MÄLARDALEN UNIVERSITY
SCHOOL OF INNOVATION, DESIGN AND ENGINEERING
VÄSTERÅS, SWEDEN
Thesis for the Degree of Bachelor of Science in Engineering - Computer Network
Engineering 15.0 hp
D
ETECTION AND
I
SOLATION OF A
R
OGUE
A
CCESS
P
OINT
Christina Ampatzi
cai18001@student.mdh.se
Examiner:
Hossein Fotouhi
Mälardalens Högskola, Västerås, Sverige
Supervisor: Iliar Rabet
Mälardalens Högskola, Västerås, Sverige
Date
26-05-2021
2
Abstract
Software-defined networking (SDN) is a technology that was developed a decade ago and has become a pole of attraction for researchers due to its unique ability to distinguish the control plane from the data plane on network devices. With SDN, network security has the potential to evolve to a great extent. Many companies, large and small, are threatened by attacks with the ultimate goal of the attacker’s personal gain. One way for outsiders to enter is through Rogue Access Points (RAPs). RAPs are malicious devices that are connected to the network and provide wireless connection to unauthorized devices. The presented thesis looks into different methods for detecting and isolating a RAP from the network with SDN architectures. The implementation of this system is developed in a platform called Mininet-WiFi that simulates heterogeneous types of networks. A topology is created on Mininet-WiFi that includes ten hosts, an OpenFlow switch, a ryuretic controller and a RAP. The thesis aims to detect and block a rogue device in an SDN network, and three algorithms are developed to achieve the main goal of this thesis. The results show that the detection and isolation algorithms work successfully. This can be understood because illegitimate users cannot ping the legitimate network users. In addition, the scalability and reliability of the network is being tested by increasing the number of users.
3
Table of Contents
1.
Introduction………. 5
2.
Background………. 6
2.1.RAP... 6 2.2.Software-defined networking (SDN) ... 6 2.2.1.SDN Controller ... 8 2.2.2.SDN Switch ... 8 2.2.3.OpenFlow ... 8 2.3.Ryuretic Controller ... 9 2.4.Network virtualization ... 10 2.5.Mininet-WiFi ... 103.
Related Work……….. 11
4.
Problem Formulation………. 12
5.
Method………. 13
5.1.Case Study... 13 5.2.Experiment ... 136.
Ethical and Societal Considerations………... 14
7.
Experimental setup……….. 15
7.1.Virtual Machine ... 15
7.2.Installation of Mininet-WiFi ... 15
7.3.Programming the topology ... 16
7.4.Configuration of a Ryu controller ... 17
4
7.4.2.Multi-MAC Check ... 19
7.4.3.TTA Analysis ... 20
8.
Results……….. 21
8.1.Detection and isolation of a RAP ... 21
8.2.Scalability ... 22
9.
Discussion……… 24
10.
Conclusions……….. 26
11.
Future Work……… 27
5
1. Introduction
Nowadays, when computers and computer science are making great progress, wireless networking and wireless communication have made the lives of people who use it easier. People with bad intentions take advantage of such technologies. These people, also known as attackers or outsiders, usually have excellent knowledge on network security and how they can overcome the firewalls of a network. One device that many attackers use to access a network is through a RAP which is an unauthorized device that is connected to a network’s device. Studies have shown that almost 20% of corporations had at one point an active RAP in their network [1].
The aim of the thesis is to create a system that detects and isolates rogue devices from a network. The detection and isolation of such a device in this thesis is performed on an SDN-based network. One may wonder why use an SDN-based network? The answer is that traditional networks do not have much as flexibility as an SDN-based network has, furthermore changes in the software are not done quickly in a traditional network [2]. As opposed to an SDN based network where the network administrator can change the software according to a company’s needs at any time. To experiment with such a network, a platform called mininet-WiFi is used to simulate SDN networks. There are studies that have been carried out with the aim of isolating attackers from networks [3]. These studies have shown that SDN networks in combination with the software they used carried out their research.
The purpose of the work is to create an SDN network on the mininet-WiFi platform and with the help of a controller to detect and isolate a malicious device from the network. This is achieved by developing software and applying different rules for detecting an attacker and then blocking the attacker from the network. The combination of SDN with emulator tools has become a big draw for many researchers and several studies have been conducted on these technologies for the same or similar purpose.
6
2. Background
This section describes the different technologies that are used in this project, their purpose and how they function.
2.1. RAP
A Rogue Access Point (RAP) is an unauthorized AP which is directly connected to a network device and its purpose is to fool other devices into believing that it is a legitimate access point (AP) [4]. A RAP poses a threat to a private network; it is usually plugged in a network without authorization, often by an employee or an outsider, also known as a network attacker. A RAP poses a serious network security threat because it can provide a wireless backdoor into a network for outsiders. Once a RAP is up and running the unauthorized individual can bypass the network firewalls and other security devices which can lead to the network being open for attacks.
