which is common in all available solutions today. Another advantage with our solution is that the end-user do not need any additional tool-specific training.
• A proof-of-concept implementation is done and shows that our proposed
solution works in a real scenario. We show that it is possible to download WirelessHART configuration, including security configuration, to both the WirelessHART network manager as well as to the WirelessHART sensors.
Author’s Contribution. The author proposed and implemented the integration method for WirelessHART in a distributed control system using PROFINET IO. Furthermore, the author wrote most of the paper.
4.3 Paper III
J. Åkerberg, F. Reichenbach, and M. Björkman, Enabling Safety-Critical Communication using WirelessHART and PROFIsafe, The 15th IEEE
International Conference on Emerging Technology and Factory Automation (ETFA), Bilbao, Spain, September, 2010
Short Summary. Two major trends can be recognized in industrial automa-tion. One of them is that Ethernet is replacing traditional fieldbus networks continuously, because it combines flexibility, reliability, and introduces fast data rates, which allow beside others quality of services. This is pushed even further when field devices use wireless communication to connect to the con-trol system. Beside that another trend is seen in functional safety due to rising customer demands and evolving regulations in industry. That leads necessar-ily to a consolidation of both technologies, where safety must be guaranteed in the same manner over wireless channels as it is handled over Ethernet.
This paper addresses safety issues emerging when PROFIsafe, as one of various safety protocols on the market, is used on top of a black channel layer, that is comprized of non-safe protocols including WirelessHART.
Contribution. The main contributions in this paper are summarized as fol-lows:
• We show that it is principally possible to enable safety-critical
communica-tion with a combinacommunica-tion of WirelessHART, PROFINET IO, and PROFIsafe.
• An integration method enabling that safety-related configuration is
down-loaded from the control system to the WirelessHART device.
• A proof-of-concept implementation based on industrial products shows
that this can be realized without changing fundamental control engineer-ing practices.
Author’s Contribution. The author proposed and implemented the inte-gration method enabling safety-critical communication using WirelessHART, PROFINET IO, and PROFIsafe. Furthermore, the author implemented the proof-of-concept demonstrator and wrote most of the paper.
4.4 Paper IV
J. Åkerberg, M. Gidlund, J. Neander, T. Lennvall, and M. Björkman, Deter-ministic Downlink Transmission in WirelessHART Networks Enabling Wire-42
less Control Applications, The 36th Annual Conference of the IEEE Industrial
Electronics Society (IECON), Phoenix, USA, November, 2010
Short Summary. Wireless sensor and actuator networks bring many bene-fits to industrial automation systems. However, unreliable wireless and multi-hop communication among sensors and actuators cause challenges in design-ing such systems. Wireless HART is the first standard for wireless real-time industrial applications. However, current Wireless HART standard does not provide services for efficient usage of actuators, which are an essential part of automation. In this paper we focus on Wireless HART and propose a pe-riodic and deterministic downlink transmission functionality which enables efficient usage of actuators and control applications. Furthermore, we define new HART commands extending the interface, without affecting available ser-vices, to support the integration of actuators. This can be achieved with minor changes in the current standard.
Contribution. The main contributions in this paper are summarized as fol-lows:
• We propose a new service called periodic downlink transmission for
Wireless HART, that enables periodic and deterministic transmissions from gateway to Wireless HART actuators.
• We define a new set of HART commands extending the interface, without
affecting available services.
• We propose a mechanism to utilize the deterministic properties of the
downlink transmission to discover errors in a control loop enabling actuators to transit into a failsafe mode.
• We show that our proposed deterministic downlink transmission scheme
integrates well into PROFINET IO.
Author’s Contribution. The author identified the lack of periodic downlink transmission for Wireless HART and proposed the method to extend the Wire-less HART standard. Furthermore, the author demonstrated that the proposed deterministic downlink transmission scheme integrates well into PROFINET IO and wrote most of the paper.
4.5 Paper V
J. Åkerberg, M. Gidlund, T. Lennvall, J. Neander, and M. Björkman, Efficient Integration of Secure and Safety Critical Industrial Wireless Sensor Networks,
EURASIP Journal on Wireless Communications and Networking, September,
2011
Short Summary. Wireless communication has gained more interest in in-dustrial automation due to flexibility, mobility, and cost reduction. Wireless systems, in general, require additional and different engineering and mainte-43
![Table 2.4: Possible communication errors from IEC 61784 [27]](https://thumb-eu.123doks.com/thumbv2/5dokorg/4938387.135918/34.718.95.581.90.605/table-possible-communication-errors-from-iec.webp)