2.2. Software-defined networking (SDN)
Software-defined networking (SDN) is a relatively new paradigm for communication networks and its architecture separates the control plane from the data plane where the control is handled by the SDN controller [5]. SDN virtualizes the network and provides us with higher levels of visibility and control. SDN enables the separation of the control management plane of network devices from the data plane where the traffic flows. It has a controller running with specialized software that manages all network traffic. SDN detects and blocks security threats as well as it can detect a network anomaly before entering a network. Figure 1 depicts the difference between a traditional network and an SDN network.
Figure 1: Traditional network versus SDN [6]
7
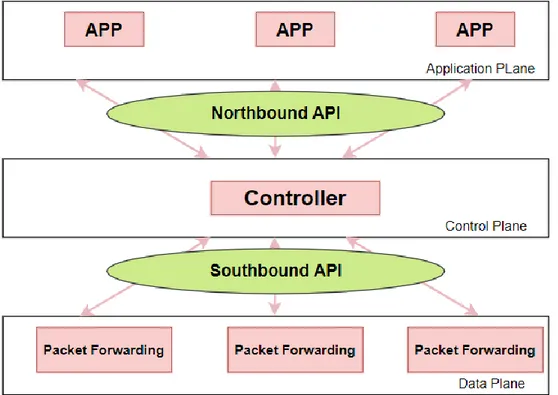
SDN consist of the following three elements [7]:1.
Controller: A SDN controller is an application that is responsible for managing the flow controlof the network. It runs on a server and it is responsible for directing the traffic to the switch.
2.
Southbound API: A southbound API enables the communication between the controller and theother network devices, such as switches, APs, routers.
3.
Northbound API: A northbound API enables the network functions which are based on theinformation between the controller and the applications.
Figure 2 represents the SDN architecture and how the controller interacts with the different APIs.
8
2.2.1. SDN Controller
The main purpose of an SDN controller is to control and manage the traffic flow of devices on a network [9]. The controller controls the traffic to improve the performance of a network application. The controller runs on a server and according to the configured protocols it directs the switches to forward the packets to their destination. Although there are different controllers with different properties the basic features are the same, for example the collection of information and the monitoring of the network topology.
2.2.2. SDN Switch
SDN switches are responsible for receiving, processing, and forwarding the packets to their destination [10]. The best known and most widely used protocol in SDN switches is OpenFlow. Each SDN switch has ports and tables. Ports are responsible for receiving and transferring packets while tables are responsible for lookups and for packet forwarding.
2.2.3. OpenFlow
OpenFlow is a communication protocol that provides access to the data plane of a network’s switches and routers [11]. The OpenFlow protocol is layered on top of the Transmission Control Protocol (TCP) and describes the use of Transport Layer Security (TLS). OpenFlow is the southbound API which is responsible for enabling the communication between the controller and the other network devices.
OpenFlow controller is a type of SDN controller that uses the OpenFlow protocol and is responsible for determining the behavior of network switches. OpenFlow allows the controller to determine the path of the packets. Regarding OpenFlow controllers there is a choice of programming language with Java and Python being the most popular. There are many types of OpenFlow controllers like NOX, POX, Trema, Ryu, Beacon etc. [12].
OpenFlow switches consist of ports, OpenFlow channel and OpenFlow tables. The connection between controller and switch is accomplished through an OpenFlow channel [11]. The function of a traditional switch is to switch packets based on the MAC address, to forward packets but also route the packets based on the TCP/IP protocol. In an OpenFlow switch the forwarding is based on flows which consist of a packet sequence which obey certain specifications. Figure 3 depicts the different architectures of an OpenFlow switch and a traditional switch.
9
Figure 3: Difference between an SND switch and a traditional switch [13]
2.3. Ryuretic Controller
The controller determines the traffic and the flow of packets and it also gives instructions on how the traffic will be transferred from device to device. In addition, it is used to communicate with an OpenFlow switch through the southbound interface [14]. There is a wide range of controllers available, in this project a Ryu controller is used. Ryu is a programming framework that allows network operators to develop SDN environments. A feature of the Ryu controller is that it supports all versions of OpenFlow, and a network operator can interact with layers 2, 3 and 4 of the OSI model.
During the programming of the controller, the Ryuretic coupler is used which is responsible for translating the instructions it receives from multiple modules and then forwarding them to the controller via the northbound interface [14]. These modules are created by the network operator and then integrated into the OpenFlow switch via the Ryu coupler. Finally, when the controller receives the instructions, it forwards them through the southbound interface to update the flow table of the switch.
Once the
Ryu controller is configured the rules that have been applied are activated to the switch via the Ryu coupler.10
2.4. Network virtualization
Network visualization is the approach of a real network and allows the support of multiple networks [15]. Network infrastructure offers opportunities for experimentation in order to create and control new protocols that will then be implemented in real networks. Network visualization enables the creation and coexistence of multiple heterogeneous architectural networks on one platform. The advantage of visualizing networks over a real network is that it offers the same services as a real network.In addition, the use of real network devices such as computers, routers, switches and even cables are financially burdensome for the user. Τhe purchase and maintenance of equipment can significantly affect the scaling of a network. Ιn a real network the change of any topology takes time and may presuppose additional equipment purchase in contrast to the visualization of networks where changes in the topologies are made easily, quickly and without any financial burden.
SDN combined with network visualization allows the user to create and experiment while writing a software program. With the help of the software the user can create topologies according to the needs of the experiment. In general, the use of SDN together with the OpenFlow protocol in combination with network visualization offers results for bandwidth limits, areas of failover, emergency flow cache, port enumeration and many other analytics data [15].
2.5. Mininet-WiFi
Mininet-WiFi is an extension of Mininet, it is a technology created by Ramon Fontes and Christian Rothenberg and it grants permission for creating and testing networks that support SDN [16]. Mininet-WiFi can emulate networks and perform experiments on these networks giving the impression that a real network has been implemented. Mininet-WiFi is supported by the Linux Ubuntu distributed system. Mininet-WiFi is a widely known and useful tool for researchers since it is possible to create heterogenous environments that are designed based on the needs of each individual user. The devices that can be used are virtual stations, hosts, switches, links and OpenFlow controllers.
Mininet-WiFi is an experimental platform that facilitates its users since a network can be created at any time without any additional devices other than a computer [16]. Additionally, Mininet-WiFi networks can run real software and network protocol codes to evaluate the performance of the devices and signal as well as test various protocols. What makes the Mininet-WiFi special is that the devices in an environment can be connected wirelessly. Various propagations of radio signals are supported and allow its users to test and calculate the mobility of the nodes and the signal propagation. In this project the default propagation model is used which is Log-Distance Propagation Loss Model. The communication between wireless stations and AP is achieved through the network interface, in which a 6-byte MAC address is stored. Network topology is created with scripts that run on the terminal of the device which are written in Python.
11
3. Related Work
SDN has attracted the attention and interest of many researchers in recent years. A large number of studies have been conducted on top of SDN technology. One of the many platforms used to simulate experimental SDN networks is with Mininet-WiFi. A simulator is a tool that helps a user to create an environment that mimics the configurations and software of a real device [17]. Unlike emulators which duplicated the hardware and the software of a device. The properties that are being offered by SDN in combination with network visualization attracted researchers since the creation of heterogeneous topologies and the number of experiments is endless.
The purpose of the paper that was written by Cox et al. [2] is to discover and block a rogue AP by taking advantage of SDN. The network topology was created on Mininet Wi-Fi. In the topology the authors used a Ryu controller and OpenFlow switch which has six host directly connected to the switch and two RAPs that are connected to the switch with wires. The controller is connected to the switch and it works as the brain of the network, all decisions are made by the controller which is configured with a software program written in Python. The purpose of the controller is to control, admit or reject incoming traffic to the network. This implementation uses various types of methods to detect and isolate a rogue access point. Among the techniques port inspecting and inner packet spacing is used which controls ingress and egress traffic over time to detect patterns. To discover and deny a malicious device they used an implementation called NFG (Network Flow Guard) which offers both passive and active measures to detect and isolate RAPs.
The thesis was implemented with the emulator Mininet-WiFi in a linear topology [2]. Wireless clients, who are being referred to as stations, communicate with an AP through a wireless interface of each station by authentication and association process. In Linux systems the wireless drivers communicate with the wireless APs through cfg80211. Stations and APs communicate with the device drive though cfg 80211.
Cfg80211 provides communication between stations and mac80211.
Both works have some similarities in the task, approach, and methodology that is used [2]. The main goal of the projects is to detect and isolate an attacker from a network. Another similarity is that both my experiment and the author's experiment is tested on miminet-WiFi. SDN technology is used to detect an attacker. Finally, the test bed of my work includes more hosts. With that said the scalability is increased which also includes higher delays.
12
4. Problem Formulation
The digital world we live in stores and transmits more and more data than ever before, which places great emphasis on network security. Wireless communication has simplified our everyday lives however our private data is transferred that can affect the owner and can jeopardize its privacy if confidential data falls into the hands of an unauthorized person. A hacker possesses expertise in networking and together with various techniques, such a person can intrude into a network in any way and damage it or extract information from it. Hackers can access the user's computer system though an access point which leads to gaining access to the user's private information. But how do these hackers manage to get into a network? Well, rogue access points can pose DHCP server attack, ARP poisoning, DoS attack etc. With these kinds of attacks, a hacker can learn useful information in order to access a network.
During a normal Wi-Fi connection, an individual's device associates with a legitimate access point, once an individual's device connects to a malicious access point the attack has occurred and that could result in catastrophic results. In this work, I am going to create a network with both wired and wireless stations, and this will be achieved with the help of a mininet-Wifi, which is also a SDN network simulator, by adding virtualized Wi-Fi stations and access points. In the mininet-WiFi simulator, a script is required to create a network topology and a set of rules is also required in order to discover and isolate a rogue access point. The goal of this thesis is to experiment with a network that is configured in Mininet-WiFi and take advantage of the SDN technology and apply rules to the controller in order to detect and isolate a rogue access point. A topology with both wired clients is used to test the reliability of the system.The controller will act as the brain of the network and it will determine how the network traffic will flow as well as if the OpenFlow switch will accept or reject the traffic. The thesis focuses on the security of a network and how outsiders can access a network and how the system can detect an anomaly on the network. More specifically the core of the thesis will be the detection and isolation of a rogue access point from a network. The following questions will be the main core of the thesis:
● How can a rogue access point be detected from a SDN system? ● What rules have been applied to discover a rogue access point?
13
5. Method
The methods for the execution of his project are divided into two separate methods. These methods are case study and experiment.
5.1. Case Study
The work required a study by reading scientific articles to gather knowledge about the tools that are used in order to create and implement a network topology and create a controller. Information about the tools and specifically Mininet-WiFi and SDN is collected from a book and well-known databases like IEEEXplore. The reason why a case study is required is because of the lack of knowledge as well as the inexperience of these technologies. The study has given me a deeper understanding of Mininet-WiFi and SDN.
5.2. Experiment
In order to test and be able to answer the questions, an experiment study is required. After the case study, I moved on to the next phase, the experiment phase. In order to answer the questions above, a network topology is configured and is tested in practice. Mininet-WiFi allows us to add wireless devices in and to emulate the attributes of a mobile station such as position and movement relative to the access points. In the Mininet simulator a software is required to create a network topology and a set of rules is also required in order to discover a rogue access point. The software is written in Python programming language. The configuration of the software is available online however it requires some modification before being implemented since the software was written six years ago [18]. The test bed consists of software files that create a topology, the interface of the controller and the rules that have been applied to identify a rogue access point. Once the script is completed and working, the measurements and results are gathered to examine if the network can detect and isolate a rogue access point.
14
6. Ethical and Societal Considerations
Rapid and quick developments in research and experiments often bring to the surface ethical and social issues such as the misuse of results that could affect the protection of personal data. Network security and especially wireless network security should be handled with great caution by the network administrator. With that said, personal data shall be carried out with a professional ethical mindset. Personal data protection refers to the protection of privacy and especially in relation to new technologies that can spread sensitive information. The main purpose of the thesis is to protect the private and confidential information of a network. It is well known that many attackers try to gather useful information for their own benefit, several times attackers achieve their goal and other times not.
My thesis is tested and implemented on a VM which will later be discarded from the system. Confidential and private data are not used in this project. However, if this project was implemented in a real environment all confidential information should remain private. Finally, the outcome of my work cannot affect any vital information and with that in mind there cannot be any ethical and societal considerations.
15
7. Experimental setup
This section provides all the needed information for a reader to understand the workflow and execution steps that were taken to complete the work.
7.1. Virtual Machine
The initial step for this work was to install a VM so that I can download and run Linux Ubuntu system. Since I own a remote computer that runs windows a VM is necessary to proceed with the rest of the project.
7.2. Installation of Mininet-WiFi
After the installation of the VM with the Linux system I proceeded to the installation of mininet-WiFi. There are several ways in which the installation of mininet-WiFi can be performed. The choice I chose was to install it directly from the source. The execution was completed in a machine terminal with the following command:
christina@christina-VirtualBox:~$ git clone
https://github.com/intrig-unicamp/mininet-wifi
This process is called cloning where all the information is copied from an application program or object and then is installed on the computer [19]. Mininet-WiFi is a repository available on GitHub, cloning is achieved from the GitHub page. After executing the command above another command is executed, according to the needs of the user, for the installation of the mininet-WiFi.
christina@christinaVirtualBox:~/mininetwifi$ sudo util/install.sh -Wnfvl Install.sh options: -W: wireless dependencies -n: mininet dependencies -f: OpenFlow -v: OpenvSwitch -l: wmediumd
16
7.3. Programming the topology
To create a topology to the platform of Mininet-WiFi a Python file was used. This file includes an access point, three wireless stations, ten hosts, an OpenFlow switch and a Ryu controller. The Mininet network is isolated from the internet and LAN and that is why it is common to use NAT to connect to the local network [16]. Without the default gateway in a Mininet-WiFi environment it is impossible to have communication between two wireless stations. In this case the access point has three interfaces operating in master mode i.e., this mode works as an access point for them.The interfaces of the stations operate as managed mode, and it is the corresponding mode for the clients. In case a default gateway is not configured it is not possible for these stations to communicate with each other even if they belong to the same network subnet. Figure 4 illustrates a virtual reflection from the current topology used for this project.
Figure 4: Topology of the network
As it can be seen from the picture above there are 10 hosts which are wired connected to the OpenFlow switch. The 10 hosts represent the authorized and legitimate clients of the network as opposed to the stations which operate as unauthorized users. RAP is a device that tries to connect to the LAN, and it has 3 wireless stations connected to the device. As mentioned previously the controller is the operator of the ingress and egress traffic and it determines the way and the order in which the packets move in the network.
To create the topology the following commands were used on the script. In figure 5 there is an example of the configuration of a host, in figure 6 configuration of a rogue AP can be seen and in figure 7 there is an example of the configuration of a station.
17
To create a host, an IP address, a MAC address and a default route are required. The creation of the RAP includes a ssid, a wireless mode, a channel, a position, and a radio range. Finally, to configure a wireless station an IP address, a MAC address, a default route and position are required since the station is wireless.
7.4. Configuration of a Ryu controller
As previously explained an OpenFlow controller is a type of SDN controller that uses the OpenFlow protocol which allows controllers to determine the path of packets. In this project a Ryu controller is used. There are three approaches to locating a rogue device: server-side, client-side, and hybrid-side.
The main focus of interest at this project is exclusively the hybrid-side approach, this means that the main goal is to investigate how a server and a client can detect and isolate a rogue device from the rest of the network. Many studies have shown that passive techniques applied to SDN prevent attacks such as ARP poisoning, DDOS, rogue DHCP server etc. [2]. Three algorithms are used to detect a malicious device in this project. Both active and passive detection methods are used: Multi-MAC/IP, TTL (time-to-live) check, and TCP- TTA (time-to-ACK).
One of the hosts is chosen to act as a trusted agent and work together with the controller to successfully block RAPs. The purpose of the trusted agent is to inspect suspected traffic and perfume some active tests. For instance, if the TTA algorithm flags a port then the traffic is redirected to the trusted agent and it drops the suspicious traffic. Multi-MAC/IP, TTL check algorithms do not redirect the traffic to the trusted agent.
18
7.4.1. TTL Check
TTL check is part of the property of the system for detecting a rogue device. TTL value is a numeric amount where TTL calculates how many hops a packet has traversed [20]. TTL field value is found in the packet header and with each hop that the packet makes its lifetime is reduced by one. If TTL becomes 0 the packet is dropped and an ICMP error message is sent to the source router.
Small networks that own routers that have only one processor to forward packets in conjunction with the TTL expiration propose attack risk, and more specifically DDoS attack [21]. When the attacker sends packets where the TTL value in the IP header is 0 then the router that receives these packets shall drop the packets. In case this does not happen, the packets will float in the network unnecessarily and that could cause traffic overload.
When an IP packet is detected the packet and more specifically the TTL value of the packet is checked, and the value should be either 64 or 128. In case the TTL value has been decremented by one unit or more then the SDN controller marks the port as a flagged which is blocked immediately from the rest of the network, this means that it cannot send or receive packets from this port. In case an aspiring hacker manipulates the TTL value before it is sent to SDN then the detection of RAP cannot be detected by this algorithm. The creation and implementation of 3 different and independent methods increases the probabilities of detecting a RAP. Figure 5 demonstrates the configuration of TTL check. In the topology created for this project all users who are directly connected to the switch are legitimate and the TTL value will not decrease for these users since the switch is the first hop for IP packets. As shown in Figure 4 the RAP device is connected to the switch and in order for the unauthorized users to reach the network will have to cross two hops, which means that the TTL value will be reduced by 1 since the IP packets will reach the RAP and finally the switch. When the IP packets with the reduced TTL value are detected by the switch they are rejected because of the configuration shown in Figure 5 and therefore this port is automatically blocked.
19
7.4.2. Multi-MAC Check
This algorithm controls the number of MAC and IP addresses on each port of the switch. In case the number of MAC / IP addresses exceeds, within a certain period of time (60 sec.), the system assumes that it is an attacker trying to invade the network with the same MAC or IP address of a legitimate user. The purpose of the algorithm is to prevent attackers who try to invade the network by obtaining access through a bridged laptop. All legitimate users are directly connected to the switch ports and thus the MAC and IP addresses do not change. Address information related to ports is stored in a table. If a wireless user attempts to enter the network with the same MAC, the IP address of another legitimate user then the packages are dropped. The appearance of a second MAC or IP address in a switch port triggers the Multi-MAC/IP algorithm and the port is marked as flagged. Once the port is flagged the client’s traffic is blocked and the attacker is isolated from the network.
20
7.4.3. TTA Analysis
The third and last algorithm used in this project is time-to-acknowledge (TTA). Property of this algorithm is to check the time a client sends TCP-ACK message for the communication that has taken place. This happens by calculating the round trip-time (RTT) of the three-way-handshake of TCP connection establishment [22]. It is worthwhile to mention that the time for a wireless client to send an ACK exceeds 1ms while for wired clients it takes less than 1ms [16]. The configuration for this algorithm has been implemented in the ports of the switch rather than the IP address. To rephrase it TTA analysis is configured at each switch port and it is calculated, because an IP address could be spoofed.
Figure 7: TCP three-way-handshake
To work in practice, the TTA analysis algorithm creates a state table, and it records all TCP connections from the hosts that are connected to the switch. The three-way-handshake process is illustrated in Figure 7. When a TCP connection is established the client sends a SYN message, from the moment the server receives the SYN message and sends back the SYN-ACK the timestamps are recorded. The different timestamps are recorded, and they are controlled by the Ryu controller. When the recording has completed then the state table with the TCP connection from a port is removed from the table. This method does not isolate an attacker from the network. If the RTT of a certain host takes more than 1ms then the Ryu redirects the traffic to the trusted agent and the packet is dropped.
Finally, it is noteworthy to mention that the TTA algorithm works on networks where all clients are directly connected to the switch. In case there are wireless legitimate clients the TTA algorithm will drop all packages from the wireless client.
22
8. Results
This section contains the collected data of how the methods that are used in this work can actually detect and isolate an attacker from the network. Section 8.1 describes the results and shows the system fulfills its requirements and section 8.2.
8.1. Detection and isolation of a RAP
As previously mentioned, the authorized and legitimate clients of the network are 10. One RAP device which is connected to the OpenFlow switch and has three wireless clients. Unfortunately, due to the complexity of the controller the system does not work exactly as it should. However, the system can detect and block access for outsiders. In case the system worked as it should the results would be different; the results would contain detailed data on how each algorithm works. Commands like ping, iperf and curl would have been used to examine the reliability of each algorithm. By using the ping command, it would have been clear that the delays between the RAP and the legitimate hosts are different and that is why the access for the malicious users is denied.
The purpose of the network is for unauthorized stations to be able to connect to the Internet but not be able to communicate with the legitimate hosts. However as shown in Figure 8 RAP can connect to the network but its wireless clients cannot connect to the Internet as shown in Figure 9.
Figure 8: RAP can successfully connect to Internet.
Figure 9: Unauthorized station cannot connect to Internet.
Nonetheless as shown in Figure 10 the station (sta5) cannot communicate with the host (h1) because the controller detects suspicious traffic, the traffic is then forwarded to the trusted agent. More detailed, the TTL value of the RAP device has decremented, which is why the packet is dropped immediately. The trusted agent examines the IP header of the packets and it decides to drop the packets.
23
8.2 Scalability
To test the reliability of the system but also the scalability of the network initially five hosts were created and then increased by five until they finally reached twenty hosts in total. The system has shown that it can respond to the increase in hosts without affecting its functionality and reliability. With the ping command that was used, four shapes can be seen and how the respond delay increases as the number of the devices increases. As it can be seen in Figure 11 to14 the delay increases as more hosts are added to the network. 50 ICMP packets were sent from each host to nat and their respond time in milliseconds. Figure 15 shows that the attacker cannot reach host20.
Figure 11: Delay for five hosts Figure 12: Delay from ten hosts
Figure 13: Delay from fifteen hosts Figure 14: Delay from twenty hosts
24
The iperf command is used to prove that the TTA detection algorithm can actually detect a suspected RAP.
iperf is a command-line tool that measures the maximum network throughput [23]. Τhe process is similar
to the one performed before. The command was executed on each host and client and the destination was the gateway router. To examine if the controller is reliable the number of hosts is increased. I first measured the throughput and later I configured the new hosts. The figures 16-19 below depict the results obtained from every port, on hosts and stations and their respond time in milliseconds.
Figure 16: h1-h5 and sta4-sta6 Figure 17: h1-h10 and sta4-sta6
Figure 18: h1-h15 and sta4-sta6 Figure 19: h1-h20 and sta4-sta6
It is obvious from the results that the hosts have a lower throughput in contrast to the stations. The throughput of the stations is greater than the limit and for this reason the packets are rejected due to the TTA-analysis algorithm that has been implemented to the system. Specifically, the controller redirects the traffic to the trusted agent, who in turn rejects the packets. It is worth noting that this method does not block the port where the traffic came from, it just drops the packages.
From the results it is understood that throughput decreases as the number of clients increases. However, this does not affect the efficiency of the system, the stations are not able to communicate with the hosts.
25
9. Discussion
The following section is based on the results that were collected in this thesis; conclusions can be made in relation to the research questions.
• How can a rogue access point be detected from a SDN system?
SDN is a very useful tool for researchers that separates the control plane from the data plane, and it also allows network administrators to handle the flow of packets. Southbound interface (SBI) is also responsible for the traffic forwarding control according to the requirements and needs that are applied by the network administrator. Controller’s decisions about network flow are announced and forwarded by the SBI. These decisions are related to the network topology, the determination of traffic flows and the implementation of the requests. Northbound interface (NBI) is responsible for the communication between the application plane and control plane. In addition, NBI is used to implement and develop management applications and monitor network traffic. A great advantage of NBI is that it can easily be modified using programming languages like Java, Python, C++, etc.
SDN architecture and its properties in conjunction with the three algorithms that have been applied to this project can successfully detect and isolate a rogue device from the network. Unfortunately, due to the complexity of the controller programming the wireless router (RAP) that was created does not fully meet all its properties. Although the wireless stations cannot communicate with the legitimate hosts, they should have internet connection. If the stations did have internet connection, then I would be able to compare the different timestamps, by using the commands iperf, between the hosts and the stations. With that said I would be able to prove that TTA is a reliable method for detecting and isolating an attacker. Additionally, if the RAP functioned properly, using the iperf command again, I could compare the time it takes for a legitimate port to perform TCP three-way-handshake and the duration of a port connected to the RAP.
• What rules have been applied to discover a rogue access point?
For this project 3 rules have been applied: TTL-check, Multi-MAC/IP-check, and TCP time-to-acknowledge analysis. TTL and Multi-MAC/IP control the received packets in the port of the switch where the destiny of the packet is determined. TTL-check calculates the TTL value of the packet and if the value has been decremented the packet is dropped. Multi-MAC/IP-check algorithm inspects if more than one MAC or IP address has been detected in the port for a certain time interval. If one of these algorithms detects a suspicious activity the port is flagged and the port is isolated from the network. Last but not least TCP time-to-acknowledge analysis inspects the timestamps of TCP three-way-handshake. If the port is flagged by the TTA algorithm, then the port is redirected to the trusted agent for more detection. Other related works have used various methods to detect a malicious device, one of these methods is a method called whitelist/blacklist. A whitelist is a list that contains information for devices that have the authority to connect to the network. When a NAT or AP is not on the whitelist the device is flagged as a RAP and it is immediately blocked from the network.
26
• How can a rogue access point (RAP) be isolated from the rest of the network?
Detecting a rogue device is not enough to protect the network, blocking this device is necessary if we want to secure the network to the maximum. Three algorithms have been implemented in the network for the purpose of discovering an attacker however only two of them can actually isolate an attacker. These two algorithms are TTL-check and Multi-MAC/IP-check. When one of these methods detects a suspicious activity the port in which the strange activity was detected is excluded from the rest of the network. Τhis way the system prevents possible breach of personal data and information leakage.
27
10. Conclusions
The fundamental objective of this thesis is the detection of a RAP device and its isolation from the network; this is achieved by using a SDN approach. Three different detection methods have been developed but only two out of three can isolate an attacker. Specifically, the algorithms that detect and isolate a rogue device are TTL-check and Multi-MAC/IP-check, while the algorithm that only detects an attacker is TTA analysis. Algorithms control the flow of packets that arrive in the ports of an OpenFlow based switch. The implementation includes ten legitimate hosts directly connected to the OpenFlow switch, a rogue access point with three wireless stations and a Ryu controller is included. The SDN controller is the control layer which creates and has a complete picture of the network topology. This feature allows easy access and testing of new services in the network topology, without requiring reprogramming of network devices and without any risk to existing services. Communication between the SDN controller and the control and data layer can be achieved using the OpenFlow protocol.
Τhe network system was created on a simulator called Mininet-WiFi. With the simulator we can have wireless and wired devices such as stations and access points, these devices were used for testing the reliability of the system to detect and exclude a rogue device. Network data is collected through various mechanisms including an agent to monitor and record network traffic.
In conclusion, topology design can affect the reliability of the algorithms. The topology design is very important for the operation of the system, a single hop or a star network topology is required in order for the system to work. The proposed solutions are effective for detecting and isolating RAPs in such topologies. In topologies that are more complicated with wireless devices the system will not be able to fulfill its functions. In order for the algorithms to work properly, the topology must have all the clients directly connected to the switch. Although algorithms can successfully detect and isolate a RAP each algorithm has its limitations. The three algorithms are independent of each and thus increase the chances of locating a RAP.
29
11. Future Work
The main goal of this work is to detect and isolate rogue devices on SDNs, even though the methods that are used can successfully achieve their purpose this project focuses only on the server-side. For future work it would be interesting to use other approaches to detect and isolate RAPs, for example client-side or even a hybrid approach. Nevertheless, this project has its legitimate clients directly connected to the OpenFlow switch, we should take into consideration how a RAP could be detected and isolated if the legitimate clients are wirelessly connected to the network.
30
12. References
[1] S. Vanjale and P. B. Mane, ”“A novel approach for elimination of rogue access point in wireless network,” in Proc. Annu. IEEE India Conf. (INDICON), Pune, India, 2014.
[2] Jacob H, Cox; Russell Clark and Henry Owen, ”Leveraging SDN and WebRTC for Rogue Access Point Security,” i IEEE TRANSACTIONS ON NETWORK AND SERVICE MANAGEMENT, VOL. 14, NO. 3, Sept. 2017.
[3]” What is Software-Defined Networking (SDN)?,” IBM, 2021. [Online]. Available: https://www.ibm.com/services/network/sdn-versus-traditional-networking. [Accessed 20 May 2021]. [4]” Rogue Access Points Explained,” IT.EXPLAINED, 2021. [Online]. Available: http://www.it-explained.com/words/rogue-access-points-explained-explained. [Accessed 23 March 2021].
[5] ”What is SDN,” Ciena, 2021. [Online]. Available: https://www.ciena.com/insights/what-is/What-Is-SDN.html . [Accessed 23 March 2021].
[6] A. Maleki, M. M. Hossain, J. Georges, E. Rondeau and T. Divoux, ”An SDN Perspective to Mitigate the Energy Consumption of Core Networks – GEANT2,” International SEEDS Conference, 2017.
[7] ”What is Software-defined networking?,” Cisco, 2021. [Online]. Available:
https://www.cisco.com/c/en/us/solutions/software-defined-networking/overview.html?dtid=osscdc000283 . [Accessed 23 March 2021].
[8] W. Jianqing, H. Yan, H. Xin, T. Qin and K. Jiaming , ”A Study on the Dependability of Software Defined Networks,” International Conference on Materials Engineering and Information Technology, P.R. China, 2015.
[9] D. Tatang, F. Quinkert, C. Röpke and T. Holz, ”SDN-Guard: Protecting SDN controllers against SDN rootkits,” 2017 IEEE Conference on Network Function Virtualization and Software Defined Networks
(NFV-SDN), Berlin, Germany, 2017
[10] P. Peresıni, M. Kuzniar and D. Kostic, ”What You Need to Know About SDN Flow Tables,” i In:
Mirkovic J., Liu Y. (eds) Passive and Active Measurement. Lecture Notes in Computer Science, vol 8995,
Springer, Cham, 2015.
[11] K. Benton, L. Jean Camp and C. Small, ”OpenFlow vulnerability assessment,” In Proceedings of the
second ACM SIGCOMM workshop on Hot topics in software defined networking (HotSDN '13). Association for Computing Machinery, Hong Kong, China, 2013.
[12] ”List of SDN controller software,” Wikipedia, 6 April 2021. [Online]. Available: https://en.wikipedia.org/wiki/List_of_SDN_controller_software. [Accessed 4 May 2021].
31
[13] Quora, [Online]. Available:
https://www.google.com/search?q=difference+between+openflow+switch+and+traditional+switch&sxsrf =ALeKk023MOjpadRbprBOAs3ApHB7aTg51A:1620550626494&source=lnms&tbm=isch&sa=X&ved
=2ahUKEwix1LrDnbzwAhXitYsKHSIFC-IQ_AUoAXoECAEQAw&biw=1536&bih=722#imgrc=7UkT_EkpI. [Accessed 25 April 2021].
[14] Henry L. Owen, Russell J. Clarky, Sean Donovan and Jacob H. Cox, ”Ryuretic: A modular framework for Ryu,” IEEE Military Communications Conference, Baltimore, MD, USA, MILCOM 2016 - 2016, pp. 1065-1070.
[15] Masayoshi Kobayashi, Srini Seetharaman, Guru Parulkar, Guido Appenzeller, Joseph Little, Johan van Reijendam, Paul Weissmann and Nick McKeown, ”Maturing of OpenFlow and Software-defined Networking through deployments,” Computer Networks Volume 61, Pages 151-175, 14 March 2014. [16] Ramon Fontes och Christian Rothenberg, Wireless Network Emulator with Mininet-WiFi, Campinas, Brazil: Christian Rothenberg, 2019.
[17] ”Simulators vs. Emulators: What’s the Difference, Anyway?,” SAUCELABS, 18 Dec 2018. [Online]. Available: https://saucelabs.com/blog/simulators-vs-emulators-whats-the-difference-anyway. [Använd 15 May 2021].
[18] J. Cox, ”Network Flow Guard (NFG) for Rogue Access Point (RAP),” 2016. [Online]. Available: https://github.com/Ryuretic/RAP .
[19] ”Cloning,” technopedia, 2021. [Online]. Available:
https://www.techopedia.com/definition/31923/cloning-programming. [Accessed 20 April 2021].
[20] ”Disabling Normal TTL Decrementing,” Juniper Networks, 23 Dec. 2019. [Online]. Available: https://www.juniper.net/documentation/en_US/junos/topics/usage-guidelines/mpls-disabling-normal-ttl-decrementing.html . [Accessed 3 May 2021].
[21] Y.-T. Han, N.-S. Ko, M.-G. Kim and H.-S. Park, ”Vulnerability of small networks for the TTL expiry DDoS attack,” 2012 Computing, Communications and Applications Conference, Hong Kong, China, 11-13 Jan. 2012.
[22] [Online]. Available: https://www.juniper.net/documentation/en_US/junos/topics/usage-guidelines/mpls-disabling-normal-ttl-decrementing.html [Accessed 4 May 2021].
[23] Dave R.,“Network Throughput Testing with iPerf”, linode 7 Oct. 2020, [Online]. Available:
https://www.linode.com/docs/guides/install-iperf-to-diagnose-network-speed-in-linux/ [Accessed 4 May
![Figure 1: Traditional network versus SDN [6]](https://thumb-eu.123doks.com/thumbv2/5dokorg/4444608.107747/6.918.126.759.642.884/figure-traditional-network-versus-sdn.webp)
![Figure 3: Difference between an SND switch and a traditional switch [13]](https://thumb-eu.123doks.com/thumbv2/5dokorg/4444608.107747/9.918.107.761.111.489/figure-difference-snd-switch-traditional-switch.webp)




